- Jan 11, 2011
- 2,007
What are Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar?
Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar are adware that displays advertisements and hijacks your browsers. Although some adwares are not harmful, they are a nuisance due to constant pop-ups and ads. It is recommended that you remove these programs as some can be malicious.
Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar installs itself, without the user's permission. Once installed, it displays various advertisements and tracks the user's surfing activity. It also redirects the user's search results to advertisement sites. In addition, this adware may also install other junk or unwanted programs onto the user's PC without the user's knowledge. The browser interface may also look different, as a result of this adware.
It is highly recommended that you remove Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar from your computer.

<h1>How to remove Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar (Removal Instructions)</h1>
If you experience any problems completing these instructions, please start a new thread in our Malware Removal Assistance forum
<h2> Step 1: Uninstall Yontoo </h2>
<h2>Step 2: Download AdwCleaner onto your desktop. </h2>
<h2>Step 3: Download and run Junkware Removal Tool to your desktop from here</h2>
<h2> Step 4: Download Malwarebytes' Anti-Malware(download link) to your desktop
 </h2>
</h2>
These instructions should remove any remaining traces of this adware. If you are still experiencing problems on your PC or would like to have one of our staff members verify that your PC is clean, please start a new thread in our <a href="https://malwaretips.com/forums/malware-removal-assistance-for-windows.10/">Malware Removal Assistance</a> forum.
How was I infected?
How can I prevent these infections?
Now that your PC is clean, I recommend you to create a new System Restore point then purge the old ones after.
For XP
How to create a Restore Point in XP
Delete all restore points except the most recent one
For Vista
Create a restore point
Delete all but the most recent restore point
For Windows 7
Create a restore point
Delete all but the most recent restore point - Click the Delete all but the most recent restore point link
Keep your system updated
I also recommend you to switch your antivirus program to a better one. Here are some suggestions:
In addition to your antivirus, you need additional protection such as a firewall and behavioural blocker.
Other steps that you may want to do to further protect your system/files:
Here are only a few suggestions that will improve your system security. Should you wish to allow us to make full recommendations and set your PC up with maximum security, please start a thread here. Our community of PC enthusiasts and experts will give you feedback and help you secure your system from future malware infections.
Should you want to try a product but don't know how it performs, here is a list of current reviews to help you decide.
Internet Explorer may be the most popular browser but it's definitely not the most secure browser. Consider using other browsers with addition add-ons to safeguard your system while browsing the internet.
Firefox is a more secure, faster browser than Internet Explorer. Firefox contains less vulnerabilities, reducing the risk of drive-by downloads. In addition, you can add the following add-ons to increase security.
Google Chrome is another good browser that is faster and more secure than Internet Explorer by having a sandbox feature. Additionally, you can add the following add-on to Chrome to heighten security.
Lastly, it is important to perform system maintenance on a regular basis. Here are a few tools and on-demand scanners that you should keep & use every 1-2 weeks to keep your system healthy.
Other than that, stay safe out there! If you have any other questions or concerns, feel free to ask
Technical details
Registry keys:
HKLM\SOFTWARE\Classes\YontooIEClient.Api
HKLM\SOFTWARE\Classes\YontooIEClient.Api.1
HKLM\SOFTWARE\Classes\YontooIEClient.Layers
HKLM\SOFTWARE\Classes\YontooIEClient.Layers.1
HKLM\SOFTWARE\Classes\AppID\YontooIEClient.DLL
Files/Folders:
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\skin
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\locale\en-US
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\locale
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\defaults\preferences
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\defaults
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\content
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com
C:\Program Files\Yontoo Layers Runtime
Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar are adware that displays advertisements and hijacks your browsers. Although some adwares are not harmful, they are a nuisance due to constant pop-ups and ads. It is recommended that you remove these programs as some can be malicious.
Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar installs itself, without the user's permission. Once installed, it displays various advertisements and tracks the user's surfing activity. It also redirects the user's search results to advertisement sites. In addition, this adware may also install other junk or unwanted programs onto the user's PC without the user's knowledge. The browser interface may also look different, as a result of this adware.
It is highly recommended that you remove Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar from your computer.

