Problems in Removing Fake Police Warning Virus
- Thread starter WalterE
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Fiery
Level 1
- Jan 11, 2011
- 2,007
Hi and welcome to MalwareTips! 
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
<hr>
Please print these instruction out so that you know what you are doing
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Please print these instruction out so that you know what you are doing
- Download OTLPENet.exe to your desktop
- Download Farbar Recovery Scan Tool and save it to a flash drive.
- Ensure that you have a blank CD in the drive
- Double click OTLPENet.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
Note : If you do not know how to set your computer to boot from CD follow the steps here - Wait for the CD to detect your hardware and load the operating system
- Your system should now display a Reatogo desktop
Note : as you are running from CD it is not exactly speedy - Insert the USB with FRST
- Locate the flash drive with FRST and double click
- The tool will start to run.
- When the tool opens click Yes to disclaimer.
- Press Scan button.
- It will make a log (FRST.txt) on the flash drive. Please copy and paste it to your reply.
I have downloaded OTLPNet.exe and burned to CD.
When I try to download FRST I get told "this version of FRST is not compatible with your OS. Please use FRST64. Should I just search for that somewhere and download it?
When I try to download FRST I get told "this version of FRST is not compatible with your OS. Please use FRST64. Should I just search for that somewhere and download it?
Fiery said:Hi and welcome to MalwareTips!
I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
Please print these instruction out so that you know what you are doing
- Download OTLPENet.exe to your desktop
- Download Farbar Recovery Scan Tool and save it to a flash drive.
- Ensure that you have a blank CD in the drive
- Double click OTLPENet.exe and this will then open imgburn to burn the file to CD
- Reboot your system using the boot CD you just created.
Note : If you do not know how to set your computer to boot from CD follow the steps here- Wait for the CD to detect your hardware and load the operating system
- Your system should now display a Reatogo desktop
Note : as you are running from CD it is not exactly speedy- Insert the USB with FRST
- Locate the flash drive with FRST and double click
- The tool will start to run.
- When the tool opens click Yes to disclaimer.
- Press Scan button.
- It will make a log (FRST.txt) on the flash drive. Please copy and paste it to your reply.
Fiery said:Here is the 64 bit version
Here is the log as requested:
Scan result of Farbar Recovery Scan Tool (FRST) (x86) Version: 09-09-2013
Ran by SYSTEM on REATOGO on 11-09-2013 19:14:21
Running from D:\
Microsoft Windows XP (X86) OS Language: English(US)
Internet Explorer Version 8
Boot Mode: Recovery
The current controlset is ControlSet002
ATTENTION!:=====> If the system is bootable FRST could be run from normal or Safe mode to create a complete log.
==================== Registry (Whitelisted) ==================
HKLM\...\Run: [igfxhkcmd] - C:\WINDOWS\system32\hkcmd.exe [ ] ()
HKLM\...\Run: [igfxpers] - C:\WINDOWS\system32\igfxpers.exe [118784 2005-12-13] (Intel Corporation)
HKLM\...\Run: [SigmatelSysTrayApp] - C:\Windows\stsystra.exe [282624 2006-03-24] (SigmaTel, Inc.)
HKLM\...\Run: [SynTPEnh] - C:\Program Files\Synaptics\SynTP\SynTPEnh.exe [761947 2006-03-08] (Synaptics, Inc.)
HKLM\...\Run: [Adobe ARM] - C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe [958576 2013-04-04] (Adobe Systems Incorporated)
HKLM\...\Run: [ROC_roc_dec12] - "C:\Program Files\AVG Secure Search\ROC_roc_dec12.exe" /PROMPT /CMPID=roc_dec12
HKLM\...\Run: [MSC] - c:\Program Files\Microsoft Security Client\msseces.exe [995176 2013-06-20] ()
HKLM\...\Run: [QuickTime Task] - C:\Program Files\QuickTime\qttask.exe [421888 2012-04-18] (Apple Inc.)
HKLM\...\Runonce: [AvgUninstallURL] - cmd.exe /c start http://www.avg.com/ww.special-uninstallation-feedback-app?lic=OQBJAC0ATgAyAEcARABKAC0ANwA3AFkATQBNAC0AMgBUAFYASABBAC0AWAA0ADQAUgBSAC0ATABLAEYAQgBLAA"&"inst=NwA2AC0ANQAxADEAMgAzADYAMAAxADEALQBVADkAMAArADEALQBUAFAAKwAxAC0AWABPADMANgArADEALQBUAEIAOQArADIALQBOADEARAArADEALQBQAEwAKwA5AC0AQwBJAFAAKwAyAC0ARABEAFQAKwA0ADcANQAzADcALQBEAEQAOQAwACsAMQAtAFMAVAA5ADAAQQBQAFAAKwAxAC0AUAA5ADAATQAxADIAQwArADEALQBVADkANQArADEALQBUAEIAKwAxAC0AUAA5ADAAVABCACsAMgA"&"prod=94"&"ver=9.0.894
Winlogon\Notify\WgaLogon: WgaLogon.dll (Microsoft Corporation)
HKLM\...D6A79037F57F\InprocServer32: [Default-fastprox] ATTENTION! ====> ZeroAccess?
HKLM\...\Policies\Explorer: [NoCDBurning] 0
HKLM\...\Policies\Explorer: [NoDrives] 0
HKU\Administrator\...\Run: [ModemOnHold] - C:\Program Files\NetWaiting\netWaiting.exe
HKU\Administrator\...\RunOnce: [avg_spchecker] - "C:\Program Files\AVG\AVG9\Notification\SPChecker1.exe" /start
HKU\Default User\...\Run: [ModemOnHold] - C:\Program Files\NetWaiting\netWaiting.exe
HKU\Walter1\...\Run: [Google Update] - [x]
HKU\Walter1\...\Run: [Internet Explorer] - C:\DOCUME~1\Walter1\LOCALS~1\Temp\fvJcrgR.exe [ 2013-09-10] () <===== ATTENTION
Startup: C:\Documents and Settings\All Users\Start Menu\Programs\Startup\AVG Tray Icon.lnk
ShortcutTarget: AVG Tray Icon.lnk -> C:\Program Files\AVG\AVG9\avgtray.exe (No File)
========================== Services (Whitelisted) =================
S3 HP Port Resolver; C:\WINDOWS\system32\spool\drivers\w32x86\3\HPBPRO.EXE [81920 2005-05-20] (Hewlett-Packard Company)
S3 HP Status Server; C:\WINDOWS\system32\spool\drivers\w32x86\3\HPBOID.EXE [73728 2004-10-16] (Hewlett-Packard Company)
S2 MsMpSvc; c:\Program Files\Microsoft Security Client\MsMpEng.exe [22208 2013-06-20] ()
S2 MSSQL$MICROSOFTSMLBIZ; C:\Program Files\Microsoft SQL Server\MSSQL$MICROSOFTSMLBIZ\Binn\sqlservr.exe [9158656 2008-12-18] (Microsoft Corporation)
S3 MSSQLServerADHelper; C:\Program Files\Microsoft SQL Server\80\Tools\Binn\sqladhlp.exe [73728 2005-05-03] (Microsoft Corporation)
S2 NICCONFIGSVC; C:\Program Files\Dell\QuickSet\NICCONFIGSVC.exe [380928 2006-04-06] (Dell Inc.)
S2 S24EventMonitor; C:\Program Files\Intel\Wireless\Bin\S24EvMon.exe [946176 2006-10-18] (Intel Corporation )
S3 SQLAgent$MICROSOFTSMLBIZ; C:\Program Files\Microsoft SQL Server\MSSQL$MICROSOFTSMLBIZ\Binn\sqlagent.EXE [323584 2005-05-03] (Microsoft Corporation)
S4 WLANKEEPER; C:\Program Files\Intel\Wireless\Bin\WLKeeper.exe [290816 2006-10-18] (Intel(R) Corporation)
S4 JavaQuickStarterService; "C:\Program Files\Java\jre6\bin\jqs.exe" -service -config "C:\Program Files\Java\jre6\lib\deploy\jqs\jqs.conf" [x]
S2 *etadpug; "C:\Program Files\Google\Desktop\Install\{11961d25-6d84-e3cd-58c4-ca0936d58d33}\ \ \???\{11961d25-6d84-e3cd-58c4-ca0936d58d33}\GoogleUpdate.exe" < <==== ATTENTION (ZeroAccess)
==================== Drivers (Whitelisted) ====================
S2 AegisP; C:\Windows\System32\DRIVERS\AegisP.sys [21425 2007-02-06] (Meetinghouse Data Communications)
S1 APPDRV; C:\Windows\SYSTEM32\DRIVERS\APPDRV.SYS [16128 2005-08-12] (Dell Inc)
S2 ASCTRM; C:\Windows\System32\Drivers\ASCTRM.sys [8552 2006-07-28] (Windows (R) 2000 DDK provider)
S3 HPZid412; C:\Windows\System32\DRIVERS\HPZid412.sys [51120 2005-03-08] (HP)
S3 HPZipr12; C:\Windows\System32\DRIVERS\HPZipr12.sys [16496 2005-03-08] (HP)
S3 HPZius12; C:\Windows\System32\DRIVERS\HPZius12.sys [21744 2005-03-08] (HP)
S3 HSFHWAZL; C:\Windows\System32\DRIVERS\HSFHWAZL.sys [201600 2005-07-21] (Conexant Systems, Inc.)
S3 HSF_DPV; C:\Windows\System32\DRIVERS\HSF_DPV.sys [1035008 2005-07-21] (Conexant Systems, Inc.)
S3 ialm; C:\Windows\System32\DRIVERS\ialmnt5.sys [1364574 2005-12-13] (Intel Corporation)
S3 MBAMSwissArmy; C:\WINDOWS\system32\drivers\mbamswissarmy.sys [40776 2013-09-10] (Malwarebytes Corporation)
S0 MpFilter; C:\Windows\System32\DRIVERS\MpFilter.sys [211560 2013-06-18] (Microsoft Corporation)
S3 NETw3x32; C:\Windows\System32\DRIVERS\NETw3x32.sys [1711104 2006-10-17] (Intel® Corporation)
S2 s24trans; C:\Windows\System32\DRIVERS\s24trans.sys [12544 2006-10-19] (Intel Corporation)
S3 STHDA; C:\Windows\System32\drivers\sthda.sys [1156648 2006-03-24] (SigmaTel, Inc.)
S3 w39n51; C:\Windows\System32\DRIVERS\w39n51.sys [1429632 2006-04-27] (Intel® Corporation)
S3 catchme; \??\C:\DOCUME~1\Walter1\LOCALS~1\Temp\catchme.sys [x]
S1 SASKUTIL; \??\C:\Program Files\SUPERAntiSpyware\SASKUTIL.SYS [x]
S5 ScsiPort; C:\Windows\system32\drivers\scsiport.sys [96384 2008-04-13] (Microsoft Corporation)
S3 USBAAPL; System32\Drivers\usbaapl.sys [x]
S3 wanatw; system32\DRIVERS\wanatw4.sys [x]
==================== NetSvcs (Whitelisted) ===================
==================== One Month Created Files and Folders ========
2013-09-10 15:38 - 2013-09-10 15:38 - 00040776 _____ (Malwarebytes Corporation) C:\Windows\System32\Drivers\mbamswissarmy.sys
2013-09-10 15:38 - 2013-09-10 15:38 - 00004850 _____ C:\Windows\setupapi.log
2013-09-10 15:02 - 2013-09-10 15:02 - 00000000 ____D C:\Program Files\Google
2013-09-10 15:02 - 2013-09-10 15:02 - 00000000 ____D C:\Documents and Settings\Walter1\Local Settings\Application Data\Google
2013-09-03 17:26 - 2013-09-03 17:27 - 00014159 _____ C:\Windows\KB2862772-IE8.log
2013-09-03 17:24 - 2013-09-03 17:24 - 00000000 ____D C:\Windows\System32\MRT
2013-09-03 15:57 - 2013-09-03 15:58 - 00006630 _____ C:\Windows\KB2834904-v2.log
2013-09-03 15:57 - 2013-09-03 15:57 - 00000000 __HDC C:\Windows\$NtUninstallKB2834904-v2_WM11$
2013-09-03 15:52 - 2013-09-03 15:52 - 00009115 _____ C:\Windows\KB2859537.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00007794 _____ C:\Windows\KB2850869.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00007518 _____ C:\Windows\KB2863058.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2863058$
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2859537$
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2850869$
2013-09-03 15:51 - 2013-09-03 17:27 - 00039785 _____ C:\Windows\iis6.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00036953 _____ C:\Windows\FaxSetup.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00017736 _____ C:\Windows\ocgen.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00016927 _____ C:\Windows\tsoc.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00012188 _____ C:\Windows\comsetup.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00011252 _____ C:\Windows\msmqinst.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00007480 _____ C:\Windows\ntdtcsetup.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00006498 _____ C:\Windows\netfxocm.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00003416 _____ C:\Windows\updspapi.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00002550 _____ C:\Windows\MedCtrOC.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00002052 _____ C:\Windows\ocmsn.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00001866 _____ C:\Windows\tabletoc.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00001854 _____ C:\Windows\msgsocm.log
2013-09-03 15:51 - 2013-09-03 17:27 - 00001355 _____ C:\Windows\imsins.log
2013-09-03 15:51 - 2013-09-03 15:58 - 00001355 _____ C:\Windows\imsins.BAK
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 __HDC C:\Windows\$NtUninstallKB2849470$
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 _____ C:\Windows\setuperr.log
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 _____ C:\Windows\setupact.log
==================== One Month Modified Files and Folders =======
2013-09-10 15:42 - 2006-08-04 09:15 - 00000000 __SHD C:\Windows\CSC
2013-09-10 15:42 - 2004-08-11 18:09 - 00000159 _____ C:\Windows\wiadebug.log
2013-09-10 15:42 - 2004-08-11 18:09 - 00000049 _____ C:\Windows\wiaservc.log
2013-09-10 15:42 - 2004-08-11 18:00 - 00002206 _____ C:\Windows\System32\wpa.dbl
2013-09-10 15:38 - 2013-09-10 15:38 - 00040776 _____ (Malwarebytes Corporation) C:\Windows\System32\Drivers\mbamswissarmy.sys
2013-09-10 15:38 - 2013-09-10 15:38 - 00004850 _____ C:\Windows\setupapi.log
2013-09-10 15:02 - 2013-09-10 15:02 - 00000000 ____D C:\Program Files\Google
2013-09-10 15:02 - 2013-09-10 15:02 - 00000000 ____D C:\Documents and Settings\Walter1\Local Settings\Application Data\Google
2013-09-10 15:02 - 2004-08-11 18:13 - 01220305 _____ C:\Windows\WindowsUpdate.log
2013-09-10 14:43 - 2004-08-11 18:07 - 00567296 _____ C:\Windows\System32\PerfStringBackup.INI
2013-09-06 12:38 - 2006-08-03 06:23 - 00000278 ___SH C:\Documents and Settings\Walter1\ntuser.ini
2013-09-06 12:38 - 2004-08-11 18:20 - 00032480 _____ C:\Windows\SchedLgU.Txt
2013-09-03 17:27 - 2013-09-03 17:26 - 00014159 _____ C:\Windows\KB2862772-IE8.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00039785 _____ C:\Windows\iis6.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00036953 _____ C:\Windows\FaxSetup.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00017736 _____ C:\Windows\ocgen.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00016927 _____ C:\Windows\tsoc.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00012188 _____ C:\Windows\comsetup.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00011252 _____ C:\Windows\msmqinst.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00007480 _____ C:\Windows\ntdtcsetup.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00006498 _____ C:\Windows\netfxocm.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00003416 _____ C:\Windows\updspapi.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00002550 _____ C:\Windows\MedCtrOC.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00002052 _____ C:\Windows\ocmsn.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00001866 _____ C:\Windows\tabletoc.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00001854 _____ C:\Windows\msgsocm.log
2013-09-03 17:27 - 2013-09-03 15:51 - 00001355 _____ C:\Windows\imsins.log
2013-09-03 17:26 - 2013-09-03 17:24 - 00000000 ____D C:\Windows\System32\MRT
2013-09-03 17:24 - 2012-03-25 14:08 - 00001945 _____ C:\Windows\epplauncher.mif
2013-09-03 17:24 - 2006-08-03 06:38 - 75778376 _____ (Microsoft Corporation) C:\Windows\System32\MRT.exe
2013-09-03 16:53 - 2012-03-25 14:16 - 00000000 ____D C:\Program Files\Microsoft Security Client
2013-09-03 16:04 - 2004-08-11 18:21 - 00000000 ____D C:\Windows\Microsoft.NET
2013-09-03 15:58 - 2013-09-03 15:57 - 00006630 _____ C:\Windows\KB2834904-v2.log
2013-09-03 15:58 - 2013-09-03 15:51 - 00001355 _____ C:\Windows\imsins.BAK
2013-09-03 15:57 - 2013-09-03 15:57 - 00000000 __HDC C:\Windows\$NtUninstallKB2834904-v2_WM11$
2013-09-03 15:52 - 2013-09-03 15:52 - 00009115 _____ C:\Windows\KB2859537.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00007794 _____ C:\Windows\KB2850869.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00007518 _____ C:\Windows\KB2863058.log
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2863058$
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2859537$
2013-09-03 15:52 - 2013-09-03 15:52 - 00000000 __HDC C:\Windows\$NtUninstallKB2850869$
2013-09-03 15:52 - 2007-02-18 12:09 - 00871906 _____ C:\Windows\System32\TZLog.log
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 __HDC C:\Windows\$NtUninstallKB2849470$
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 _____ C:\Windows\setuperr.log
2013-09-03 15:51 - 2013-09-03 15:51 - 00000000 _____ C:\Windows\setupact.log
2013-09-03 15:49 - 2006-08-03 06:27 - 00000000 __SHD C:\Documents and Settings\Walter1\UserData
2013-09-03 15:48 - 2013-03-21 12:29 - 00000682 _____ C:\Documents and Settings\All Users\Desktop\CCleaner.lnk
2013-09-03 15:48 - 2013-03-21 12:29 - 00000000 ____D C:\Program Files\CCleaner
2013-09-03 15:25 - 2012-04-01 09:46 - 00692104 _____ (Adobe Systems Incorporated) C:\Windows\System32\FlashPlayerApp.exe
2013-09-03 15:25 - 2011-05-16 09:06 - 00071048 _____ (Adobe Systems Incorporated) C:\Windows\System32\FlashPlayerCPLApp.cpl
ZeroAccess:
C:\RECYCLER\S-1-5-21-2087605615-3403434741-26284291-1006\$11961d256d84e3cd58c4ca0936d58d33
ZeroAccess:
C:\Windows\assembly\GAC\Desktop.ini
Files to move or delete:
====================
C:\DOCUME~1\Walter1\LOCALS~1\Temp\fvJcrgR.exe
ZeroAccess:
C:\Documents and Settings\Walter1\Local Settings\Application Data\Google\Desktop\Install\{11961d25-6d84-e3cd-58c4-ca0936d58d33}
ZeroAccess:
C:\Program Files\Google\Desktop\Install\{11961d25-6d84-e3cd-58c4-ca0936d58d33}
C:\Documents and Settings\Walter1\g2ax_customer_downloadhelper_win32_x86.exe
C:\Documents and Settings\Walter1\Local Settings\Temp\fvJcrgR.exe
==================== Known DLLs (Whitelisted) ============
==================== Bamital & volsnap Check =================
C:\Windows\explorer.exe => MD5 is legit
C:\Windows\System32\winlogon.exe => MD5 is legit
C:\Windows\System32\svchost.exe => MD5 is legit
C:\Windows\System32\services.exe => MD5 is legit
C:\Windows\System32\User32.dll => MD5 is legit
C:\Windows\System32\userinit.exe => MD5 is legit
C:\Windows\System32\Drivers\volsnap.sys => MD5 is legit
C:\Program Files\Microsoft Security Client\MsMpEng.exe => ATTENTION: ZeroAccess. Use DeleteJunctionsIndirectory: C:\Program Files\Microsoft Security Client
==================== EXE ASSOCIATION =====================
HKLM\...\.exe: exefile => OK
HKLM\...\exefile\DefaultIcon: %1 => OK
HKLM\...\exefile\open\command: "%1" %* => OK
==================== Restore Points (XP) =====================
RP: -> 2013-09-10 14:51 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1565
RP: -> 2013-09-06 12:11 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1564
RP: -> 2013-09-03 15:50 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1563
RP: -> 2013-09-03 15:00 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1562
RP: -> 2013-08-09 11:41 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1561
RP: -> 2013-08-01 10:24 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1560
RP: -> 2013-07-28 11:01 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1559
RP: -> 2013-07-23 14:33 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1558
RP: -> 2013-07-17 09:53 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1557
RP: -> 2013-07-10 14:05 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1556
RP: -> 2013-07-10 13:46 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1555
RP: -> 2013-07-06 13:34 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1554
RP: -> 2013-06-25 18:54 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1553
RP: -> 2013-06-13 15:08 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1552
RP: -> 2013-06-12 12:32 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1551
RP: -> 2013-06-12 12:14 - 028672 _restore{46DE8921-1D39-44D2-A9E9-64119261F211}\RP1550
==================== Memory info ===========================
Percentage of memory in use: 22%
Total physical RAM: 1014.37 MB
Available physical RAM: 784.48 MB
Total Pagefile: 901.9 MB
Available Pagefile: 817.12 MB
Total Virtual: 2047.88 MB
Available Virtual: 1993.54 MB
==================== Drives ================================
Drive b: (RAMDisk) (Fixed) (Total:0.06 GB) (Free:0.06 GB) NTFS
Drive c: () (Fixed) (Total:107.24 GB) (Free:88.53 GB) NTFS ==>[Drive with boot components (Windows XP)]
Drive d: (HITMANPRO) (Removable) (Total:14.88 GB) (Free:14.87 GB) FAT32
Drive x: (ReatogoPE) (CDROM) (Total:0.43 GB) (Free:0 GB) CDFS
==================== MBR & Partition Table ==================
========================================================
Disk: 0 (Size: 110 GB) (Disk ID: 41AB2316)
Partition 1: (Not Active) - (Size=39 MB) - (Type=DE)
Partition 2: (Active) - (Size=107 GB) - (Type=07 NTFS)
Partition 3: (Not Active) - (Size=3 GB) - (Type=DB)
========================================================
Disk: 1 (Size: 15 GB) (Disk ID: 599055E5)
Partition 1: (Active) - (Size=15 GB) - (Type=0C)
==================== End Of Log ============================
Fiery said:Here is the 64 bit version
http://download.bleepingcomputer.com/farbar/FRST64.exe
Here is the FRST.txt as an attachment. Not sure how I am really supposed to send this[attachment=5600]
Attachments
Fiery
Level 1
- Jan 11, 2011
- 2,007
Hi,
On your clean PC, download the following file by right-clicking it and select save as
[attachment=5604]
and save it onto your flash drive.
Then, boot to system recovery, plug in your flash drive, open FRST and click fix. Post the generated log.
Attempt to boot normally. If successful,
Download TDSSkiller from here
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
On your clean PC, download the following file by right-clicking it and select save as
[attachment=5604]
and save it onto your flash drive.
Then, boot to system recovery, plug in your flash drive, open FRST and click fix. Post the generated log.
Attempt to boot normally. If successful,
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.
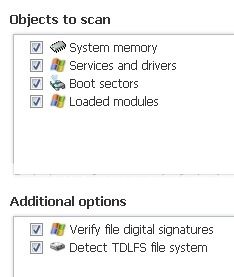
- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Attachments
Sorry. Before I start on this, you need to better explain "boot to system recovery" for me.
Fiery said:Hi,
On your clean PC, download the following file by right-clicking it and select save as
and save it onto your flash drive.
Then, boot to system recovery, plug in your flash drive, open FRST and click fix. Post the generated log.
Attempt to boot normally. If successful,
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
WalterE said:Sorry. Before I start on this, you need to better explain "boot to system recovery" for me. I am dealing with a Dell Inspiron 6400 if that helps.
Fiery said:Hi,
On your clean PC, download the following file by right-clicking it and select save as
and save it onto your flash drive.
Then, boot to system recovery, plug in your flash drive, open FRST and click fix. Post the generated log.
Attempt to boot normally. If successful,
Download TDSSkiller from here
- Double-Click on TDSSKiller.exe to run the application
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.

- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually C:\ folder in the form of TDSSKiller.[Version]_[Date]_[Time]_log.txt
Download Malwarebytes Anti-Rootkit from here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
[attachment=5606]Attached is the generated log from FRST "fix". I can now boot normally but am unable to connect to the internet in spite of having an "excellent" wireless signal strength. Can I download TDSSKiller to the clean PC, put it on the flash drive and try it on the infected machine?
Fiery said:Sorry for the confusion. By System recovery, i mean the otlpe environment in which you ran the farbar tool initially. So instead of clicking scan this time, you click Fix. But make sure you have the fixlist.txt file o your USB before you click Fix.
Attachments
I have gone ahead per my suggestion above. Here are the TDSSKiller log texts
WalterE said:Attached is the generated log from FRST "fix". I can now boot normally but am unable to connect to the internet in spite of having an "excellent" wireless signal strength. Can I download TDSSKiller to the clean PC, put it on the flash drive and try it on the infected machine?
Fiery said:Sorry for the confusion. By System recovery, i mean the otlpe environment in which you ran the farbar tool initially. So instead of clicking scan this time, you click Fix. But make sure you have the fixlist.txt file o your USB before you click Fix.
Attachments
WalterE said:Attached is the generated log from FRST "fix". I can now boot normally but am unable to connect to the internet in spite of having an "excellent" wireless signal strength. Can I download TDSSKiller to the clean PC, put it on the flash drive and try it on the infected machine?
Fiery said:Sorry for the confusion. By System recovery, i mean the otlpe environment in which you ran the farbar tool initially. So instead of clicking scan this time, you click Fix. But make sure you have the fixlist.txt file o your USB before you click Fix.
I have gone ahead and completed the suggested steps with TDSSKiller and Malwarebytes Anti-Rootkit. This message is coming from my previously infected machine. Attached are the MBAR logs. You guys are amazing, thanks for everything.
Attachments
Fiery
Level 1
- Jan 11, 2011
- 2,007
Hi,
Glad you got your Desktop back . We are not quite done yet...
. We are not quite done yet...
Step 1
Please re-run TDSSkiller but this time, if the following entry appears, choose delete. If Delete is not available, choose quarantine .
etadpug ( Rootkit.Win32.PMax.gen )
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - skipped by user
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - User select action: Skip
Step 2
Afterwards, download the following file by right-clicking it and select save as
[attachment=5612]
and save it onto your flash drive with the Farbar tool.
Then in normal mode, plug in your flash drive, open FRST and click fix. Post the generated log.
Step 3
Please download AdwCleaner by Xplode onto your desktop.
Step 4
Download & SAVE to your Desktop RogueKiller or from here
Step 5
Lastly, Please download SystemLook from one of the links below and save it to your Desktop.
Download Mirror #1
Download Mirror #2
Note: The log can also be found on your Desktop entitled SystemLook.txt
Glad you got your Desktop back
Step 1
Please re-run TDSSkiller but this time, if the following entry appears, choose delete. If Delete is not available, choose quarantine .
etadpug ( Rootkit.Win32.PMax.gen )
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - skipped by user
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - User select action: Skip
Step 2
Afterwards, download the following file by right-clicking it and select save as
[attachment=5612]
and save it onto your flash drive with the Farbar tool.
Then in normal mode, plug in your flash drive, open FRST and click fix. Post the generated log.
Step 3
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Step 4
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Step 5
Lastly, Please download SystemLook from one of the links below and save it to your Desktop.
Download Mirror #1
Download Mirror #2
- Double-click SystemLook.exe to run it.
- Copy the content of the following codebox into the main textfield:
:service
gupdate
etadpug
:Regfind
toober
- Click the Look button to start the scan.
- When finished, a notepad window will open with the results of the scan. Please post this log in your next reply.
Note: The log can also be found on your Desktop entitled SystemLook.txt
Attachments
I have worked my way through these steps and here are the log files generated
Fiery said:Hi,
Glad you got your Desktop back. We are not quite done yet...
Step 1
Please re-run TDSSkiller but this time, if the following entry appears, choose delete. If Delete is not available, choose quarantine .
etadpug ( Rootkit.Win32.PMax.gen )
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - skipped by user
11:13:29.0909 0x0f90 \Device\Harddisk1\DR4 ( TDSS File System ) - User select action: Skip
Step 2
Afterwards, download the following file by right-clicking it and select save as
and save it onto your flash drive with the Farbar tool.
Then in normal mode, plug in your flash drive, open FRST and click fix. Post the generated log.
Step 3
Please download AdwCleaner by Xplode onto your desktop.
- Close all open programs and internet browsers.
- Double click on AdwCleaner.exe to run the tool(For Vista or Windows 7, right-click and select Run as Administrator to start)
- Click delete
- Please post the content of that logfile with your next reply.
- You can find the logfile at C:\AdwCleaner[S1].txt
Step 4
Download & SAVE to your Desktop RogueKiller or from here
- Quit all programs that you may have started.
- Please disconnect any USB or external drives from the computer before you run this scan!
- For Vista or Windows 7, right-click and select Run as Administrator to start
- Wait until Prescan has finished, then click on "Scan" button
- Wait until the Status box shows "Scan Finished"
- Click delete and wait until it saids deleting finished
- Click on "Report" and copy/paste the content of the Notepad into your next reply.
- The log should be found in RKreport[1].txt on your Desktop
Exit/Close RogueKiller+
Step 5
Lastly, Please download SystemLook from one of the links below and save it to your Desktop.
Download Mirror #1
Download Mirror #2
- Double-click SystemLook.exe to run it.
- Copy the content of the following codebox into the main textfield:
:service
gupdate
etadpug
:Regfind
toober
- Click the Look button to start the scan.
- When finished, a notepad window will open with the results of the scan. Please post this log in your next reply.
Note: The log can also be found on your Desktop entitled SystemLook.txt
Attachments
Fiery
Level 1
- Jan 11, 2011
- 2,007
Hi,
Open notepad and copy & paste the following:
Click File > Save As. Under file type, select All files and name the file fix.bat and save it on your Desktop. Afterwards, double click it and the command prompt should pop-up momentarily and disappear.
Afterwards, please head back to OTLPE and run another FRST log so I can the script worked or not.
Open notepad and copy & paste the following:
@echo off
sc stop gupdate
sc delete gupdate
sc stop etadpug
sc delete etadpug
exit
Click File > Save As. Under file type, select All files and name the file fix.bat and save it on your Desktop. Afterwards, double click it and the command prompt should pop-up momentarily and disappear.
Afterwards, please head back to OTLPE and run another FRST log so I can the script worked or not.
Here is the latest FRST scan log run from OTLPE
Fiery said:Hi,
Open notepad and copy & paste the following:
@echo off
sc stop gupdate
sc delete gupdate
sc stop etadpug
sc delete etadpug
exit
Click File > Save As. Under file type, select All files and name the file fix.bat and save it on your Desktop. Afterwards, double click it and the command prompt should pop-up momentarily and disappear.
Afterwards, please head back to OTLPE and run another FRST log so I can the script worked or not.
Attachments
Fiery
Level 1
- Jan 11, 2011
- 2,007
Download the following file by right-clicking it and select save as
[attachment=5639]
and save it onto your flash drive.
Then, boot to OTLPE, plug in your flash drive, open FRST and click fix. Post the generated log.
After, update Malwarebytes and perform a Quick Scan.
lastly, Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
[attachment=5639]
and save it onto your flash drive.
Then, boot to OTLPE, plug in your flash drive, open FRST and click fix. Post the generated log.
After, update Malwarebytes and perform a Quick Scan.
lastly, Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
Attachments
Here are the latest FRST log and the ESET scan report
Fiery said:Download the following file by right-clicking it and select save as
and save it onto your flash drive.
Then, boot to OTLPE, plug in your flash drive, open FRST and click fix. Post the generated log.
After, update Malwarebytes and perform a Quick Scan.
lastly, Run Eset NOD32 Online AntiVirus here
Note: You will need to use Internet Explorer for this scan.
Vista / 7 users: You will need to to right-click on the Internet Explorer icon and select Run as Administrator
- Tick the box next to YES, I accept the Terms of Use.
- Click Start
- When asked, allow the activex control to install
- Disable your current antivirus software. You can usually do this with its Notfication Tray icon near the clock.
- Make sure that the option "Remove found threats" is Un-checked, and the following Advance Settings are Checked
- Scan unwanted applications
- Scan for potentially unsafe applications
- Enable Anti-Stealth Technology
- Click Scan
- Wait for the scan to finish
- When the scan is done, if it shows a screen that says "Threats found!", then click "List of found threats", and then click "Export to text file..."
- Save that text file on your desktop. Copy and paste the contents of that log in your next reply to this topic.
- The log can also be found in logfile located at C:\Program Files\ESET\Eset Online Scanner\log.txt
Attachments
Similar threads
- Locked
- Replies
- 11
- Views
- 633
- Replies
- 0
- Views
- 1,193