- Jan 24, 2011
- 9,378
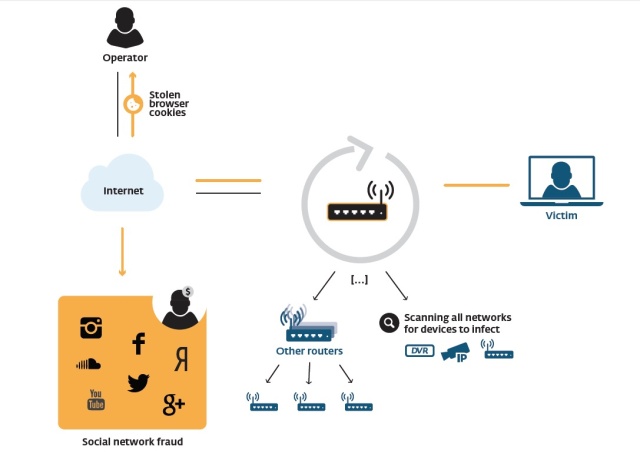
The "Linux/Moose" worm turns routers into eavesdroppers, a covert channel for social network fraud, and a platform for spreading malware to client devices that connect through them to the Internet.
A worm that targets cable and DSL modems, home routers, and other embedded computers is turning those devices into a proxy network for launching armies of fraudulent Instagram, Twitter, and Vine accounts as well as fake accounts on other social networks. The new worm can also hijack routers' DNS service to route requests to a malicious server, steal unencrypted social media cookies such as those used by Instagram, and then use those cookies to add "follows" to fraudulent accounts. This allows the worm to spread itself to embedded systems on the local network that use Linux-based operating systems.
The malware, dubbed "Linux/Moose" by Olivier Bilodeau and Thomas Dupuy of the security firm ESET Canada Research, exploits routers open to connections from the Internet via Telnet by performing brute-force login attempts using default or common administrative credentials. Once connected, the worm installs itself on the targeted device.
Moose spreads itself using a file named elan2—"élan" is the French word for moose, Bilodeau and Dupuy explained in their report. Once installed, the malware begins to watch traffic passing through the router for unencrypted cookies from Web browsers and mobile applications, which may be passed to unencrypted sites that leverage social network features:
- Twitter: twll, twid
- Facebook: c_user
- Instagram: ds_user_id
- Google: SAPISID, APISID
- Google Play / Android: LAY_ACTIVE_ACCOUNT
- Youtube: LOGIN_INFO
The main purpose of Moose, however, appears to be to create a network of covert HTTP proxies that can be used by the worm's command and control (C&C) servers to communicate with social networks. While this traffic is encrypted using HTTPS, the researchers were able to trace which sites the traffic was going to and establish a link between the traffic and fraudulent social media accounts. The proxy service is created on TCP port 2318 on the router's Internet network interface, taking incoming Web requests from a whitelisted set of IP addresses and redirecting them as HTTPS requests to social media sites. The most heavily targeted social networks were Instagram (accounting for 47 percent of the traffic analyzed by ESET), then Twitter and Vine (49 percent).
Bilodeau and Dupuy were able to monitor the accounts accessed by an infected router through the proxy service, and they saw "more than 700 Instagram accounts accessed... over about a month." They watched accounts get created through the tunnels and found that they were followed by about 40 accounts within a few hours. The accounts, in turn, were apparently used as paid "follows" for commercial accounts, including a wedding planner in Riyadh and a Brazilian site advertising paid Facebook followers.
Read more: http://arstechnica.com/security/201...-worm-turns-routers-into-social-network-bots/