<h1>How to remove Yontoo PageRage, Yontoo Layers Client and Yontoo Toolbar (Removal Instructions)</h1>
If you experience any problems completing these instructions, please start a new thread in our Malware Removal Assistance forum
<h2> Step 1: Uninstall Yontoo </h2>
- Click Start, select Control Panel
- Click Add/Remove Programs (Or if you are using Vista/ Window 7, click Uninstall a program)
- Let the list of programs finish loading and find any program that starts with Yontoo and uninstall it
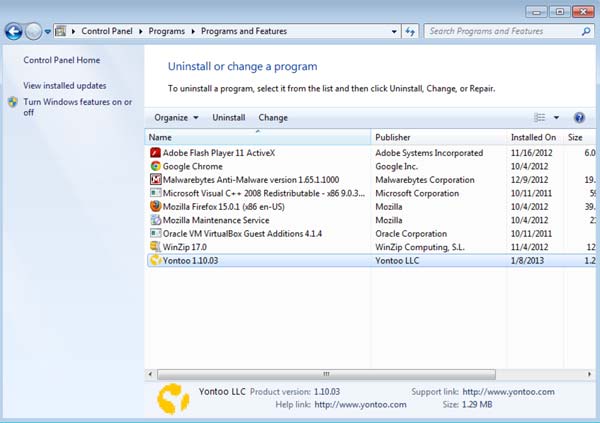
- If you don't see any Yontoo entries on the list, proceed to the next step
<h2>Step 2: Download AdwCleaner onto your desktop. </h2>
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
<h2>Step 3: Download and run Junkware Removal Tool to your desktop from here</h2>
- Turn off your antivirus software now to avoid potential conflicts
- Double-click to run the tool. For Windows Vista or 7 users, right-click the file and select Run as Administrator
- The tool will open and start scanning your system
- Please be patient as this can take a while to complete depending on your system's specifications
<h2> Step 4: Download Malwarebytes' Anti-Malware(download link) to your desktop

- Double-click mbam-setup.exe and follow the prompts to install the program.
- At the end, be sure a checkmark is placed next to
- Update Malwarebytes' Anti-Malware
- and Launch Malwarebytes' Anti-Malware
- then click Finish.
- Malwarebytes Anti-Malware will now start and you'll be prompted to start a trial period , please select '<>Decline</>'
<img title="Decline trial period in Malwarebytes Anti-Malware" src="http://malwaretips.com/images/removalguide/mbam3.PNG" alt="[Image: Decline Malwarebytes trial]" width="432" height="165" border="0" />
[*]If an update is found, it will download and install the latest version.
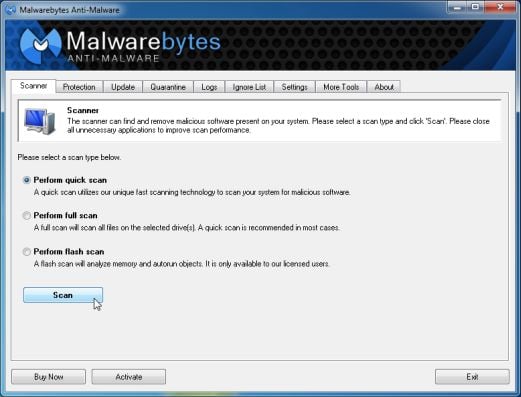
[*]Once the program has loaded, select Perform quick scan, then click Scan.
[*]When the scan is complete, click OK, then Show Results to view the results.
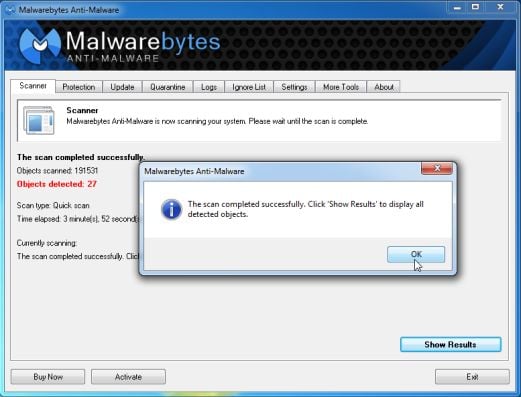
[*]Be sure that everything is Checked (ticked) and click on Remove Selected.
[*]Reboot your computer if prompted.
These instructions should remove any remaining traces of this adware. If you are still experiencing problems on your PC or would like to have one of our staff members verify that your PC is clean, please start a new thread in our <a href="https://malwaretips.com/forums/malware-removal-assistance-for-windows.10/">Malware Removal Assistance</a> forum.
How was I infected?
- Rogues can get on to computers without the user's consent through Drive-by downloads. When a user visits a compromised or infected website, the site immediately checks for any security vulnerabilities on the machine to inject the malicious code.
- Peer-to-peer (P2P) programs such as utorrent are frequently used by hackers to distribute malware
- Although the peer-to-peer programs are legitimate, the files shared are extremely dangerous. Hackers often use fake file names to trick users into downloading malware.
- Hackers can also trick the user into downloading a file, saying it is a legitimate file needed to view a video or pictures.
How can I prevent these infections?
Now that your PC is clean, I recommend you to create a new System Restore point then purge the old ones after.
For XP
How to create a Restore Point in XP
Delete all restore points except the most recent one
For Vista
Create a restore point
Delete all but the most recent restore point
For Windows 7
Create a restore point
Delete all but the most recent restore point - Click the Delete all but the most recent restore point link
Keep your system updated
- Keeping your programs (especially Adobe and Java products) updated is essential. Update Checker will notify you if any of your programs require an update.
- Microsoft releases patches for Windows and Office products regularly to patch up Windows and Office product bugs and vulnerabilities.
- Please ensure you update your system regularly and have automatic updates on. You can learn how to turn Automatic Updates on here
I also recommend you to switch your antivirus program to a better one. Here are some suggestions:
- avast! 7 Home Edition - Don't use it with Online Armor
- Avira AntiVir Personal
- BitDefender Antivirus Free Edition
- Microsoft Security Essentials
In addition to your antivirus, you need additional protection such as a firewall and behavioural blocker.
- Online Armor
- Comodo Firewall - If you are an advance user
- ZoneAlarm Free Firewall
- PC Tool Firewall Plus
Other steps that you may want to do to further protect your system/files:
- Sandboxie - "Quarantines" your browser so anything that you do in it will be isolated from your system.
- Backup important files regulary to an external hard-drive or USB
Here are only a few suggestions that will improve your system security. Should you wish to allow us to make full recommendations and set your PC up with maximum security, please start a thread here. Our community of PC enthusiasts and experts will give you feedback and help you secure your system from future malware infections.
Should you want to try a product but don't know how it performs, here is a list of current reviews to help you decide.
Internet Explorer may be the most popular browser but it's definitely not the most secure browser. Consider using other browsers with addition add-ons to safeguard your system while browsing the internet.
Firefox is a more secure, faster browser than Internet Explorer. Firefox contains less vulnerabilities, reducing the risk of drive-by downloads. In addition, you can add the following add-ons to increase security.
- KeyScramber - Encrypts your keystrokes to protect you against keyloggers that steals personal & banking information
- AdBlock - Disable/blocks advertisements on websites so you won't accidentally click on a malicious ad.
- NoScript - Disables Flash & Java contents to avoid exploits or drive-by attacks
- Web of Trust - Shows the website rating by other users and blocks dangerous and poor-rated sites
Google Chrome is another good browser that is faster and more secure than Internet Explorer by having a sandbox feature. Additionally, you can add the following add-on to Chrome to heighten security.
Lastly, it is important to perform system maintenance on a regular basis. Here are a few tools and on-demand scanners that you should keep & use every 1-2 weeks to keep your system healthy.
Other than that, stay safe out there! If you have any other questions or concerns, feel free to ask
Technical details
Registry keys:
HKLM\SOFTWARE\Classes\YontooIEClient.Api
HKLM\SOFTWARE\Classes\YontooIEClient.Api.1
HKLM\SOFTWARE\Classes\YontooIEClient.Layers
HKLM\SOFTWARE\Classes\YontooIEClient.Layers.1
HKLM\SOFTWARE\Classes\AppID\YontooIEClient.DLL
Files/Folders:
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\skin
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\locale\en-US
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\locale
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\defaults\preferences
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\defaults
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com\content
C:\Documents and Settings\Jane\Application Data\Mozilla\Firefox\Profiles\dxwlwziu.default\extensions\plugin@yontoo.com
C:\Program Files\Yontoo Layers Runtime
Last edited by a moderator: