- Oct 23, 2012
- 12,527
Malware authors have improved the functionality of Dyre banking Trojan, which now benefits from its own SSL certificate to communicate with its command and control (C&C) servers.
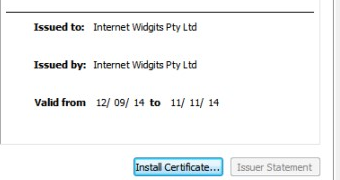
In a recently analyzed sample, security researchers discovered that the malware relies on a digital certificate issued for an entity called Internet Widgits Pty Ltd.
Proofpoint security experts determined that the communication with the remote servers occurs on ports 443 and 4443.
By using its own certificate for the communication, the actors behind the new variant of Dyre make it more difficult for security solutions to identify the traffic as illegitimate.
New Dyre steals browser data and enumerates installed programs
In the latest variant, they found that a freshly introduced feature, called “browsersnapshot,” is responsible for collecting browser data like cookies, client-side certificates and private keys from the Windows Certificate Store used by Internet Explorer and the Firefox certificate database.
Also new is enumerating the programs installed on the compromised computer as well as the running services. This is generally done by cybercriminals as a research for creating more efficient attacks on the victims, or to create a database with the attack vectors that would work on specific types of users.
As far as the targets are concerned, the Trojan is instructed to download them from the C&C server. This makes the malware a much more flexible tool in the hands of cybercriminals as they can add or remove targets according to their needs.
List of targets can be updated at any time
Proofpoint discovered that Salesforce.com was among the targets, which could suggest that the same variant was used against the customers of cloud-based CRM provider in the attack that took place earlier this month.
“This sample of Dyreza highlights the rapid adaptation of new malware to updated defenses and the effort by crimeware groups to pursue new targets. Expect to see Dyreza and other threats continue to evolve – and to evolve more rapidly – as time goes by,” Proofpoint warns.
The Trojan has been first reported by PhishMe back in June and after analysing it, they determined that it could bypass the SSL mechanism in the browser through the technique known as man-in-the-middle (MitM), which allows interception of encrypted data without giving any sign that the secure connection is compromised.
The malware has been created specifically to steal banking information from users and initially it targeted connections to Bank of America, Citigroup, the Royal Bank of Scotland, Ulsterbank and Natwest financial institutions.

In a recently analyzed sample, security researchers discovered that the malware relies on a digital certificate issued for an entity called Internet Widgits Pty Ltd.
Proofpoint security experts determined that the communication with the remote servers occurs on ports 443 and 4443.
By using its own certificate for the communication, the actors behind the new variant of Dyre make it more difficult for security solutions to identify the traffic as illegitimate.
New Dyre steals browser data and enumerates installed programs
In the latest variant, they found that a freshly introduced feature, called “browsersnapshot,” is responsible for collecting browser data like cookies, client-side certificates and private keys from the Windows Certificate Store used by Internet Explorer and the Firefox certificate database.
Also new is enumerating the programs installed on the compromised computer as well as the running services. This is generally done by cybercriminals as a research for creating more efficient attacks on the victims, or to create a database with the attack vectors that would work on specific types of users.
As far as the targets are concerned, the Trojan is instructed to download them from the C&C server. This makes the malware a much more flexible tool in the hands of cybercriminals as they can add or remove targets according to their needs.
List of targets can be updated at any time
Proofpoint discovered that Salesforce.com was among the targets, which could suggest that the same variant was used against the customers of cloud-based CRM provider in the attack that took place earlier this month.
“This sample of Dyreza highlights the rapid adaptation of new malware to updated defenses and the effort by crimeware groups to pursue new targets. Expect to see Dyreza and other threats continue to evolve – and to evolve more rapidly – as time goes by,” Proofpoint warns.
The Trojan has been first reported by PhishMe back in June and after analysing it, they determined that it could bypass the SSL mechanism in the browser through the technique known as man-in-the-middle (MitM), which allows interception of encrypted data without giving any sign that the secure connection is compromised.
The malware has been created specifically to steal banking information from users and initially it targeted connections to Bank of America, Citigroup, the Royal Bank of Scotland, Ulsterbank and Natwest financial institutions.