D
Deleted member 21043
Thread author
Hello everyone!
Today I am going to give you a method of securing your system whilst browsing the internet. For this thread, I will be using the sandboxing software, Sandboxie, and explain how sandboxing your browser protects your system.
1. Why sandboxing your browser is a good idea
- If you download a suspicious application, you can have it executed in the sandbox with a few clicks.
- If you get infected by a drive-by-drive download (of course without being aware of it occuring), the sandbox will be compromised as opposed to it affecting your real system/your documents, and then you can reset the sandbox and go back to to normal.
- If you download malicious software (e.g. rootkit, ransomware, bootkit, trojan downloader) and run it, everything will happen inside of the sandbox instead of affecting your real system. This is really good, as it allows you to see how a program behaves before allowing it non-virtualized.
- If you get infected by a keylogger on your main system (without being aware, if you were aware of course you'd get the infection cleaned), it won't be able to access information from the browser which is being sandboxed.
2. How to install Sandboxie
Before you can install Sandboxie, you need to download the installer. You can do so by navigating to the official website and downloading it: http://www.sandboxie.com/index.php?DownloadSandboxie http://www.sandboxie.com/index.php?AllVersions
You'll need to download the correct version depending on if you're on a 32-bit or 64-bit version of Windows.
After the installer has downloaded, open it up. **It will require administrator privileges to run, you'll be required to confirm the UAC popup if you have UAC enabled**.
After confirming the UAC alert, Sandboxie should present the first stage of the installer which is choosing the language out of the supported languages. Once you have finished setting your language, click OK. The License Agreement will then be displayed, make sure to read through it; reading through the License Agreements/Privacy Policies of security software is very important. If you are happy with the License Agreement, you can click 'I Agree'. Sandboxie will then allow you to configure the directory Sandboxie will be installed too, I recommend leaving the path as the default one. After you have finished with that step, Sandboxie will proceed to install.
Once installation has complete, you have a very important stage to have completed - installing and activating the Sandboxie Kernel-Mode driver (Sandboxie name it "system-level"). I recommend you temporarily disable any other security software you have active currently, because they may interfere with the process and block the loading of the driver.
In the below spoiler, I have made a screenshot and scaled it down for you to see what the installer now looks like for me for this stage:
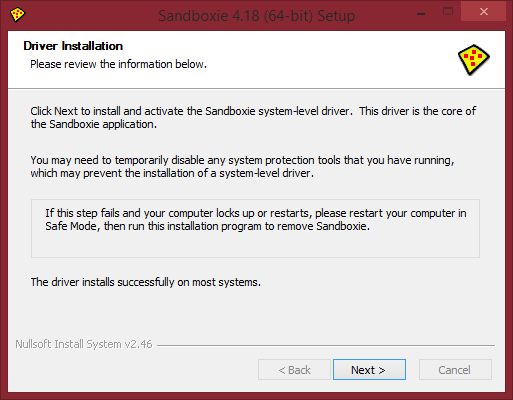
Select 'Next >'. If it's a success, you'll be presented the finished stage view. You can now exit out of the installer, installation has completed successfully.
After installation has finished, when Sandboxie is opened/opens up, you'll be prompted with a software compatibility list. The way it works is Sandboxie will try to enhance compatibility between the programs in the list (if possible).
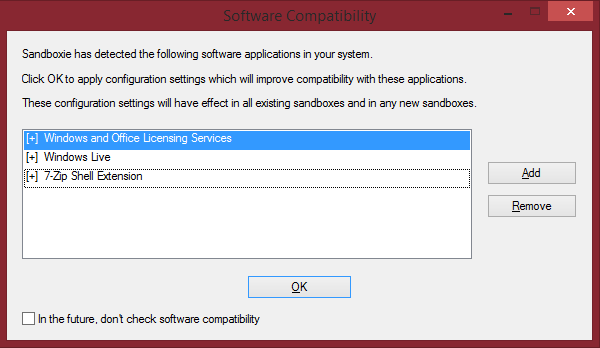
Since I do not mind, I am going to hit OK, enhancing compatbility with the items in the list.
The Sandboxie tutorial window should now open, you can go through these steps, read the information shown on the window since it can help you.
3. How to sandbox your browser using Sandboxie
When you were setting up Sandboxie, a desktop shortcut should have been made by Sandboxie, with the filename, "Sandboxed Web Browser". The target path for the shortcut (for me) would be: "C:\Program Files\Sandboxie\Start.exe" default_browser

Open up the shortcut (double click/right click > Open) and the default web browser should be executed in the Sandbox.
My default browser on my system is Firefox, therefore Firefox was executed in the Sandbox when I opened the shortcut up. If you run a program in the Sandbox, you may notice the yellow border around the application - this represents that the program is being sandboxed:
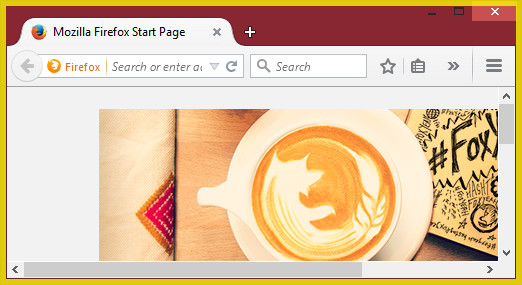
If you wish to sandbox a different browser installed on your system (or if you misplaced the desktop shortcut), you can open Sandboxie via the System Tray icon (double click it).
From the Sandboxie main window, go to Sandbox > DefaultBox > Run Sandboxed > Run Any Program
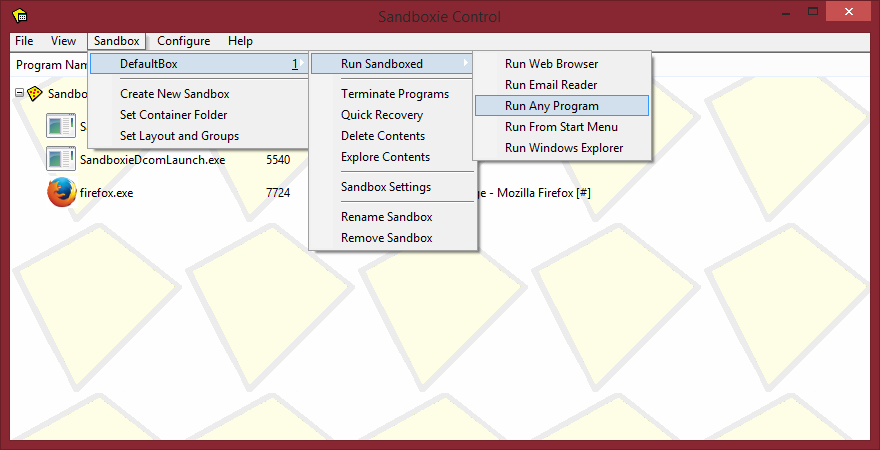
A new window will be displayed. Enter the path to the executable you wish to run sandboxed, I will put the path to Google Chrome (for my system).
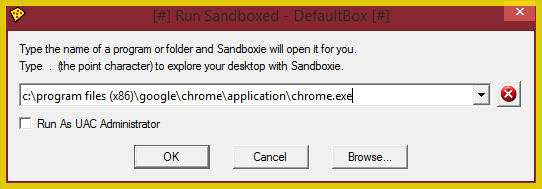
Once you have entered the path to the executable you wish to run sandboxed, click OK.
Google Chrome now launches in the Sandbox.
We can see it's running in the sandbox from the main window, it's listed:
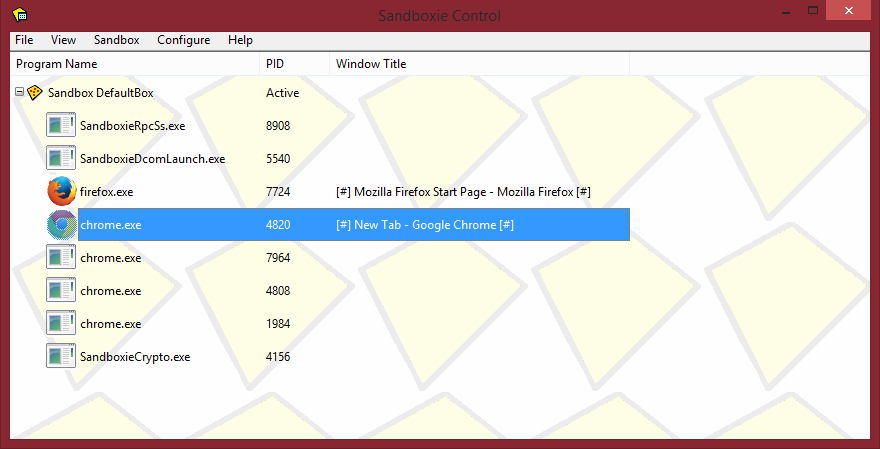
When you are finished with the Sandbox, you can Empty the can 'Delete Contents'. The option is under Sandbox > DefaultBox. After this, if you'd like, you can Delete Sandbox (also under Sandbox > DefaultBox). You can access the dropdown menu from right click on the system-tray icon, also.
You can terminate a program running in the sandbox by right clicking on the item in the programs list and selecting 'Terminate Program' option or by using Sandbox > DefaultBox > Terminate Programs option.
Anything that happens now regarding the browser will occur in the Sandbox. If you get infected via drive-by-downloads, it will all be inside of the sandbox. However, exploits are possible; it's technically possible for an exploit to allow malware to escape the sandbox. However, there are currently no known exploits for sandboxie and the developmet team for the product are extremely intelligent, hardworking and quick to fix bugs so hopefully there won't be an issue anytime soon.
4. Warnings
- Data theft can still occur in the sandbox! (If you run malware in the sandbox, it can steal data from the web browser being sandboxed).
- Sandbox uses a kernel-mode driver - if there is an issue with it, it can cause BSOD crashes.
- Some software/malware is Anti-VM/Anti-Sandbox, meaning it may attempt to trick you by pretending to do no harm but then when used on a real, non-virtualized environment, it causes harm to the system/users documents.
- If the sandbox isn't set up correctly, and the sandbox is infected, it can still steal. Make sure to block off directories from access.
- Make sure programs in the sandbox cannot access directories like C:\Windows.
Cheers.
Today I am going to give you a method of securing your system whilst browsing the internet. For this thread, I will be using the sandboxing software, Sandboxie, and explain how sandboxing your browser protects your system.
1. Why sandboxing your browser is a good idea
- If you download a suspicious application, you can have it executed in the sandbox with a few clicks.
- If you get infected by a drive-by-drive download (of course without being aware of it occuring), the sandbox will be compromised as opposed to it affecting your real system/your documents, and then you can reset the sandbox and go back to to normal.
- If you download malicious software (e.g. rootkit, ransomware, bootkit, trojan downloader) and run it, everything will happen inside of the sandbox instead of affecting your real system. This is really good, as it allows you to see how a program behaves before allowing it non-virtualized.
- If you get infected by a keylogger on your main system (without being aware, if you were aware of course you'd get the infection cleaned), it won't be able to access information from the browser which is being sandboxed.
2. How to install Sandboxie
Before you can install Sandboxie, you need to download the installer. You can do so by navigating to the official website and downloading it: http://www.sandboxie.com/index.php?DownloadSandboxie http://www.sandboxie.com/index.php?AllVersions
You'll need to download the correct version depending on if you're on a 32-bit or 64-bit version of Windows.
After the installer has downloaded, open it up. **It will require administrator privileges to run, you'll be required to confirm the UAC popup if you have UAC enabled**.
After confirming the UAC alert, Sandboxie should present the first stage of the installer which is choosing the language out of the supported languages. Once you have finished setting your language, click OK. The License Agreement will then be displayed, make sure to read through it; reading through the License Agreements/Privacy Policies of security software is very important. If you are happy with the License Agreement, you can click 'I Agree'. Sandboxie will then allow you to configure the directory Sandboxie will be installed too, I recommend leaving the path as the default one. After you have finished with that step, Sandboxie will proceed to install.
Once installation has complete, you have a very important stage to have completed - installing and activating the Sandboxie Kernel-Mode driver (Sandboxie name it "system-level"). I recommend you temporarily disable any other security software you have active currently, because they may interfere with the process and block the loading of the driver.
In the below spoiler, I have made a screenshot and scaled it down for you to see what the installer now looks like for me for this stage:

Select 'Next >'. If it's a success, you'll be presented the finished stage view. You can now exit out of the installer, installation has completed successfully.
After installation has finished, when Sandboxie is opened/opens up, you'll be prompted with a software compatibility list. The way it works is Sandboxie will try to enhance compatibility between the programs in the list (if possible).

Since I do not mind, I am going to hit OK, enhancing compatbility with the items in the list.
The Sandboxie tutorial window should now open, you can go through these steps, read the information shown on the window since it can help you.
3. How to sandbox your browser using Sandboxie
When you were setting up Sandboxie, a desktop shortcut should have been made by Sandboxie, with the filename, "Sandboxed Web Browser". The target path for the shortcut (for me) would be: "C:\Program Files\Sandboxie\Start.exe" default_browser

Open up the shortcut (double click/right click > Open) and the default web browser should be executed in the Sandbox.
My default browser on my system is Firefox, therefore Firefox was executed in the Sandbox when I opened the shortcut up. If you run a program in the Sandbox, you may notice the yellow border around the application - this represents that the program is being sandboxed:

If you wish to sandbox a different browser installed on your system (or if you misplaced the desktop shortcut), you can open Sandboxie via the System Tray icon (double click it).

From the Sandboxie main window, go to Sandbox > DefaultBox > Run Sandboxed > Run Any Program

A new window will be displayed. Enter the path to the executable you wish to run sandboxed, I will put the path to Google Chrome (for my system).

Once you have entered the path to the executable you wish to run sandboxed, click OK.
Google Chrome now launches in the Sandbox.
We can see it's running in the sandbox from the main window, it's listed:

When you are finished with the Sandbox, you can Empty the can 'Delete Contents'. The option is under Sandbox > DefaultBox. After this, if you'd like, you can Delete Sandbox (also under Sandbox > DefaultBox). You can access the dropdown menu from right click on the system-tray icon, also.
You can terminate a program running in the sandbox by right clicking on the item in the programs list and selecting 'Terminate Program' option or by using Sandbox > DefaultBox > Terminate Programs option.
Anything that happens now regarding the browser will occur in the Sandbox. If you get infected via drive-by-downloads, it will all be inside of the sandbox. However, exploits are possible; it's technically possible for an exploit to allow malware to escape the sandbox. However, there are currently no known exploits for sandboxie and the developmet team for the product are extremely intelligent, hardworking and quick to fix bugs so hopefully there won't be an issue anytime soon.
4. Warnings
- Data theft can still occur in the sandbox! (If you run malware in the sandbox, it can steal data from the web browser being sandboxed).
- Sandbox uses a kernel-mode driver - if there is an issue with it, it can cause BSOD crashes.
- Some software/malware is Anti-VM/Anti-Sandbox, meaning it may attempt to trick you by pretending to do no harm but then when used on a real, non-virtualized environment, it causes harm to the system/users documents.
- If the sandbox isn't set up correctly, and the sandbox is infected, it can still steal. Make sure to block off directories from access.
- Make sure programs in the sandbox cannot access directories like C:\Windows.
Cheers.
Last edited by a moderator:
