- Jan 24, 2011
- 9,378
Malware, short for malicious (or malevolent) software, is software used or programmed by attackers to disrupt computer operation, gather sensitive information, or gain access to private computer systems. It can appear in the form of code, scripts, active content, and other software. ‘Malware’ is a general term used to refer to a variety of forms of hostile or intrusive software.
Malware includes computer viruses, ransomware, worms, trojan horses, rootkits, keyloggers, dialers, spyware, adware, malicious BHOs, rogue security software and other malicious programs; the majority of active malware threats are usually worms or trojans rather than viruses.
It’s not always easy to tell if your computer was compromised or not,because these days cybercriminals are going to great lengths to hide their code and conceal what their programs are doing on an infected computer.
It’s very difficult to provide a list of characteristic symptoms of a infected computer because the same symptoms can also be caused by hardware incompatibilities or system instability,however here are just a few examples that may suggest that your PC has been compromised :
How to remove viruses, ransomware, worms, trojan horses, rootkits, keyloggers, dialers, spyware, adware, malicious BHOs, rogue security software and other malicious programs
OPTIONAL: Some forms of malware will not allow you to start some of the below utilites and on-demand scanners, while running Windows in Normal mode. If this happens, we recommend that you start your computer in Start your computer in Safe Mode with Networking, and try from there to perform the scan.
We recommend that you first try to run the below scans while your computer is in Normal mode, and only if you are experiencing issues, should you try to start the computer in Safe Mode with Networking.
To start your computer Start your computer in Safe Mode with Networking, you can follow the below steps:
STEP 1: Scan your computer with Kaspersky TDSSKiller
In this first step, we will run a system scan with Kaspersky TDSSKIller to remove any malicious software that might be installed on your system.
RKill is a program that will attempt to terminate all malicious processes associated with “Windows Update can not continue as your Software copy is Expired/Corrupt” infection, so that we will be able to perform the next step without being interrupted by this malicious software.
Because this utility will only stop “Windows Update can not continue as your Software copy is Expired/Corrupt” running process and does not delete any files, after running it you should not reboot your computer as any malware processes that are configured to start automatically will just be started again.
Malwarebytes Anti-Malware Free uses industry-leading technology to detect and remove all traces of malware, including worms, Trojans, rootkits, rogues, dialers, spyware, and more.
It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
HitmanPro is a second opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc.) that have infected your computer despite all the security measures you have taken (such as anti virus software, firewalls, etc.). HitmanPro is designed to work alongside existing security programs without any conflicts. It scans the computer quickly (less than 5 minutes) and does not slow down the computer.
The AdwCleaner utility will scan your computer and web browser for the malicious files, browser extensions and registry keys, that may have been installed on your computer without your knowledge.
Zemana AntiMalware is a cloud on-demand scanner which uses several antivirus engines to scan your computer for malware.
This step should be performed only if your issues have not been solved by the previous steps.
Malware includes computer viruses, ransomware, worms, trojan horses, rootkits, keyloggers, dialers, spyware, adware, malicious BHOs, rogue security software and other malicious programs; the majority of active malware threats are usually worms or trojans rather than viruses.
It’s not always easy to tell if your computer was compromised or not,because these days cybercriminals are going to great lengths to hide their code and conceal what their programs are doing on an infected computer.
It’s very difficult to provide a list of characteristic symptoms of a infected computer because the same symptoms can also be caused by hardware incompatibilities or system instability,however here are just a few examples that may suggest that your PC has been compromised :
- You may receive the error “Internet Explorer could not display the page” when attempting to access certain websites
- Your web browser (e.g., Microsoft Internet Explorer, Mozilla Firefox, Google Chrome) freezes, hangs or is unresponsive
- Your web browser’s default homepage is changed
- Access to security related websites is blocked
- You get redirected to web pages other than the one you intended to go to
- You receive numerous web-browser popup messages
- Strange or unexpected toolbars appear at the top of your web browser
- Your computer runs slower than usual
- Your computer freezes, hangs or is unresponsive
- There are new icons on your desktop that you do not recognize
- Your computer restarts by itself (but not a restart caused by Windows Updates)
- You see unusual error messages (e.g., messages saying there are missing or corrupt files folders)
- You are unable to access the Control Panel, Task Manager, Registry Editor or Command Prompt.
