- Apr 25, 2013
- 5,355
Security experts at TrendMicro have detected a new variant of the BIFROSE malware leveraging on the Tor network in a targeted attack.
Security experts at TrendMicro have been investigating a targeted attack against a device manufacturer when they discovered that BIFROSE malware, a well-known backdoor, has infected the systems of the company. BIFROSE has been around for many years and it is quite easy to acquire it the underground. BIFROSE has data stealing capability, but it is mostly popular for its keylogging routines, but the variant detected by the at TrendMicro (detected as BKDR_BIFROSE.ZTBG-A and has the hash 5e2844b20715d0806bfa28bd0ebcba6cbb637ea1) leverages theTor network to hide the communications between the infected machines and the C&C server.
“What makes this variant more elusive is its ability of Tor to communicate with its command-and-control [C&C] server.”” reports a blog post published by TrendMicro.
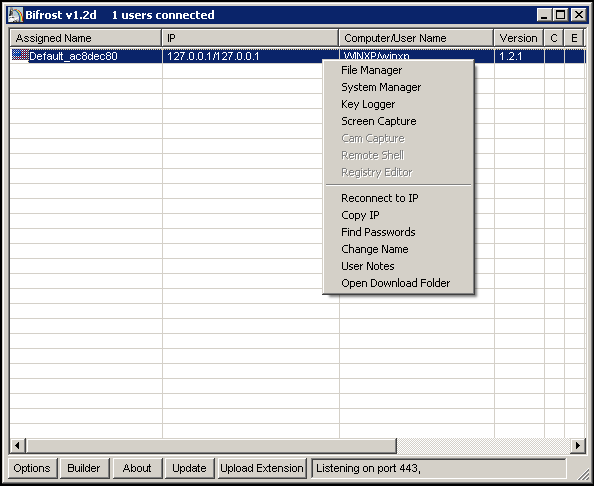
The BIFROSE malware was widely used by cyber criminals, in 2010 a threat actor targeted human resource (HR) personnel of different government offices, including the African Union and the NATO. The BIFROSE variant used in the targeted attack on the device manufacturer is able to perform the following operations, as explained in the blog post:
Security experts at TrendMicro have been investigating a targeted attack against a device manufacturer when they discovered that BIFROSE malware, a well-known backdoor, has infected the systems of the company. BIFROSE has been around for many years and it is quite easy to acquire it the underground. BIFROSE has data stealing capability, but it is mostly popular for its keylogging routines, but the variant detected by the at TrendMicro (detected as BKDR_BIFROSE.ZTBG-A and has the hash 5e2844b20715d0806bfa28bd0ebcba6cbb637ea1) leverages theTor network to hide the communications between the infected machines and the C&C server.
“What makes this variant more elusive is its ability of Tor to communicate with its command-and-control [C&C] server.”” reports a blog post published by TrendMicro.

The BIFROSE malware was widely used by cyber criminals, in 2010 a threat actor targeted human resource (HR) personnel of different government offices, including the African Union and the NATO. The BIFROSE variant used in the targeted attack on the device manufacturer is able to perform the following operations, as explained in the blog post:
- Download a file
- Upload a file
- Get file details (file size, last modified time)
- Create a folder
- Delete a folder
- Open a file using ShellExecute
- Execute a command line
- Rename a file
- Enumerate all windows and their process IDs
- Close a window
- Move a window to the foreground
- Hide a window
- Send keystrokes to a window
- Send mouse events to a window
- Terminate a process
- Get display resolution
- Upload contents of %Windows%\winieupdates\klog.dat
- Capture screenshot or webcam image
“Another indicator would be seeing abnormal activities, such as those seen through network and mail logs. As we’ve mentioned in our past post, 7 Places to Check for Signs of a Targeted Attack in Your Network, network activities such as logins and emails during “abnormal” times need to be checked.” suggests Christopher Daniel So, Threat Response Engineer at TrendMicro.
The use of Tor network is becoming popular within the community of malware authors, also a recent variant of Zeus was able to hide its communications in theanonymizing network. The use of Tor makes troubling tracking and taking down the malware infrastructure, but IT administrator could carefully monitor their network to detect Tor activity, since several strain of malware uses Tor in communicating with their C&C servers.
The use of Tor network is becoming popular within the community of malware authors, also a recent variant of Zeus was able to hide its communications in theanonymizing network. The use of Tor makes troubling tracking and taking down the malware infrastructure, but IT administrator could carefully monitor their network to detect Tor activity, since several strain of malware uses Tor in communicating with their C&C servers.
