- Sep 17, 2013
- 1,492
http://ultrapasswordcreator.com/index.php
Ultra Password Creator Software
1. How To Make Great Passwords
UPC is for people that want to use far stronger passwords than they could ordinarily use by memory alone. UPC passwords are made by transforming memorable information a person knows to highly complex pseudo-random character strings. With a single Secret Input Phrase memorable to the user they can use exceptionally strong passwords for multiple accounts and because passwords are produced on-demand there is no need to hide, store or protect a plaintext password from an adversary.
2. SIP & The Two-Part Key
At the heart of the UPC design is a two-part key. The Secret Input Phrase (SIP) is the first part and the Password Identifier (PI) is the second part. Both parts are required to produce, or reproduce a password. The SIP can be a simple phrase or longer text up to thousands of characters in length. The most effective SIPs are those that are memorable and distinctive. The inspiration for a SIP can be from something you know or text you can refer to. The examples below suggest how creative one can be:
1. "Frozen yogurt with pecan sprinkles"
2. "5:30pm is a great time for tea"
3."A smile and a wink ;-)"
and a wink ;-)"
4. "To be, or not to be: that is the question:
Whether 'tis nobler in the mind to suffer
The slings and arrows of outrageous fortune"
While the SIP is never stored by the application, the user has the option to save a PI associated with a particular password.
Additional SIP Rules:
SIPs must be entered the same way each time they are used. SIPs are case sensitive, punctuation sensitive and font sensitive. Manually typed SIPs will automatically have the correct font.
If text is borrowed from any public literature or popular media such as a movie or a song, it is recommended the text be modified in some way. The modification does not have to be large, perhaps adding or subtracting a comma, a period, or changing the capitalization or simply adding new text following your phrase. The objective is for your SIP not to be identical to the publicly available version. The avalanche property of the UPC engine will make the output significantly different than the original text even if the modification is small. This increases resiliance to attack by adversaries drawing on publicly available media to accelerate an attack.
To illustrate the point, below are two hypothetical 20 character passwords of two nearly identical SIPs. The only difference in the second example is the period instead of the colon as the last character. Comparing the two shows dramatically different passwords despite their SIPs being almost identical.
- "To be, or not to be: that is the question:" ---> Hukqpel9HsysTfqKYYhf
- "To be, or not to be: that is the question." ---> MO7j8aamtn49QAK08AnA
Whatever modifications one makes to text drawn from published literature should be memorable.
Overall, the best SIPs are those that are unique and private and should not be information one might find by reading one's social media profile. See below, Saving and Retrieving Parameters.
3. Making Password Identifiers
The Password Identifier (PI) is the second part of the two-part key. It is intended to be a label for each password made. Although it is not required, the UPC application provides the ability to save the PI and password length associated with each password. When this information is retrieved one only need enter their SIP to reproduce their password. Password Identifiers cannot have blank spaces nor use the character "|". Those characters are reserved for the application.
Password Identifiers might contain dates or version numbers to identify multiple passwords used for the same account. Examples of this are:
"my_yahoo_080114"
"my_wellsfargo_v1"
If one makes PIs in this manner they can quickly identify when those passwords were made using the Retrieve function. This can be useful for those changing passwords at regular intervals or managing multiple versions of passwords for the same account.
4. Setting Password Length
One of the most effective strategies one can use to make a strong password is to increase its length. With UPC one selects password length using the rotating password length selector that ranges from 4 to 32 characters. A UPC password of length 32 has 192 bits of entropy and could take modern supercomputers up to 1.9 x 1029 years attempting to recover the password.
5. Producing Passwords
Once the inputs have been entered generating the password is done simply by pressing the Generate Password button.
Passwords produced by UPC can have upper & lower case Latin letters, numerals 0-9 and the special characters "/" and "+". Passwords produced by UPC are deterministic. This means that UPC will always produce the same password provided the identical inputs are used. This enables one to reproduce a complex password at any time and on any device the UPC application is installed, and to do this entirely from memory.
6. Pasting Passwords Into Applications
Pressing the Generate Password button UPC automatically copies the password to the clipboard so that one can immediately paste the password into the desired application. ** As soon as the password is no longer needed one should clear all UPC parameters & the Windows clipboard by pressing the Clear Parameters button. See "Clearing The Parameter" section below. **
7. Saving & Retrieving Parameters
UPC provides the capability to save parameters used to produce a password. This feature can be convenient when one wants to quickly reproduce that password later. The parameters that can be saved are the Password Identifier and passord length. To save these parameters after a password has been generated select the File/Save Profile drop down selection. A confirmation message will be shown to confirm the save action.
To retrieve the parameters select the File/Retrieve drop down selection and the parameters will automatically be inserted into the appropriate fields. Then enter your Secret Input Phrase and press Generate Password to generate the password.
8. Clearing The Parameters **
Pressing UPC's Clear Parameters button will reset UPC's parameters to their default values and clear the Windows Clipboard which contains the most recent password produced. This step should be performed as soon as the password is no longer needed.
9. Password Strength (Entropy)
A useful way to view password entropy is to imagine one is looking for a needle in a haystack and to find the needle they must remove one piece of hay at a time. The entropy value represents the number of individual pieces of hay the haystack contains before the search begins. Clearly, the larger the haystack the more guesses must be made before the needle is found. The actual Password Entropy value is the number of binary digits needed to represent the number of "guesses" in base 2 format.
10. Estimating Password Survivability
Like most designs, passwords are made for a particular purpose. It can be useful to understand how the selections one makes for password length impacts password survivability. The main menu Password Strength dropdown links to an interactive website [passwordstrengthcalculator.org] that explains how the choices one makes for password length and cardinality impact survivability given the computer power adversaries can apply at this time.
UPC users can estimate survivability of a password for a brute force attack at the site. Most importantly and for your safety, no password is required to perform the calculation. UPC users calculating survivability should enter the length of a hypothetical password and select the top four checkboxes in Step 2.
11. Making Master Passwords For Password Managers
Password managers can be useful tools to store and transmit passwords to applications that support the appropriate technology. However, because password managers stores its passwords in an encrypted file, the password manager itself needs its own Master Password to administer the stored passwords. The strength of this one Master Password is critical because it is the gatekeeper to all the passwords managed by the password manager.
Ultra Password Creator is an ideal companion to password managers because it can help the PC owner create a very strong password Master Password from memory while eliminating the risk of having to save the plaintext copy in physical or digital form.
12. Using UPC Across Multiple Windows Devices
UPC's license allows the application to be installed on as many Windows devices as one likes. To transfer saved password profile information copy the upcdata.txt file within the \My Documents\Ultra Password Creator directory of the account the application is installed to the same directory path on other PCs UPC is installed.
Create a strong password
Create even more lengthy passwords
With simple trick you can create even more lengthy password
What you need to remember
Demo
Password output 1 : 5IWRU5ossqx2qcN97qdnC1czAaA3suB7

