- Apr 25, 2013
- 5,355
- Content source
- http://news.drweb.com/show/?i=7047&lng=en&c=5
Autumn 2014 proved to be rich in malware targeting gamers. In September, Doctor Web issued a report about Trojan.SteamBurglar.1 which had been stealing valuable Game assets from Dota 2 users. Apparently, the criminals decided to take things further. Doctor Web's virus analysts have examined a new malware sample with very similar features which has been dubbed Trojan.SteamLogger.1. This program targets fans of several popular multiplayer games.
It can steal game assets from Dota 2, Counter-Strike: Global Offensive, and Team Fortress 2 gamers. Also, it logs key strokes and transmits the information to criminals. It can be assumed that, like its predecessor, Trojan. SteamLogger.1 is spread via forums or Steam live chat in offers to sell, buy or exchange game items.
The malicious program consists of three modules, the first of which is a dropper that decrypts and extracts from its body the main and service modules. The service module is stored in a temporary folder as Update.exe and launched, and the main module is loaded in the infected system's memory by means of a system routine. Then the service module downloads an image from the attackers' site, saves it into the temporary folder and immediately displays it on the screen:
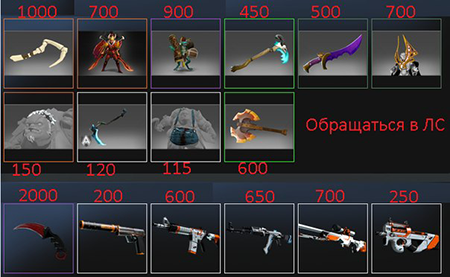
The service module checks whether the subdirectory Common Files\Steam\ is located in Program Files, and if it is not present, the module creates it. After that, the module copies itself to the folder under the name SteamService.exe, sets the attributes for the executable as “system” and “hidden”, and then adds a registry entry, so that SteamService.exe will be launched automatically and start the file. Then the service module sends a query to the attackers' site, and if the instruction “OK” is not returned, it attempts to establish a connection to the command and control server via any of the proxy servers on its hardcoded list. Trojan.SteamLogger.1 transmits information about the infected computer to the remote server. The data includes the operating system version and platform, as well as its unique identifier, generated using the serial number of the hard disk that contains the C partition. In addition, Trojan.SteamLogger.1 can receive an instruction to update its service module.
Once the main Trojan. SteamLogger.1 module is started and initialised, it searches the infected system memory for a Steam process and verifies whether the user has logged in on the Steam server under their account. If not, the malicious program waits for the server to authorise a player and then extracts information about their Steam account (the availability of SteamGuard, steam-id, security token). The program then transmits the data to the criminals. In response,Trojan.SteamLogger.1 gets a list of accounts to which game items from the compromised account can be transferred. All the collected data is sent to the criminals' server after which the Trojan checks whether automatic authorisation is enabled in the Steam settings. If the feature is disabled, the malware creates a separate thread to run the keylogger. Information about logged key strokes will be sent to the attackers in 15-second intervals.
To search for the inventory and valuable in-game items, Trojan. SteamLogger.1 uses such keywords as Mythical, Legendary, Arcana, Immortal, DOTA_WearableType_Treasure_Key, Container, and Supply Crate. That is, the Trojan attempts to steal the most valuable in-game items, chests and chest keys. Trojan.SteamLogger.1 also monitors whether players attempt to sell any of the virtual items themselves, and if they do, it automatically removes the items from the sale dialogue box.
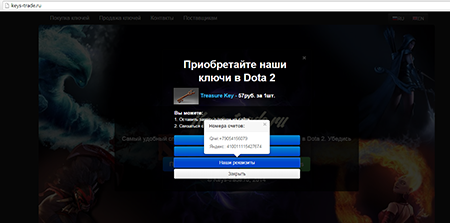
Trojan.SteamLogger.1 primarily targets Dota 2, Counter-Strike: Global Offensive, and Team Fortress 2. However, it can easily be tweaked to steal assets of other games. All the stolen virtual items are transferred to cybercriminals' accounts—as instructed by the command and control server. Then criminals use their specially designed e-store to sell the cheapest portion of their stolen loot, namely Dota 2 chest keys. It is not quite clear how the criminals convert other items into money.
It can steal game assets from Dota 2, Counter-Strike: Global Offensive, and Team Fortress 2 gamers. Also, it logs key strokes and transmits the information to criminals. It can be assumed that, like its predecessor, Trojan. SteamLogger.1 is spread via forums or Steam live chat in offers to sell, buy or exchange game items.
The malicious program consists of three modules, the first of which is a dropper that decrypts and extracts from its body the main and service modules. The service module is stored in a temporary folder as Update.exe and launched, and the main module is loaded in the infected system's memory by means of a system routine. Then the service module downloads an image from the attackers' site, saves it into the temporary folder and immediately displays it on the screen:

The service module checks whether the subdirectory Common Files\Steam\ is located in Program Files, and if it is not present, the module creates it. After that, the module copies itself to the folder under the name SteamService.exe, sets the attributes for the executable as “system” and “hidden”, and then adds a registry entry, so that SteamService.exe will be launched automatically and start the file. Then the service module sends a query to the attackers' site, and if the instruction “OK” is not returned, it attempts to establish a connection to the command and control server via any of the proxy servers on its hardcoded list. Trojan.SteamLogger.1 transmits information about the infected computer to the remote server. The data includes the operating system version and platform, as well as its unique identifier, generated using the serial number of the hard disk that contains the C partition. In addition, Trojan.SteamLogger.1 can receive an instruction to update its service module.
Once the main Trojan. SteamLogger.1 module is started and initialised, it searches the infected system memory for a Steam process and verifies whether the user has logged in on the Steam server under their account. If not, the malicious program waits for the server to authorise a player and then extracts information about their Steam account (the availability of SteamGuard, steam-id, security token). The program then transmits the data to the criminals. In response,Trojan.SteamLogger.1 gets a list of accounts to which game items from the compromised account can be transferred. All the collected data is sent to the criminals' server after which the Trojan checks whether automatic authorisation is enabled in the Steam settings. If the feature is disabled, the malware creates a separate thread to run the keylogger. Information about logged key strokes will be sent to the attackers in 15-second intervals.
To search for the inventory and valuable in-game items, Trojan. SteamLogger.1 uses such keywords as Mythical, Legendary, Arcana, Immortal, DOTA_WearableType_Treasure_Key, Container, and Supply Crate. That is, the Trojan attempts to steal the most valuable in-game items, chests and chest keys. Trojan.SteamLogger.1 also monitors whether players attempt to sell any of the virtual items themselves, and if they do, it automatically removes the items from the sale dialogue box.
Trojan.SteamLogger.1 primarily targets Dota 2, Counter-Strike: Global Offensive, and Team Fortress 2. However, it can easily be tweaked to steal assets of other games. All the stolen virtual items are transferred to cybercriminals' accounts—as instructed by the command and control server. Then criminals use their specially designed e-store to sell the cheapest portion of their stolen loot, namely Dota 2 chest keys. It is not quite clear how the criminals convert other items into money.