How to remove viruses, ransomware, worms, trojan horses, rootkits, keyloggers, dialers, spyware, adware, malicious BHOs, rogue security software and other malicious programs
OPTIONAL: Some forms of malware will not allow you to start some of the below utilites and on-demand scanners, while running Windows in Normal mode. If this happens, we recommend that you start your computer in Start your computer in Safe Mode with Networking, and try from there to perform the scan.
We recommend that you first try to run the below scans while your computer is in Normal mode, and only if you are experiencing issues, should you try to start the computer in Safe Mode with Networking.
To start your computer Start your computer in Safe Mode with Networking, you can follow the below steps:
- Remove all floppy disks, CDs, and DVDs from your computer, and then restart your computer.
- If you are using Windows XP, Vista or 7 press and hold the F8 key as your computer restarts.Please keep in mind that you need to press the F8 key before the Windows start-up logo appears.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen.If you are using Windows 8, press the Windows key + C, and then click Settings. Click Power, hold down Shift on your keyboard and click Restart, then click on Troubleshoot and select Advanced options. - In the Advanced Options screen, select Startup Settings, then click on Restart.
- If you are using Windows XP, Vista or 7 in the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
If you are using Windows 8, press 5 on your keyboard to Enable Safe Mode with Networking. - Windows will start in Safe Mode with Networking.
STEP 1: Scan your computer with Kaspersky TDSSKiller
In this first step, we will run a system scan with Kaspersky TDSSKIller to remove any malicious software that might be installed on your system.
- Please download the latest official version of Kaspersky TDSSKiller.
KASPERSKY TDSSKILLER DOWNLOAD LINK(This link will open a new web page from where you can download “Kaspersky TDSSKiller”.) - Double-click on tdsskiller.exe to open this utility, then click on Change Parameters.
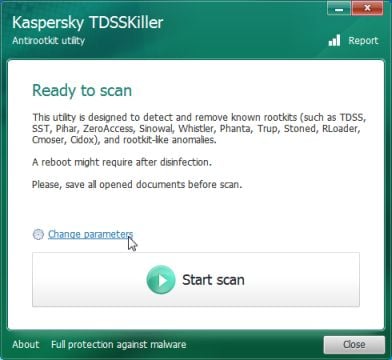
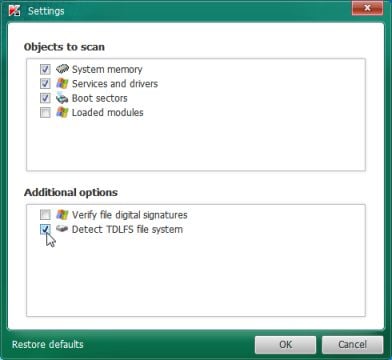
- In the new open window,we will need to enable Detect TDLFS file system, then click on OK.
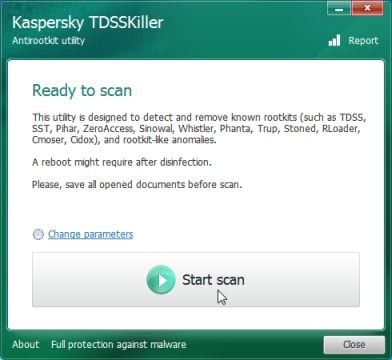
- Next,we will need to start a scan with Kaspersky, so you’ll need to press the Start Scan button.
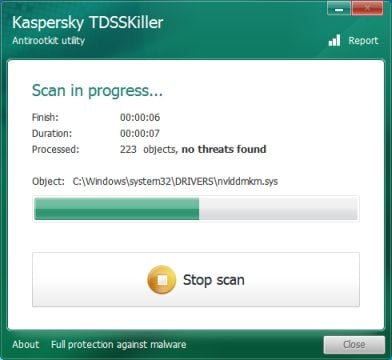
- Kaspersky TDSSKiller will now scan your computer for malware.
- When the scan has finished it will display a result screen stating whether or not the infection was found on your computer. If it was found it will display a screen similar to the one below.
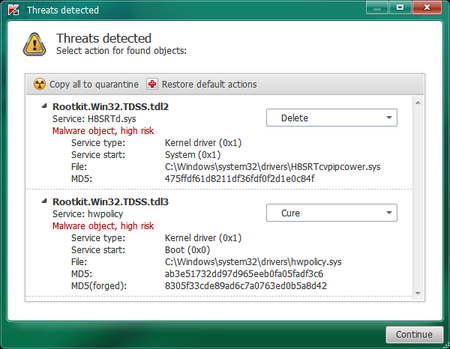
- To remove the infection simply click on the Continue button and TDSSKiller will attempt to clean the infection.A reboot will be require to completely remove any infection from your system.
RKill is a program that will attempt to terminate all malicious processes associated with “Windows Update can not continue as your Software copy is Expired/Corrupt” infection, so that we will be able to perform the next step without being interrupted by this malicious software.
Because this utility will only stop “Windows Update can not continue as your Software copy is Expired/Corrupt” running process and does not delete any files, after running it you should not reboot your computer as any malware processes that are configured to start automatically will just be started again.
- While your computer is in Safe Mode with Networking, please download Rkill from the below link.
RKILL DOWNLOAD LINK (his link will open a new web page from where you can download “RKill”) - Double click on Rkill program to stop the malicious programs from running.

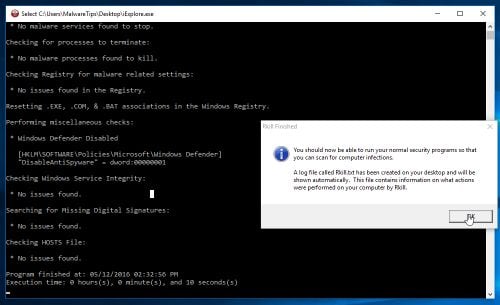
- RKill will now start working in the background, please be patient while this utiltiy looks for malicious process and tries to end them.
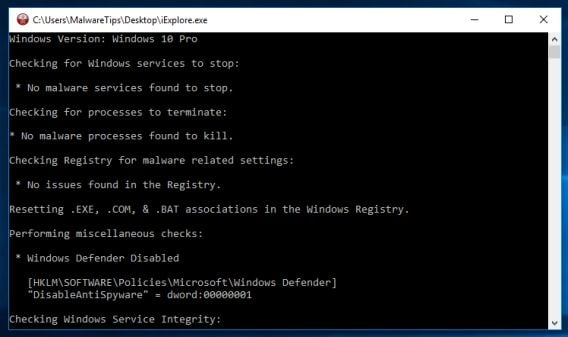
- When the Rkill tool has completed its task, it will generate a log. Do not reboot your computer after running RKill as the malware programs will start again.
Malwarebytes Anti-Malware Free uses industry-leading technology to detect and remove all traces of malware, including worms, Trojans, rootkits, rogues, dialers, spyware, and more.
It is important to note that Malwarebytes Anti-Malware works well and should run alongside antivirus software without conflicts.
- You can download download Malwarebytes Anti-Malware from the below link.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK (This link will open a new web page from where you can download “Malwarebytes Anti-Malware”) - Once downloaded, close all programs, then double-click on the icon on your desktop named “mbam-setup” to start the installation of Malwarebytes Anti-Malware.

You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
- When the installation begins, you will see the Malwarebytes Anti-Malware Setup Wizard which will guide you through the installation process.
To install Malwarebytes Anti-Malware on your machine, keep following the prompts by clicking the “Next” button.
- Once installed, Malwarebytes Anti-Malware will automatically start and will update the antivirus database. To start a system scan you can click on the “Scan Now” button.
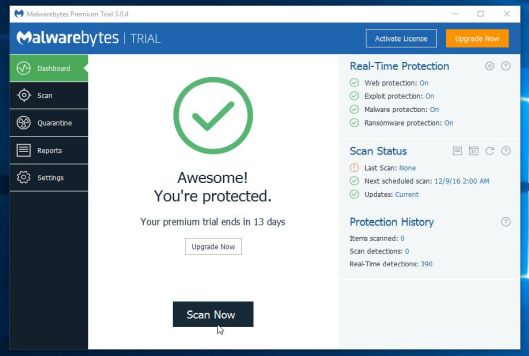
- Malwarebytes Anti-Malware will now start scanning your computer for malware. When Malwarebytes Anti-Malware is scanning it will look like the image below.
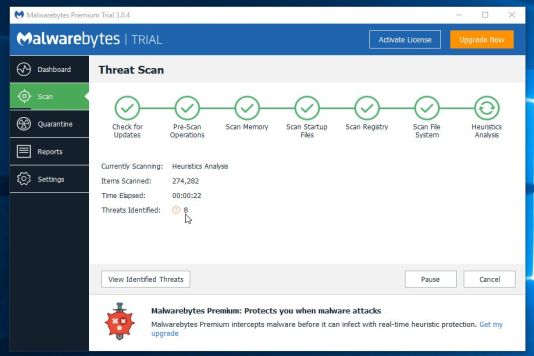
- When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes Anti-Malware has detected. To remove the malicious programs that Malwarebytes Anti-malware has found, click on the “Remove Selected” button.
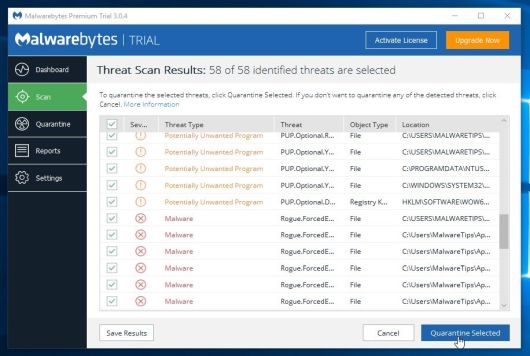
- Malwarebytes Anti-Malware will now quarantine all the malicious files and registry keys that it has found. When removing the files, Malwarebytes Anti-Malware may require a reboot in order to remove some of them. If it displays a message stating that it needs to reboot your computer, please allow it to do so.
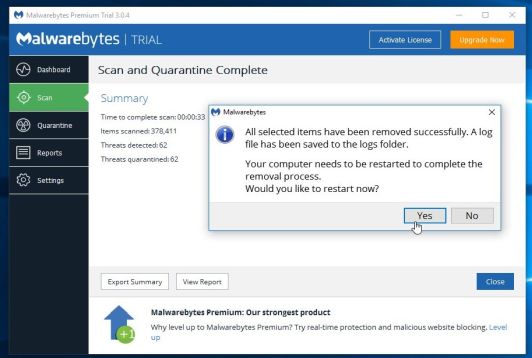
After your computer will restart, you should open Malwarebytes Anti-Malware and perform another scanto verify that there are no remaining threats
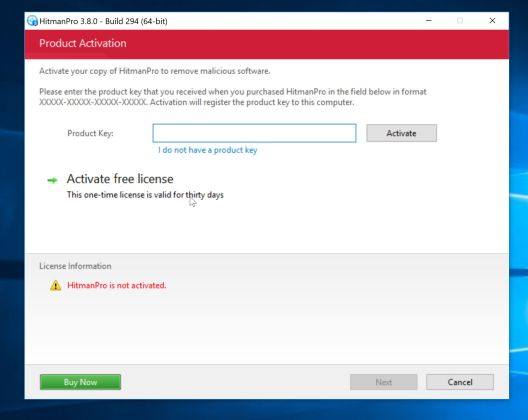
HitmanPro is a second opinion scanner, designed to rescue your computer from malware (viruses, trojans, rootkits, etc.) that have infected your computer despite all the security measures you have taken (such as anti virus software, firewalls, etc.). HitmanPro is designed to work alongside existing security programs without any conflicts. It scans the computer quickly (less than 5 minutes) and does not slow down the computer.
- You can download HitmanPro from the below link:
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download “HitmanPro”) - Double-click on the file named “HitmanPro.exe” (for 32-bit versions of Windows) or “HitmanPro_x64.exe” (for 64-bit versions of Windows).

Click on the “Next” button, to install HitmanPro on your computer.
- HitmanPro will now begin to scan your computer for malware.
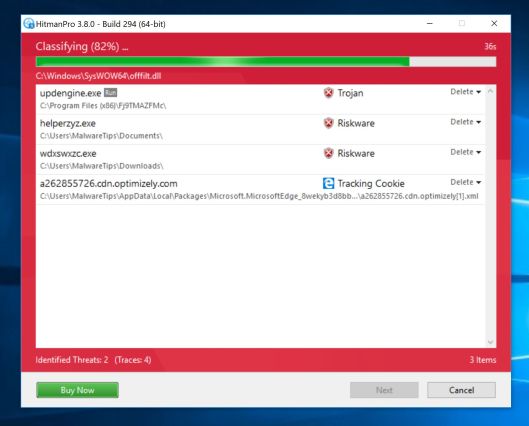
- When it has finished it will display a list of all the malware that the program found as shown in the image below. Click on the “Next” button, to remove malware.

- Click on the “Activate free license” button to begin the free 30 days trial, and remove all the malicious files from your computer.
The AdwCleaner utility will scan your computer and web browser for the malicious files, browser extensions and registry keys, that may have been installed on your computer without your knowledge.
- You can download AdwCleaner from the below link.
ADWCLEANER DOWNLOAD LINK (This link will open a new web page from where you can download “AdwCleaner”) - Before starting AdwCleaner, close your web browser, then double-click on the AdwCleaner icon.

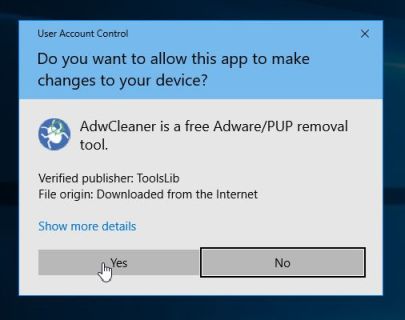
If Windows prompts you as to whether or not you wish to run AdwCleaner, please allow it to run.
- When the AdwCleaner program will open, click on the “Scan” button as shown below.

AdwCleaner will now start to search for adware and other malicious programs. - To remove the malicious files that were detected in the previous step, please click on the “Clean” button.

- AdwCleaner will prompt you to save any open files or documents, as the program will need to reboot the computer to complete the cleaning process. Please do so, and then click on the “OK” button.

When your computer reboots and you are logged in, AdwCleaner will automatically open a log file that contains the files, registry keys, and programs that were removed from your computer. Please review this log file and then close the notepad window.
Zemana AntiMalware is a cloud on-demand scanner which uses several antivirus engines to scan your computer for malware.
This step should be performed only if your issues have not been solved by the previous steps.
- You can download Zemana AntiMalware from the below link:
ZEMANA ANTIMALWARE DOWNLOAD LINK (This link will open a new web page from where you can download of “Zemana AntiMalware”) - Double-click on the file named “Zemana.AntiMalware.Setup.exe” to start the installation of Zemana AntiMalware.
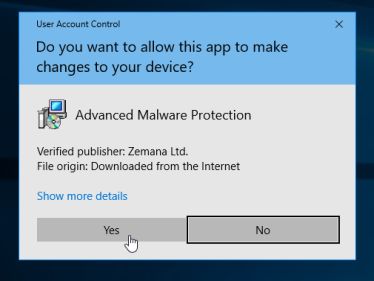
You may be presented with a User Account Control dialog asking you if you want to run this file. If this happens, you should click “Yes” to continue with the installation.
- Click on the “Next” button, to install Zemana AntiMalware on your computer.
- When Zemana AntiMalware will start, click on the “Scan” button.
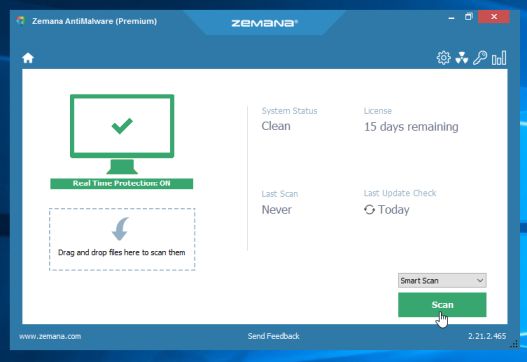
- Zemana AntiMalware will now scan computer for malicious files. This process can take up to 10 minutes.
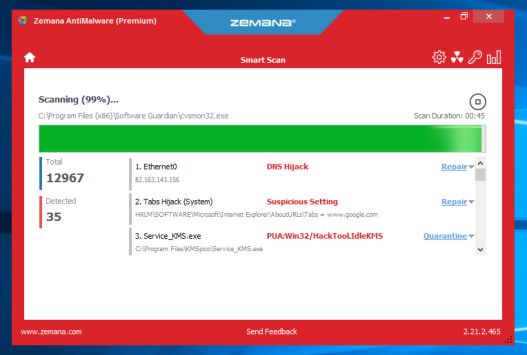
- When Zemana AntiMalware has finished it will display a list of all the malware that the program found. Click on the “Next” button, to remove the malicious files from your computer.
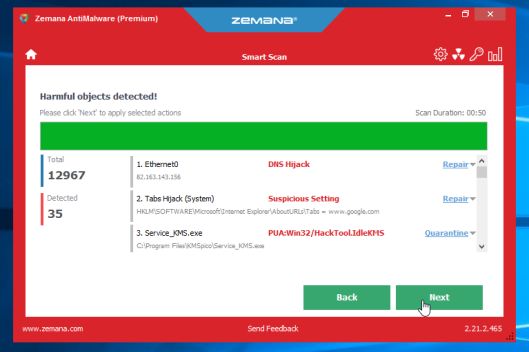
Zemana AntiMalware will now remove all the detected malicious files, and at the end a system reboot may be required to remove all traces of malware.
Last edited: