Removing unwanted 'Search' tab in Chrome.
- Thread starter acbeaton
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
- Oct 5, 2012
- 2,697
Hi and welcome to the malwaretips.com forums!
I'm Kuttus and I am going to try to assist you with your problem. Please take note of the below:
Before we start:
Please be aware that removing malware is a potentially hazardous undertaking. I will take care not to knowingly suggest courses of action that might damage your computer. However it is impossible for me to foresee all interactions that may happen between the software on your computer and those we'll use to clear you of infection, and I cannot guarantee the safety of your system. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system, or to necessitate you taking your computer to a repair shop.
Because of this, I advise you to backup any personal files and folders before you start.
<hr />
STEP 1: Run the below OTL fix
<ol><li>Start <>OTL.exe</></li>
<li>Copy/paste the following text written <>inside of the code box</> into the <>Custom Scans/Fixes</> box located at the bottom of OTL
<>NOTICE: This script was written specifically for this user, for use on that particular machine. Running this on another machine may cause damage to your operating system</></li>
<li>Then click the <>Run Fix</> button at the top</li>
<li>Let the program run unhindered, reboot when it is done</li>
<li>Attach the new log produced by OTL (C:\_OTL)</li>
</ol>
<hr />
I'm Kuttus and I am going to try to assist you with your problem. Please take note of the below:
- I will start working on your malware issues, this may or may not, solve other issues you have with your machine.
- The fixes are specific to your problem and should only be used for this issue on this machine!
- The process is not instant. Please continue to review my answers until I tell you your machine is clear. Absence of symptoms does not mean that everything is clear.
- If you don't know, stop and ask! Don't keep going on.
- Please reply to this thread. Do not start a new topic.
- Refrain from running self fixes as this will hinder the malware removal process.
- It may prove beneficial if you print of the following instructions or save them to notepad as I post them.
Before we start:
Please be aware that removing malware is a potentially hazardous undertaking. I will take care not to knowingly suggest courses of action that might damage your computer. However it is impossible for me to foresee all interactions that may happen between the software on your computer and those we'll use to clear you of infection, and I cannot guarantee the safety of your system. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system, or to necessitate you taking your computer to a repair shop.
Because of this, I advise you to backup any personal files and folders before you start.
<hr />
STEP 1: Run the below OTL fix
<ol><li>Start <>OTL.exe</></li>
<li>Copy/paste the following text written <>inside of the code box</> into the <>Custom Scans/Fixes</> box located at the bottom of OTL
Code:
:OTL
IE:64bit: - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.searchya.com/?f=1&a=dnldyho&c...545868&ir=
IE:64bit: - HKLM\..\SearchScopes,DefaultScope = {0633EE93-D776-472f-A0FF-E1416B8B2E3A}
IE:64bit: - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://www.searchya.com/?q={searchTerms}...545868&ir=
IE:64bit: - HKLM\..\SearchScopes\{5BD8EF88-D60D-AD5B-07E3-2AB749C6BBAD}: "URL" = http://www.bing.com/search?q={searchTerms}&FORM=IE8SRC
IE - HKLM\SOFTWARE\Microsoft\Internet Explorer\Main,Start Page = http://www.searchya.com/?f=1&a=dnldyho&c...545868&ir=
IE - HKLM\..\SearchScopes,DefaultScope = {0633EE93-D776-472f-A0FF-E1416B8B2E3A}
IE - HKLM\..\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}: "URL" = http://www.searchya.com/?q={searchTerms}...545868&ir=
IE - HKLM\..\SearchScopes\{3AF48E71-8792-2E43-F4A1-4F2C909F16E2}: "URL" = http://www.bing.com/search?q={searchTerms}&FORM=IE8SRC
O2:64bit: - BHO: (LastPass Vault) - {95D9ECF5-2A4D-4550-BE49-70D42F71296E} - C:\Program Files (x86)\LastPass\LPToolbar_x64.dll ()
O2 - BHO: (LastPass Vault) - {95D9ECF5-2A4D-4550-BE49-70D42F71296E} - C:\Program Files (x86)\LastPass\LPToolbar.dll ()
O3:64bit: - HKLM\..\Toolbar: (LastPass Toolbar) - {9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} - C:\Program Files (x86)\LastPass\LPToolbar_x64.dll ()
O3 - HKLM\..\Toolbar: (LastPass Toolbar) - {9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} - C:\Program Files (x86)\LastPass\LPToolbar.dll ()
O3 - HKCU\..\Toolbar\WebBrowser: (no name) - {724D43A0-0D85-11D4-9908-00400523E39A} - No CLSID value found.
O3 - HKCU\..\Toolbar\WebBrowser: (no name) - {EEE6C35B-6118-11DC-9C72-001320C79847} - No CLSID value found.
O4 - HKCU..\Run: [ConduitFloatingPlugin_kdfbddbdpnahdahmamlolacimfdbeckk] C:\Program Files (x86)\Conduit\CT3281675\plugins\ConduitFloatingPlugin.dll (Conduit Ltd.)
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktopChanges = 1
O6 - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer: NoActiveDesktop = 1
[2013/03/13 11:53:42 | 000,000,000 | ---D | C] -- C:\Users\Alistair\AppData\Local\Conduit
[2013/03/13 11:52:59 | 000,000,000 | ---D | C] -- C:\Program Files (x86)\Conduit
[2013/02/25 14:33:16 | 000,000,000 | ---D | C] -- C:\Users\Alistair\AppData\Roaming\Searchya
:Files
C:\Users\Alistair\AppData\Local\Conduit
C:\Program Files (x86)\Conduit
C:\Users\Alistair\AppData\Roaming\Searchya
:commands
[emptytemp]
[reboot]<li>Then click the <>Run Fix</> button at the top</li>
<li>Let the program run unhindered, reboot when it is done</li>
<li>Attach the new log produced by OTL (C:\_OTL)</li>
</ol>
<hr />
Last edited by a moderator:
Thank you for your response. The .log file you asked for in C:\_OTL is rejected by this system when I try to attach it so I have copied and pasted it instead.
Copy referred to:
All processes killed
========== OTL ==========
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\\DefaultScope| /E : value set successfully!
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{5BD8EF88-D60D-AD5B-07E3-2AB749C6BBAD}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5BD8EF88-D60D-AD5B-07E3-2AB749C6BBAD}\ not found.
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\\DefaultScope| /E : value set successfully!
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{3AF48E71-8792-2E43-F4A1-4F2C909F16E2}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3AF48E71-8792-2E43-F4A1-4F2C909F16E2}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
C:\Program Files (x86)\LastPass\LPToolbar_x64.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
C:\Program Files (x86)\LastPass\LPToolbar.dll moved successfully.
64bit-Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5}\ deleted successfully.
File C:\Program Files (x86)\LastPass\LPToolbar_x64.dll not found.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5}\ deleted successfully.
File C:\Program Files (x86)\LastPass\LPToolbar.dll not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{724D43A0-0D85-11D4-9908-00400523E39A} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{724D43A0-0D85-11D4-9908-00400523E39A}\ not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{EEE6C35B-6118-11DC-9C72-001320C79847} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{EEE6C35B-6118-11DC-9C72-001320C79847}\ not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\\ConduitFloatingPlugin_kdfbddbdpnahdahmamlolacimfdbeckk deleted successfully.
C:\Program Files (x86)\Conduit\CT3281675\plugins\ConduitFloatingPlugin.dll moved successfully.
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\\NoActiveDesktopChanges deleted successfully.
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\\NoActiveDesktop deleted successfully.
C:\Users\Alistair\AppData\Local\Conduit folder moved successfully.
C:\Program Files (x86)\Conduit\CT3281675\plugins folder moved successfully.
C:\Program Files (x86)\Conduit\CT3281675 folder moved successfully.
C:\Program Files (x86)\Conduit\Community Alerts folder moved successfully.
C:\Program Files (x86)\Conduit folder moved successfully.
C:\Users\Alistair\AppData\Roaming\Searchya folder moved successfully.
========== FILES ==========
File\Folder C:\Users\Alistair\AppData\Local\Conduit not found.
File\Folder C:\Program Files (x86)\Conduit not found.
File\Folder C:\Users\Alistair\AppData\Roaming\Searchya not found.
========== COMMANDS ==========
[EMPTYTEMP]
User: Alistair
->Temp folder emptied: 358941789 bytes
->Temporary Internet Files folder emptied: 85969691 bytes
->Google Chrome cache emptied: 11318788 bytes
->Flash cache emptied: 506 bytes
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 4514168 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 187372 bytes
RecycleBin emptied: 10410 bytes
Total Files Cleaned = 440.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 03182013_231751
Files\Folders moved on Reboot...
C:\Users\Alistair\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
Copy referred to:
All processes killed
========== OTL ==========
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\\DefaultScope| /E : value set successfully!
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{5BD8EF88-D60D-AD5B-07E3-2AB749C6BBAD}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{5BD8EF88-D60D-AD5B-07E3-2AB749C6BBAD}\ not found.
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\\Start Page| /E : value set successfully!
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\\DefaultScope| /E : value set successfully!
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{0633EE93-D776-472f-A0FF-E1416B8B2E3A}\ not found.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\SearchScopes\{3AF48E71-8792-2E43-F4A1-4F2C909F16E2}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{3AF48E71-8792-2E43-F4A1-4F2C909F16E2}\ not found.
64bit-Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
C:\Program Files (x86)\LastPass\LPToolbar_x64.dll moved successfully.
Registry key HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{95D9ECF5-2A4D-4550-BE49-70D42F71296E}\ deleted successfully.
C:\Program Files (x86)\LastPass\LPToolbar.dll moved successfully.
64bit-Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} deleted successfully.
64bit-Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5}\ deleted successfully.
File C:\Program Files (x86)\LastPass\LPToolbar_x64.dll not found.
Registry value HKEY_LOCAL_MACHINE\Software\Microsoft\Internet Explorer\Toolbar\\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{9f6b5cc3-5c7b-4b5c-97af-19dec1e380e5}\ deleted successfully.
File C:\Program Files (x86)\LastPass\LPToolbar.dll not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{724D43A0-0D85-11D4-9908-00400523E39A} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{724D43A0-0D85-11D4-9908-00400523E39A}\ not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Toolbar\WebBrowser\\{EEE6C35B-6118-11DC-9C72-001320C79847} deleted successfully.
Registry key HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{EEE6C35B-6118-11DC-9C72-001320C79847}\ not found.
Registry value HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\\ConduitFloatingPlugin_kdfbddbdpnahdahmamlolacimfdbeckk deleted successfully.
C:\Program Files (x86)\Conduit\CT3281675\plugins\ConduitFloatingPlugin.dll moved successfully.
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\\NoActiveDesktopChanges deleted successfully.
Registry value HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer\\NoActiveDesktop deleted successfully.
C:\Users\Alistair\AppData\Local\Conduit folder moved successfully.
C:\Program Files (x86)\Conduit\CT3281675\plugins folder moved successfully.
C:\Program Files (x86)\Conduit\CT3281675 folder moved successfully.
C:\Program Files (x86)\Conduit\Community Alerts folder moved successfully.
C:\Program Files (x86)\Conduit folder moved successfully.
C:\Users\Alistair\AppData\Roaming\Searchya folder moved successfully.
========== FILES ==========
File\Folder C:\Users\Alistair\AppData\Local\Conduit not found.
File\Folder C:\Program Files (x86)\Conduit not found.
File\Folder C:\Users\Alistair\AppData\Roaming\Searchya not found.
========== COMMANDS ==========
[EMPTYTEMP]
User: Alistair
->Temp folder emptied: 358941789 bytes
->Temporary Internet Files folder emptied: 85969691 bytes
->Google Chrome cache emptied: 11318788 bytes
->Flash cache emptied: 506 bytes
User: All Users
User: Default
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Default User
->Temp folder emptied: 0 bytes
->Temporary Internet Files folder emptied: 0 bytes
User: Public
%systemdrive% .tmp files removed: 0 bytes
%systemroot% .tmp files removed: 0 bytes
%systemroot%\System32 .tmp files removed: 0 bytes
%systemroot%\System32 (64bit) .tmp files removed: 0 bytes
%systemroot%\System32\drivers .tmp files removed: 0 bytes
Windows Temp folder emptied: 4514168 bytes
%systemroot%\sysnative\config\systemprofile\AppData\Local\Microsoft\Windows\Temporary Internet Files folder emptied: 187372 bytes
RecycleBin emptied: 10410 bytes
Total Files Cleaned = 440.00 mb
OTL by OldTimer - Version 3.2.69.0 log created on 03182013_231751
Files\Folders moved on Reboot...
C:\Users\Alistair\AppData\Local\Microsoft\Windows\Temporary Internet Files\counters.dat moved successfully.
PendingFileRenameOperations files...
Registry entries deleted on Reboot...
- Oct 5, 2012
- 2,697
STEP 1: Run a scan with Junkware Removal Tool
Please download Junkware Removal Tool to your desktop from here
STEP 2: Run a scan with AdwCleaner
<ol><li>Download AdwCleaner from the below link.
<><a href="http://general-changelog-team.fr/fr/downloads/finish/20-outils-de-xplode/2-adwcleaner" target="_blank">ADWCLEANER DOWNLAOD LINK</a></> (This link will automatically download Security Check on your computer)</li>
<li>Close all open programs and internet browsers.</li>
<li>Double click on <>adwcleaner.exe</> to run the tool.</li>
<li>Click on <>Delete</>,then confirm each time with <>Ok</>.</li>
<li>Your computer will be rebooted automatically. A text file will open after the restart.</li>
<li>Please post the contents of that logfile with your next reply.</li>
<li>You can find the logfile at <>C:\AdwCleaner[S1].txt</> as well.</li>
</ol>
<hr/>
Please download Junkware Removal Tool to your desktop from here
- Turn off your antivirus software now to avoid potential conflicts
- Double-click to run the tool. For Windows Vista or 7 users, right-click the file and select Run as Administrator
- The tool will open and start scanning your system
- Please be patient as this can take a while to complete depending on your system's specifications
- On completion, a log (JRT.txt) will be saved to your desktop and will automatically open
- Post the contents of JRT.txt into your next reply
STEP 2: Run a scan with AdwCleaner
<ol><li>Download AdwCleaner from the below link.
<><a href="http://general-changelog-team.fr/fr/downloads/finish/20-outils-de-xplode/2-adwcleaner" target="_blank">ADWCLEANER DOWNLAOD LINK</a></> (This link will automatically download Security Check on your computer)</li>
<li>Close all open programs and internet browsers.</li>
<li>Double click on <>adwcleaner.exe</> to run the tool.</li>
<li>Click on <>Delete</>,then confirm each time with <>Ok</>.</li>
<li>Your computer will be rebooted automatically. A text file will open after the restart.</li>
<li>Please post the contents of that logfile with your next reply.</li>
<li>You can find the logfile at <>C:\AdwCleaner[S1].txt</> as well.</li>
</ol>
<hr/>
Last edited by a moderator:
Thanks, Kuttus,
So far, so good. I ran the two programs as instructed and the 'Search' tab has disappeared from Chrome. Log files requested:
[attachment=3956]
[attachment=3957]
Is that it? I noticed a few 'deletion failed' Registry items. Do I need to do anything about those?
So far, so good. I ran the two programs as instructed and the 'Search' tab has disappeared from Chrome. Log files requested:
[attachment=3956]
[attachment=3957]
Is that it? I noticed a few 'deletion failed' Registry items. Do I need to do anything about those?
Attachments
- Oct 5, 2012
- 2,697
It seems it deleted most of the infected files..... Are you facing any other issues on the computer now?
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
STEP 1: Run a scan with ESET Online Scanner
<ol>
<li>Download ESET Online Scanner utility from the below link
<><a title="External link" href="http://download.eset.com/special/eos/esetsmartinstaller_enu.exe" rel="nofollow">ESET ONLINE SCANNER DOWNLOAD LINK</a></> <em>(This link will automatically download ESET Online Scanner on your computer.)</em></li>
<li>Double click on the Eset installer program (esetsmartinstaller_enu.exe).</li>
<li>Check <>Yes, I accept the Terms of Use</></li>
<li>Click the <>Start</> button.</li>
<li>Check <>Scan archives</></li>
<li>Push the <>Start</> button.</li>
<li>ESET will then download updates for itself, install itself, and begin scanning your computer. Please be patient as this can take some time.</li>
<li>When the scan completes, push <>List of found threats</></li>
<li>Push <>Export to Text file </> and save the file to your desktop using a unique name, such as <>ESET Scan</>. Include the contents of this report in your next reply.Note - when ESET doesn't find any threats, no report will be created.</li>
<li>Push the <>back</> button.</li>
<li>Push <>Finish</></li>
</ol>
<hr />
Last edited by a moderator:
- Oct 5, 2012
- 2,697
Great to hear that it worked.......  Just run the following tools also so that we can make sure we are 100% safe.
Just run the following tools also so that we can make sure we are 100% safe.
STEP 1: Run a scan with Kaspersky Virus Removal Tool
<ol><li>Download Kaspersky Virus Removal Tool from the below link and then double click on it to start this utility.
<><a title="External link" href="http://www.kaspersky.com/antivirus-removal-tool?form=1" rel="nofollow">KASPERSKY VIRUS REMOVAL TOOL</a></> <em>(This link open an new webpage from where you can download Kaspersky Virus Removal Tool on your computer.)</em></li>
<li>Follow the onscreen prompts until it is installed</li>
<li>Click the Options button (the 'Gear' icon), then make sure only the following are ticked:
<ul>
<li><span style="color: #ff0000;">System Memory</span></li>
<li><span style="color: #ff0000;">Hidden startup objects</span></li>
<li><span style="color: #ff0000;">Disk boot sectors</span></li>
<li><span style="color: #ff0000;">Local Disk (C: )</span></li>
<li><span style="color: #ff0000;">Also any other drives (Removable that you may have)</span></li>
</ul>
</li>
<li>Then click on <>Actions</> on the left hand side</li>
<li>Click <>Select Action</>, then make sure both <>Disinfect</> and <>Delete if disinfection fails</> are ticked</li>
<li>Click on <>Automatic Scan</></li>
<li>Now click the <>Start Scanning</> button, to run the scan</li>
<li>After the scan is complete, click the reports button ('Paper icon', next to the 'Gear' icon) on the right hand side</li>
<li>Click <>Detected threats</> on the left</li>
<li>Now click the <>Save</> button, and save it as <>kaslog.txt</> to your <>Desktop</></li>
<li>Please attach kaslog.txt in your next reply.</li>
</ol>
<hr />
You should be able to run both scans while in Normal mode...
STEP 2: Run a scan with Malwarebytes Anti-Malware in Chamelon mode
<ol>
<li>Download <>Malwarebytes Chameleon from <a title="External link" href="http://downloads.malwarebytes.org/file/chameleon" rel="nofollow external">here</a> </>and extract it to a folder in a convenient location</li>
<li>Make certain that your PC is connected to the internet and then open the folder where you extracted Chameleon to and double-click on the Chameleon help file and then follow the onscreen instructions to use it.</li>
<li>If the Chameleon help file itself will not open, then double-click each file one by one until you find one that works, which will be indicated by a black DOS/command prompt window <em><>Note:</> Do not attempt to open <>mbam-killer</> as that is not a Chameleon executable and serves a different purpose)</em></li>
<li>Follow the onscreen instructions to press a key to continue and Chameleon will proceed to download and install Malwarebytes Anti-Malware for yo</li>
<li>Once it has done this, it will attempt to update Malwarebytes Anti-Malware, click <>OK</> when it says that the database was updated successful</li>
<li>Next, Malwarebytes Anti-Malware will automatically open and perform a Quick scan</li>
<li>Upon completion of the scan, if anything has been detected, click on <>Show Result</></li>
<li>Have Malwarebytes Anti-Malware remove any threats that are detected and click <>Yes</> if prompted to reboot your computer to allow the removal process to complete</li>
<li>After your computer restarts, open <>Malwarebytes Anti-Malware</> and perform a Full System scan to verify that there are no remaining threats</li>
Please add both logs in your next reply.
</ol>
<hr />
STEP 3: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
STEP 1: Run a scan with Kaspersky Virus Removal Tool
<ol><li>Download Kaspersky Virus Removal Tool from the below link and then double click on it to start this utility.
<><a title="External link" href="http://www.kaspersky.com/antivirus-removal-tool?form=1" rel="nofollow">KASPERSKY VIRUS REMOVAL TOOL</a></> <em>(This link open an new webpage from where you can download Kaspersky Virus Removal Tool on your computer.)</em></li>
<li>Follow the onscreen prompts until it is installed</li>
<li>Click the Options button (the 'Gear' icon), then make sure only the following are ticked:
<ul>
<li><span style="color: #ff0000;">System Memory</span></li>
<li><span style="color: #ff0000;">Hidden startup objects</span></li>
<li><span style="color: #ff0000;">Disk boot sectors</span></li>
<li><span style="color: #ff0000;">Local Disk (C: )</span></li>
<li><span style="color: #ff0000;">Also any other drives (Removable that you may have)</span></li>
</ul>
</li>
<li>Then click on <>Actions</> on the left hand side</li>
<li>Click <>Select Action</>, then make sure both <>Disinfect</> and <>Delete if disinfection fails</> are ticked</li>
<li>Click on <>Automatic Scan</></li>
<li>Now click the <>Start Scanning</> button, to run the scan</li>
<li>After the scan is complete, click the reports button ('Paper icon', next to the 'Gear' icon) on the right hand side</li>
<li>Click <>Detected threats</> on the left</li>
<li>Now click the <>Save</> button, and save it as <>kaslog.txt</> to your <>Desktop</></li>
<li>Please attach kaslog.txt in your next reply.</li>
</ol>
<hr />
You should be able to run both scans while in Normal mode...
STEP 2: Run a scan with Malwarebytes Anti-Malware in Chamelon mode
<ol>
<li>Download <>Malwarebytes Chameleon from <a title="External link" href="http://downloads.malwarebytes.org/file/chameleon" rel="nofollow external">here</a> </>and extract it to a folder in a convenient location</li>
<li>Make certain that your PC is connected to the internet and then open the folder where you extracted Chameleon to and double-click on the Chameleon help file and then follow the onscreen instructions to use it.</li>
<li>If the Chameleon help file itself will not open, then double-click each file one by one until you find one that works, which will be indicated by a black DOS/command prompt window <em><>Note:</> Do not attempt to open <>mbam-killer</> as that is not a Chameleon executable and serves a different purpose)</em></li>
<li>Follow the onscreen instructions to press a key to continue and Chameleon will proceed to download and install Malwarebytes Anti-Malware for yo</li>
<li>Once it has done this, it will attempt to update Malwarebytes Anti-Malware, click <>OK</> when it says that the database was updated successful</li>
<li>Next, Malwarebytes Anti-Malware will automatically open and perform a Quick scan</li>
<li>Upon completion of the scan, if anything has been detected, click on <>Show Result</></li>
<li>Have Malwarebytes Anti-Malware remove any threats that are detected and click <>Yes</> if prompted to reboot your computer to allow the removal process to complete</li>
<li>After your computer restarts, open <>Malwarebytes Anti-Malware</> and perform a Full System scan to verify that there are no remaining threats</li>
Please add both logs in your next reply.
</ol>
<hr />
STEP 3: Run a HitmanPro scan
<ol>
<li><>Download the latest official version of HitmanPro</>.
<a href="http://www.surfright.nl/en/hitmanpro/" rel="nofollow" target="_blank"> <>HITMANPRO DOWNLOAD LINK</></a> <em>(This link will open a download page in a new window from where you can download HitmanPro)</em></li>
<li>Start HitmanPro by <>double clicking on the previously downloaded file.</> and then following the prompts.
<img src="http://malwaretips.com/images/removalguide/hpro4.png" alt="[Image: hitmanproscan4.png]" border="0" /></li>
<li>Once the scan is complete, a screen displaying all the malicious files that the program found will be shown as seen in the image below.After reviewing each malicious object click <>Next</> .
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/02/rsz_hpro5.png" alt="[Image: hitmanproscan5.png]" border="0" /></li>
<li>Click <>Activate free license</> to start the free 30 days trial and remove the malicious files.
<img src="http://malwaretips.com/images/removalguide/hpro6.png" alt="[Image: hitmanproscan6.png]" border="0" /></li>
<li>HitmanPro will now start removing the infected objects, and in some instances, may suggest a reboot in order to completely remove the malware from your system. In this scenario, always confirm the reboot action to be on the safe side.
</ol>
Add to your next reply, any log that HitmanPro might generate.
<hr />
Last edited by a moderator:
1. Kaspersky Virus Removal Tool won't install. Error message = [attachment=3988]
2. MwB Chameleon. Database updated OK. Quick Scan result = "No malicious items detected". No log. Restarted machine and ran full scan with updated database. No malicious items were detected BUT the "Search" tab reappeared. Screen dump of Chrome with the offending tab won't attach. File, 4.0 MB, too big.
3. Ran HitmanPro which found no threats, but reported 15 tracking cookies.
HitmanPro log file:
What now, Kuttus?
2. MwB Chameleon. Database updated OK. Quick Scan result = "No malicious items detected". No log. Restarted machine and ran full scan with updated database. No malicious items were detected BUT the "Search" tab reappeared. Screen dump of Chrome with the offending tab won't attach. File, 4.0 MB, too big.
3. Ran HitmanPro which found no threats, but reported 15 tracking cookies.
HitmanPro log file:
Code:
HitmanPro 3.7.2.190
www.hitmanpro.com
Computer name . . . . : TOSHIBA
Windows . . . . . . . : 6.2.0.9200.X64/2
User name . . . . . . : Toshiba\Alistair
UAC . . . . . . . . . : Enabled
License . . . . . . . : Free
Scan date . . . . . . : 2013-03-20 19:17:03
Scan mode . . . . . . : Normal
Scan duration . . . . : 1m 59s
Disk access mode . . : Direct disk access (SRB)
Cloud . . . . . . . . : Internet
Reboot . . . . . . . : No
Threats . . . . . . . : 0
Traces . . . . . . . : 15
Objects scanned . . . : 1,155,737
Files scanned . . . . : 11,790
Remnants scanned . . : 312,707 files / 831,240 keys
Cookies _____________________________________________________________________
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:ad.yieldmanager.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:adinterax.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:apmebf.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:atdmt.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:c.atdmt.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:doubleclick.net
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:invitemedia.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:kaspersky.122.2o7.net
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:media6degrees.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:mediaplex.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:serving-sys.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:stats.paypal.com
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:track.adform.net
C:\Users\Alistair\AppData\Local\Google\Chrome\User Data\Default\Cookies:www.googleadservices.com
C:\Users\Alistair\AppData\Roaming\Microsoft\Windows\Cookies\KQKLL5QH.txtWhat now, Kuttus?
kuttus said:You mean that Search' tab is still on Google Chrome?
Regrettably yes. It was removed after running JTL and AdwCleaner, but reappeared tonight after the MalwareBytes Chameleon run. I will not try anything until I hear from you.
PS I did a search for Conduit in the Registry and found two instances of 'ConduitFloatingPlugin' under 'StartupApproved>Run'. Left them alone!
- Oct 5, 2012
- 2,697
STEP 1: Run a scan with OTL by OldTimer
<ol><li>Download the OTL utility using the below link :
<><a title="External link" href="http://oldtimer.geekstogo.com/OTL.exe" rel="nofollow external">OTL DOWNLOAD LINK</a> <em>(This link will automatically download OTL on your computer)</em></></li>
<li>Double click on the icon to run it. Make sure all other windows are closed and to let it run uninterrupted.
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/07/OTL-logo.png" alt="" title="OTL-logo" width="106" height="118" class="alignnone size-full wp-image-3946" /></li>
<li>When the window appears, <>underneath Output</> at the top change it to <>Minimal Output</>.</li>
<li>Check the boxes beside <>LOP Check</> and <>Purity Check</>.</li>
<li>Click the<> Run Scan</> button.
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/07/OTL.png" alt="" title="OTL" width="658" height="584" class="alignnone size-full wp-image-3945" /></li>
<li>When the scan completes, it will open two notepad windows. <>OTL.Txt</> and <>Extras.Txt</>. These are saved in the same location as OTL.
<>Please post this 2 logs in your first reply.</>.</li></ol>
Settings You need to Select in OTL
<hr />
<ol><li>Download the OTL utility using the below link :
<><a title="External link" href="http://oldtimer.geekstogo.com/OTL.exe" rel="nofollow external">OTL DOWNLOAD LINK</a> <em>(This link will automatically download OTL on your computer)</em></></li>
<li>Double click on the icon to run it. Make sure all other windows are closed and to let it run uninterrupted.
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/07/OTL-logo.png" alt="" title="OTL-logo" width="106" height="118" class="alignnone size-full wp-image-3946" /></li>
<li>When the window appears, <>underneath Output</> at the top change it to <>Minimal Output</>.</li>
<li>Check the boxes beside <>LOP Check</> and <>Purity Check</>.</li>
<li>Click the<> Run Scan</> button.
<img src="http://malwaretips.com/blogs/wp-content/uploads/2012/07/OTL.png" alt="" title="OTL" width="658" height="584" class="alignnone size-full wp-image-3945" /></li>
<li>When the scan completes, it will open two notepad windows. <>OTL.Txt</> and <>Extras.Txt</>. These are saved in the same location as OTL.
<>Please post this 2 logs in your first reply.</>.</li></ol>
Settings You need to Select in OTL
- Click the Scan All Users checkbox.
- Change Standard Registry to All.
- Check the boxes beside LOP Check and Purity Check.
<hr />
Last edited by a moderator:
Ran OTL and here is log: [attachment=3991].
No Extras.txt this time. My OTL settings were as per your instructions. Should Extra Registry be checked?
I did a 'Find' for Conduit in the Registry and found two instances of 'ConduitFloatingPlug-in' in branches labeled 'StartUpApproved>Run', which seems significant.
PS Just had a thought and checked Chrome Settings. Found that the Conduit Search page is listed as a startup page. Deleted it and re-booted... didn't reappear. Did another search of the Registry for 'ConduitFloatingPlug-in'. Nothing found. Presumably there is a bit of malware lurking somewhere that will restore the Search page in due course.
No Extras.txt this time. My OTL settings were as per your instructions. Should Extra Registry be checked?
I did a 'Find' for Conduit in the Registry and found two instances of 'ConduitFloatingPlug-in' in branches labeled 'StartUpApproved>Run', which seems significant.
PS Just had a thought and checked Chrome Settings. Found that the Conduit Search page is listed as a startup page. Deleted it and re-booted... didn't reappear. Did another search of the Registry for 'ConduitFloatingPlug-in'. Nothing found. Presumably there is a bit of malware lurking somewhere that will restore the Search page in due course.
Attachments
- Oct 5, 2012
- 2,697
Could you please send me a Screenshots of the Search tab you can see, (the one reappear today)
To Take Screen Of Your Screen.
To Take Screen Of Your Screen.
- Press PRINT SCREEN (Print Scr) key on Your Keyboard.
- Now Open MS Paint
- Open Paint by clicking the Start button
, clicking All Programs, clicking Accessories, and then clicking Paint.

- In MS Paint Click Edit, and then click Paste.
- After this Save the File on your computer by Clicking on File --> Save
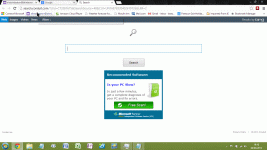
Here is the screen shot you asked for: [attachment=3992]
Could this problem originate in one of my other computers and infect the laptop through Google Sync?
PS Talk of the devil!!!! The Conduit Search tab has just appeared in Chrome and Firefox on my desktop PC.
Could this problem originate in one of my other computers and infect the laptop through Google Sync?
PS Talk of the devil!!!! The Conduit Search tab has just appeared in Chrome and Firefox on my desktop PC.
Attachments
- Oct 5, 2012
- 2,697
I think there is something like that is happening.
Okay. Please run the Junkware Removal Tool and Adware Cleaner once again in both the computer........
Follow these steps to adjust your homepage settings:
Okay. Please run the Junkware Removal Tool and Adware Cleaner once again in both the computer........
Follow these steps to adjust your homepage settings:
- Click the Chrome menu
Chrome menu on the browser toolbar.
- Select Settings. or Copy and Paste the following code in the address bar of Google Chrome and Hit on enter.
Code:chrome://settings/ - Click on Set Page on Start up.

- Now you can see 3 Home page Set over there. Delete the 3rd one...
- Status
- Not open for further replies.
Similar threads
- Locked
- Replies
- 5
- Views
- 467
- Replies
- 7
- Views
- 581