Use the password output no. 1 as phrase to create new password output
Password Output No. 2 : 6CdQDGA68n4M+EYjs5wxDUrUTV3kPdGY

Similarly you can keep creating password outputs.
Finally concatenate all the password outputs to make a lengthy password
Final lengthy password using two password outputs : 5IWRU5ossqx2qcN97qdnC1czAaA3suB76CdQDGA68n4M+EYjs5wxDUrUTV3kPdGY
If we proceed two more times
password output no. 3 : oNWKKj6aNljXYAjzhpj8BaRaGteu10c+

Password output no. 4 : IiqHOKdchU/rdlwN/Y92bbZcWKa3YQcZ

Final lengthy password using all four password output : 5IWRU5ossqx2qcN97qdnC1czAaA3suB76CdQDGA68n4M+EYjs5wxDUrUTV3kPdGYoNWKKj6aNljXYAjzhpj8BaRaGteu10c+IiqHOKdchU/rdlwN/Y92bbZcWKa3YQcZ
With this method you can create lengthy password
Ultra Password Creator Software
1. How To Make Great Passwords
UPC is for people that want to use far stronger passwords than they could ordinarily use by memory alone. UPC passwords are made by transforming memorable information a person knows to highly complex pseudo-random character strings. With a single Secret Input Phrase memorable to the user they can use exceptionally strong passwords for multiple accounts and because passwords are produced on-demand there is no need to hide, store or protect a plaintext password from an adversary.
2. SIP & The Two-Part Key
At the heart of the UPC design is a two-part key. The Secret Input Phrase (SIP) is the first part and the Password Identifier (PI) is the second part. Both parts are required to produce, or reproduce a password. The SIP can be a simple phrase or longer text up to thousands of characters in length. The most effective SIPs are those that are memorable and distinctive. The inspiration for a SIP can be from something you know or text you can refer to. The examples below suggest how creative one can be:
1. "Frozen yogurt with pecan sprinkles"
2. "5:30pm is a great time for tea"
3."A smile
4. "To be, or not to be: that is the question:
Whether 'tis nobler in the mind to suffer
The slings and arrows of outrageous fortune"
While the SIP is never stored by the application, the user has the option to save a PI associated with a particular password.
Additional SIP Rules:
SIPs must be entered the same way each time they are used. SIPs are case sensitive, punctuation sensitive and font sensitive. Manually typed SIPs will automatically have the correct font.
If text is borrowed from any public literature or popular media such as a movie or a song, it is recommended the text be modified in some way. The modification does not have to be large, perhaps adding or subtracting a comma, a period, or changing the capitalization or simply adding new text following your phrase. The objective is for your SIP not to be identical to the publicly available version. The avalanche property of the UPC engine will make the output significantly different than the original text even if the modification is small. This increases resiliance to attack by adversaries drawing on publicly available media to accelerate an attack.
To illustrate the point, below are two hypothetical 20 character passwords of two nearly identical SIPs. The only difference in the second example is the period instead of the colon as the last character. Comparing the two shows dramatically different passwords despite their SIPs being almost identical.
- "To be, or not to be: that is the question:" ---> Hukqpel9HsysTfqKYYhf
- "To be, or not to be: that is the question." ---> MO7j8aamtn49QAK08AnA
Whatever modifications one makes to text drawn from published literature should be memorable.
Overall, the best SIPs are those that are unique and private and should not be information one might find by reading one's social media profile. See below, Saving and Retrieving Parameters.
3. Making Password Identifiers
The Password Identifier (PI) is the second part of the two-part key. It is intended to be a label for each password made. Although it is not required, the UPC application provides the ability to save the PI and password length associated with each password. When this information is retrieved one only need enter their SIP to reproduce their password. Password Identifiers cannot have blank spaces nor use the character "|". Those characters are reserved for the application.
Password Identifiers might contain dates or version numbers to identify multiple passwords used for the same account. Examples of this are:
"my_yahoo_080114"
"my_wellsfargo_v1"
If one makes PIs in this manner they can quickly identify when those passwords were made using the Retrieve function. This can be useful for those changing passwords at regular intervals or managing multiple versions of passwords for the same account.
4. Setting Password Length
One of the most effective strategies one can use to make a strong password is to increase its length. With UPC one selects password length using the rotating password length selector that ranges from 4 to 32 characters. A UPC password of length 32 has 192 bits of entropy and could take modern supercomputers up to 1.9 x 1029 years attempting to recover the password.
5. Producing Passwords
Once the inputs have been entered generating the password is done simply by pressing the Generate Password button.
Passwords produced by UPC can have upper & lower case Latin letters, numerals 0-9 and the special characters "/" and "+". Passwords produced by UPC are deterministic. This means that UPC will always produce the same password provided the identical inputs are used. This enables one to reproduce a complex password at any time and on any device the UPC application is installed, and to do this entirely from memory.
6. Pasting Passwords Into Applications
Pressing the Generate Password button UPC automatically copies the password to the clipboard so that one can immediately paste the password into the desired application. ** As soon as the password is no longer needed one should clear all UPC parameters & the Windows clipboard by pressing the Clear Parameters button. See "Clearing The Parameter" section below. **
7. Saving & Retrieving Parameters
UPC provides the capability to save parameters used to produce a password. This feature can be convenient when one wants to quickly reproduce that password later. The parameters that can be saved are the Password Identifier and passord length. To save these parameters after a password has been generated select the File/Save Profile drop down selection. A confirmation message will be shown to confirm the save action.
To retrieve the parameters select the File/Retrieve drop down selection and the parameters will automatically be inserted into the appropriate fields. Then enter your Secret Input Phrase and press Generate Password to generate the password.
8. Clearing The Parameters **
Pressing UPC's Clear Parameters button will reset UPC's parameters to their default values and clear the Windows Clipboard which contains the most recent password produced. This step should be performed as soon as the password is no longer needed.
9. Password Strength (Entropy)
A useful way to view password entropy is to imagine one is looking for a needle in a haystack and to find the needle they must remove one piece of hay at a time. The entropy value represents the number of individual pieces of hay the haystack contains before the search begins. Clearly, the larger the haystack the more guesses must be made before the needle is found. The actual Password Entropy value is the number of binary digits needed to represent the number of "guesses" in base 2 format.
10. Estimating Password Survivability
Like most designs, passwords are made for a particular purpose. It can be useful to understand how the selections one makes for password length impacts password survivability. The main menu Password Strength dropdown links to an interactive website [passwordstrengthcalculator.org] that explains how the choices one makes for password length and cardinality impact survivability given the computer power adversaries can apply at this time.
UPC users can estimate survivability of a password for a brute force attack at the site. Most importantly and for your safety, no password is required to perform the calculation. UPC users calculating survivability should enter the length of a hypothetical password and select the top four checkboxes in Step 2.
11. Making Master Passwords For Password Managers
Password managers can be useful tools to store and transmit passwords to applications that support the appropriate technology. However, because password managers stores its passwords in an encrypted file, the password manager itself needs its own Master Password to administer the stored passwords. The strength of this one Master Password is critical because it is the gatekeeper to all the passwords managed by the password manager.
Ultra Password Creator is an ideal companion to password managers because it can help the PC owner create a very strong password Master Password from memory while eliminating the risk of having to save the plaintext copy in physical or digital form.
12. Using UPC Across Multiple Windows Devices
UPC's license allows the application to be installed on as many Windows devices as one likes. To transfer saved password profile information copy the upcdata.txt file within the \My Documents\Ultra Password Creator directory of the account the application is installed to the same directory path on other PCs UPC is installed.
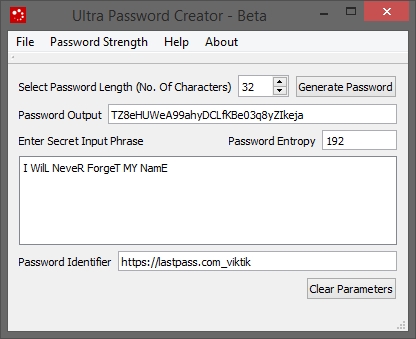
Create a strong password
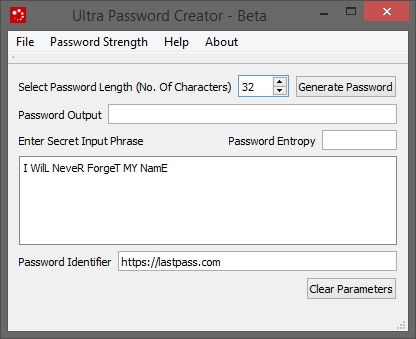
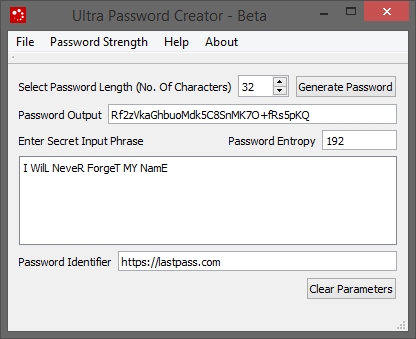
- Enter the "Secret input phrase". This is easy to remember phrase and must be remembered.
- Select Password Length. Max is 32
- Enter password Identifier. This must be remembered
- Click "Generate"
- Password created of length 32 character
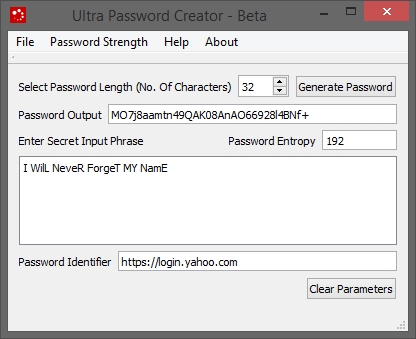
- Using same "Secret Input Phrase" to create another password for yahoo.com
- You may attach your username to "Password Identifier" along with the website name for which you are creating password.
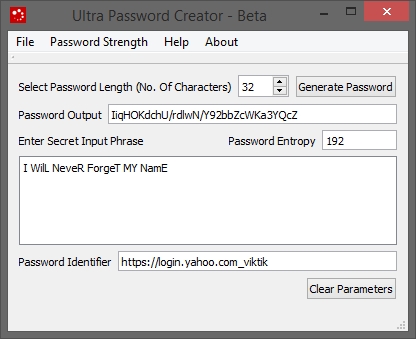
- A different password generated for yahoo.com with user name "viktik". Thus you can generate separate password for each username of same website. All this with remembering only one "Secret Input phrase".
- Better use "Ultra Password Creator" to just create a strong master password for "password managers" like "lastpass". Then the password manager will manage a number of strong login passwords for various websites and vaults. With this method the master password for password managers will be very strong and won't be easy to crack. All this by just remembering easy Secret input phrase (SIP).
Create even more lengthy passwords
With simple trick you can create even more lengthy password
What you need to remember
- The secret phrase
- Password identifier
Demo
- The secret phrase : (CrazY*LunatiC*MooN)
- Password identifier : google.com
Password output 1 : 5IWRU5ossqx2qcN97qdnC1czAaA3suB7

Use the password output no. 1 as phrase to create new password output
Password Output No. 2 : 6CdQDGA68n4M+EYjs5wxDUrUTV3kPdGY

Similarly you can keep creating password outputs.
Finally concatenate all the password outputs to make a lengthy password
Final lengthy password using two password outputs : 5IWRU5ossqx2qcN97qdnC1czAaA3suB76CdQDGA68n4M+EYjs5wxDUrUTV3kPdGY
If we proceed two more times
password output no. 3 : oNWKKj6aNljXYAjzhpj8BaRaGteu10c+

Password output no. 4 : IiqHOKdchU/rdlwN/Y92bbZcWKa3YQcZ

Final lengthy password using all four password output : 5IWRU5ossqx2qcN97qdnC1czAaA3suB76CdQDGA68n4M+EYjs5wxDUrUTV3kPdGYoNWKKj6aNljXYAjzhpj8BaRaGteu10c+IiqHOKdchU/rdlwN/Y92bbZcWKa3YQcZ
With this method you can create lengthy password
Last edited:

