L
LabZero
Thread author
Hello to all
I would like to introduce Wireshark Packet Sniffer : https://www.wireshark.org/
Wireshark is a software analyser of protocol or "packet sniffer" able to analyse the content of all the packs given in transit on the interface of active net. Wireshark is able to individualise the net protocols used for several types of communication and is then able to show several encapsulation.
Point of strength of this excellent analyser of protocol is certainly the flexibility: thanks to special criteria of ordering and filtering it becomes so swift to extract the data from interest with the recorded information.
The software lets choose which net interface must be analysed, if the information should be memorised or I lead, of acquiring log at other similar programs (libpcap) tcpdump, NAI Sniffer, etc.
I would like to use this tool for analyzing the traffic data of a file considered to Adware toolbar which can be found easily on many web pages and install so deceptive instead of software that really you want download
The file is called Utility Chest.exe : https://www.virustotal.com/it/file/...3f083b3641f07f32a896ae689eaaa34cb91/analysis/
Once installed Wireshark run as Administrator:
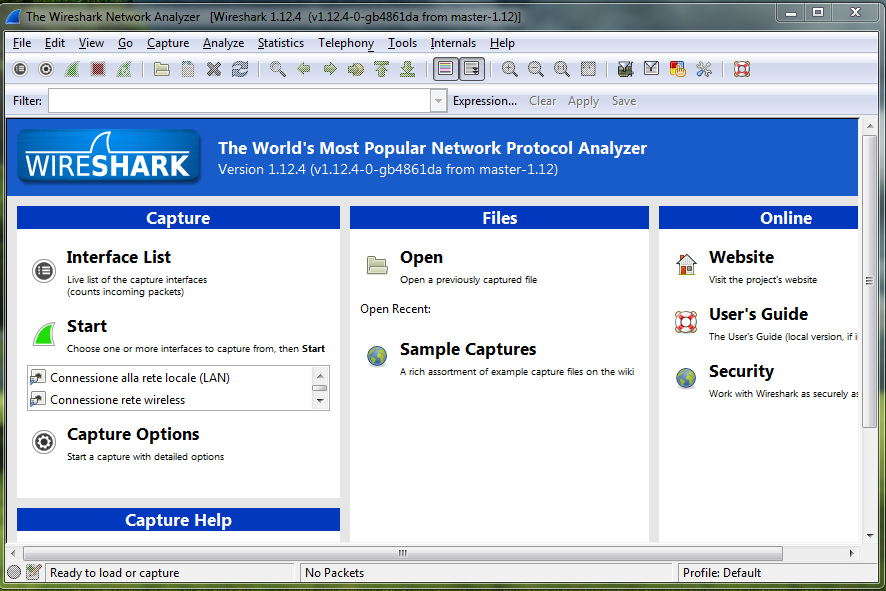
At this point, clicking on the Captures menu then click Interfaces, you can get a complete list of network interfaces that Wireshark is able to "inspect" (if you have not run the program with administrative rights, it is possible that the list is empty).
For each interface in the list, are already detected-in real-time-the number of data packets transmitted and the number of packets received. Next to each interface, the program shows the IP assigned to your system (in list you can find all network interfaces: ethernet card installed, the card used for Wi-Fi, virtual device drivers installed by VMware or other virtualization tools, interfaces are installed by details such as device driver Bluetooth USB keys).
Clicking the Details button leads to a dialog that summarizes all technical specifications of selected tab as well as offering numerous statistical data (this information is often useful to identify the interface of interest).
By clicking on the Start button, you can start the immediate capture of data in transit on the specified interface (WireShark icon will become green).
Wireshark will immediately see the information conveyed about the choice to highlight them, for ease of reading, with different colors and specifying, for each data packet, the protocol used, the source system and the destination system.
In the case of the HTTP protocol (web browsing), for example, record the whole WireShark phase of "handshake" between client and server and then start to bring back information about the request for a specific web page (GET method, requested resource, host address, browser used, language, character encoding, referrer links, cookies transmitted, etc.).
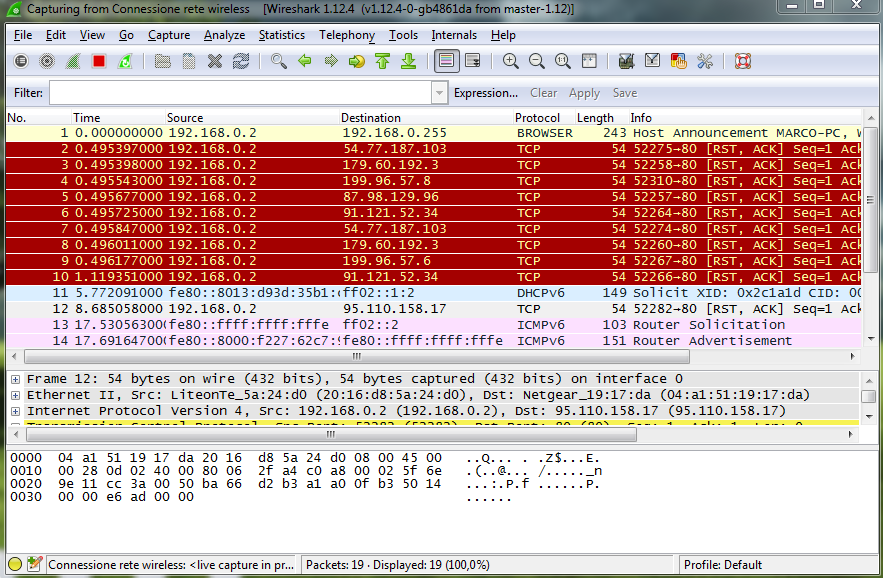
After completing the initial request with the message "GET", is the TCP protocol to take charge of the process of data transfer. Wireshark will therefore always the following process: HTTP requests data back to the server, the server uses TCP for transport to the client. The server notifies the client of the validity of your request by sending the message "HTTP OK" before sending data.
You can observe the data traffic started after running the Adware files
This is a simple example of the potential of this software in the malware analysis
I would like to introduce Wireshark Packet Sniffer : https://www.wireshark.org/
Wireshark is a software analyser of protocol or "packet sniffer" able to analyse the content of all the packs given in transit on the interface of active net. Wireshark is able to individualise the net protocols used for several types of communication and is then able to show several encapsulation.
Point of strength of this excellent analyser of protocol is certainly the flexibility: thanks to special criteria of ordering and filtering it becomes so swift to extract the data from interest with the recorded information.
The software lets choose which net interface must be analysed, if the information should be memorised or I lead, of acquiring log at other similar programs (libpcap) tcpdump, NAI Sniffer, etc.
I would like to use this tool for analyzing the traffic data of a file considered to Adware toolbar which can be found easily on many web pages and install so deceptive instead of software that really you want download
The file is called Utility Chest.exe : https://www.virustotal.com/it/file/...3f083b3641f07f32a896ae689eaaa34cb91/analysis/
Once installed Wireshark run as Administrator:
At this point, clicking on the Captures menu then click Interfaces, you can get a complete list of network interfaces that Wireshark is able to "inspect" (if you have not run the program with administrative rights, it is possible that the list is empty).
For each interface in the list, are already detected-in real-time-the number of data packets transmitted and the number of packets received. Next to each interface, the program shows the IP assigned to your system (in list you can find all network interfaces: ethernet card installed, the card used for Wi-Fi, virtual device drivers installed by VMware or other virtualization tools, interfaces are installed by details such as device driver Bluetooth USB keys).
Clicking the Details button leads to a dialog that summarizes all technical specifications of selected tab as well as offering numerous statistical data (this information is often useful to identify the interface of interest).
By clicking on the Start button, you can start the immediate capture of data in transit on the specified interface (WireShark icon will become green).
Wireshark will immediately see the information conveyed about the choice to highlight them, for ease of reading, with different colors and specifying, for each data packet, the protocol used, the source system and the destination system.
In the case of the HTTP protocol (web browsing), for example, record the whole WireShark phase of "handshake" between client and server and then start to bring back information about the request for a specific web page (GET method, requested resource, host address, browser used, language, character encoding, referrer links, cookies transmitted, etc.).
After completing the initial request with the message "GET", is the TCP protocol to take charge of the process of data transfer. Wireshark will therefore always the following process: HTTP requests data back to the server, the server uses TCP for transport to the client. The server notifies the client of the validity of your request by sending the message "HTTP OK" before sending data.
You can observe the data traffic started after running the Adware files
This is a simple example of the potential of this software in the malware analysis
