- Apr 25, 2013
- 5,355
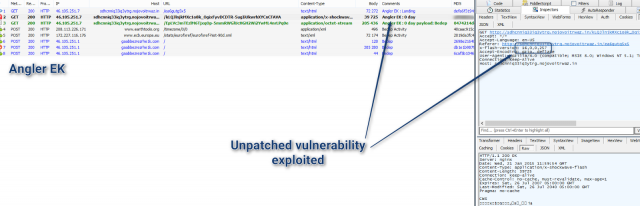
If you've been meaning to disable Adobe Flash, now might be a good time. Attacks exploiting a critical vulnerability in the latest version of the animation software have been added to a popular exploitation kit, researchers confirmed. Attackers often buy the kits to spare the hassle of writing their own weaponized exploits.
Prolific exploit sleuth Kafeine uncovered the addition to Angler, an exploit kit available in underground forums. The zero-day vulnerability was confirmed by Malwarebytes. Malwarebytes researcher Jérôme Segura said one attack he observed used the new exploit to install a distribution botnet known as Bedep.
Adobe officials say only that they're investigating the reports. Until there's a patch, it makes sense to minimize use of Flash when possible. AV software from Malwarebytes and others can also block Angler attacks.
