If your computer is locked, and you are seeing a “You have lost control over your computer” notification from MBL Advisory (Malware Block List) and Decrypt Protect, then your computer is infected with a piece of malware known as Trojan Reveton.
The Decrypt Protect virus is distributed through several means. Malicious websites, or legitimate websites that have been compromised, may drop this trojan onto a compromised computer. This drive-by-download often happens surreptitiously. Another method used to propagate this type of malware is spam email containing infected attachments or links to malicious websites. The threat may also be downloaded manually by tricking the user into thinking they are installing a useful piece of software.
The Decrypt Protect virus is also prevalent on peer-to-peer file sharing websites and is often packaged with pirated or illegally acquired software.
Once installed on your computer, the Decrypt Protect MoneyPak virus will display a bogus notification that pretends to be from the MBL Advisory, and states that your computer has been blocked due to it being involved with the distribution of pornographic material, SPAM and copyrighted content.
The Decrypt Protect virus will lock you out of your computer and applications, so whenever you’ll try to log on into your Windows operating system or Safe Mode with Networking, it will display instead a lock screen asking you to pay a non-existing fine of 300$ in the form of a Ukash, Paysafecard or MoneyPak code.
Furthermore, to make this alert seem more authentic, this virus also has the ability to access your installed webcam, so that the bogus Decrypt Protect notification shows what is happening in the room. The the Decrypt Protect MoneyPak virus virus will also display a countdown timer, a bogus case number and FBI agent name, needless to say that all this details are fake and are only used, in an attempt to scare you into sending a MoneyPak code.
The Decrypt Protect virus locks the computer and, depending on the user’s current location, displays a localized web page that covers the entire desktop of the infected computer and demands payment for the supposed possession of illicit material.
![Decrypt Protect virus [Image: Decrypt Protect virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/05/decrypt-protect-virus.jpg)
Cyber criminals often updated the design of this lock screen, however you should always keep in mind that the MBL Advisory will never lock down your computer or monitor your online activities.
The message displayed by the threat can be localized depending on the user’s location, with text written in the appropriate language.
DECRYPT PROTECT
MBL Advisory
You have 48 hours left to enter your payment.
You have lost control over your computer. Your system and all your files has been blocked and encrypted because you were spreading the Malware (viruses, trojans, worms). You are breaking numerous International and USA laws.
Actions made by your computer backed up under United States law USA Patriot ACT What exactly is THE Patriot Act? The Patriot Act is short for the Uniting and Strengthening America by Providing Appropriate Tools Required to Intercept and obstruct Terrorism Act of 2001. We have the right backed by law: Sec.201. Authority to intercept wire, oral, and electronic communications relating to terrorism. Sec.202. Authority to intercept wire, oral, and electronic communications relating to computer fraud and abuse offences. Sec.209. Seizure of voice-mail messages pursuant to warrants. Sec.2017. Interception of computer trespasser communications. With the support of the federal Bureau investigation department on cybercrime and the Supreme court of the United States of America. We have the legal right to scan and intercept any information going in and out of your computers. Your IP address was identified and isolated by our organisation in connection with a complaint to the involvement of distributed denial of service (DDoS) attack such organisations: NASDAQ and BATSS stock exchange markets and WIKILEAKS.ORG website. Such attacks caused $15 billion in damage. In order to isolate the infected files we have blocked your access to the outside world and your IP address was listed in our MBL (Malware Block List). You can not use the Internet or any of your programs. You have a chance to settle this issue right now before we contact the proper authorities. Within 48 hours you can pay a fine of $300. All your files will be decrypted, and access to the computer will be granted, a claim for compensation from affected companies will be removed and your IP address will be restored to good standings with MBL (Malware Block List). If your don’t pay a penalty within next 48 hours, local authorities and service will be contacted, and most likely it will result in your arrest. You can and will be prosecuted to the fullest extent of the law in order to recover our losses. Do not take any chance to be convicted as a felon. Our Decrypt Protect agent has conducted a full check of your system and found following violations: Your are a distributor of pornographic and porno materials, regular watch porno sites with child pornography and zoophillia. You possess unlicensed software and private audio and video records…
This infection will also scan your computer for files that end with the .ddrw ,.pptm ,.dotm ,.xltx ,.text ,.docm ,.djvu ,.potx ,.jpeg ,.pptx ,.sldm ,.xlsm ,.sldx ,.xlsb ,.ppam ,.xlsx ,.ppsm ,.ppsx ,.docx ,.odp ,.eml ,.ods ,.dot ,.php ,.xla ,.pas ,.gif ,.mpg ,.ppt ,.bkf ,.sda ,.mdf ,.ico ,.dwg ,.mbx ,.sfx ,.mdb ,.zip ,.xlt extensions and then encrypt them. When the ransomware encrypts a file it will rename it as a HTML file and then embed the encrypted file inside of it. If you then attempt to launch any of these encrypted files, you will be taken to a web page, which is currently at htxp://mdlblock.in, that prompts you to pay the ransom in the form of a MoneyPak voucher.
The Decrypt Protect lock screen is a scam, and you should ignore any alerts that this malicious software might generate.
Under no circumstance should you send any Ukash, MoneyPak or Paysafecard code to these cyber criminals, and if you have, you can should request a refund, stating that you are the victim of a computer virus and scam.
Decrypt Protect lock screen – Virus Removal Guide
STEP 1: Remove Decrypt Protect lock screen from your computer
Decrypt Protect virus has modified your Windows registry and added its malicious files to run at start-up, so whenever you’re trying to boot your computer it will launch instead its bogus notification.To remove these malicious changes, we can use any of the below methods :
Method 1: Start your computer in Safe Mode with Networking and scan for malware
Some variants of Decrypt Protect virus will allow the users to start the infected computer in Safe Mode with Networking without displaying the bogus lock screen. In this first method, we will try to start the computer in Safe Mode with Networking and then scan for malware to remove the malicious files.
- Remove all floppy disks, CDs, and DVDs from your computer, and then restart your computer.
- Press and hold the F8 key as your computer restarts.Please keep in mind that you need to press the F8 key before the Windows start-up logo appears.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - On the Advanced Boot Options screen, use the arrow keys to highlight Safe Mode with Networking , and then press ENTER.
![Remove Decrypt Protect virus (MoneyPak Scam) 2 [Image: Safe Mode with Networking]](//malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)
- If your computer has started in Safe Mode with Networking, you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the Decrypt Protect virus didn’t allow you to start the computer in Safe Mode with Networking,you’ll need to follow Method 2 to get rid of its lock screen.
Method 2: Restore Windows to a previous state using System Restore
System Restore can return your computer system files and programs to a time when everything was working fine, so we will try to use this Windows feature to get rid of Decrypt Protect lock screen.
- Restart your computer, and then press and hold F8 during the initial startup to start your computer in safe mode with a Command prompt.
Note: With some computers, if you press and hold a key as the computer is booting you will get a stuck key message. If this occurs, instead of pressing and holding the “F8 key”, tap the “F8 key” continuously until you get the Advanced Boot Options screen. - Use the arrow keys to select the Safe mode with a Command prompt option.
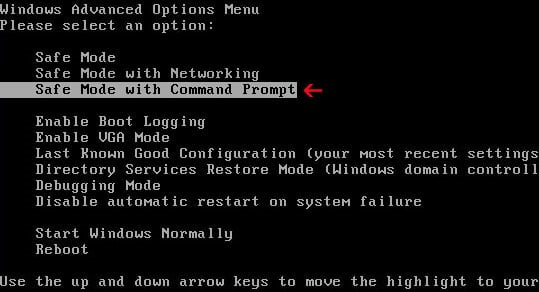
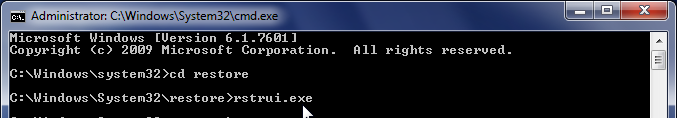
- At the command prompt, type cd restore, and then press ENTER.
Next,we will type rstrui.exe , and then press ENTER.Alternatively, if you are using Windows Vista, 7 and 8, you can just type : C:\windows\system32\rstrui.exe , and press ENTER.
If you are using Windows XP, you will need to type C:\windows\system32\restore\rstrui.exe, and then press ENTER.
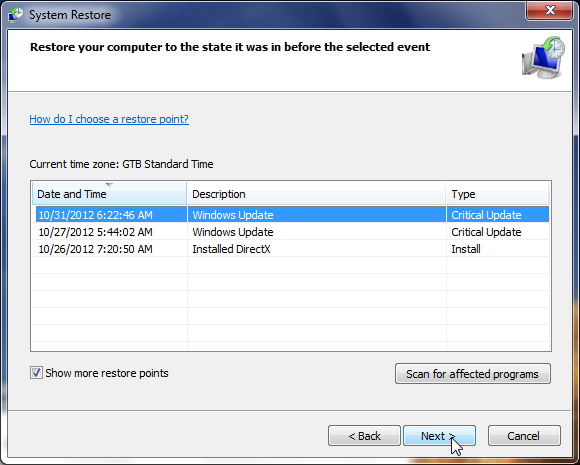
- The System Restore utility will start, and you’ll need to select a restore point previous to this infection.
- After System Restore has completed its task, you should be able to boot in Windows normal mode, and perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
IF the Decrypt Protect virus didn’t allow you to restore your computer to a previous point, you’ll need to follow Method 3 to get rid of its screen lock.
Method 3: Remove Decrypt Protect virus with HitmanPro Kickstart
IF you couldn’t boot into Safe Mode with Command Prompt or didn’t have a System Restore point on your machine, we can use HitmanPro Kickstart to bypass this infection, and access your computer to scan it for malware.
- We will need to create a HitmanPro Kickstart USB flash drive,so while you are using a “clean” (non-infected) computer, download HitmanPro from the below link.
HITMANPRO DOWNLOAD LINK (This link will open a download page in a new window from where you can download HitmanPro) - Insert your USB flash drive into your computer and follow the instructions from the below video:
- After you have create the HitmanPro Kickstart USB flash drive, you can insert this USB drive into the infected machine and start your computer.
- Once the computer starts, repeatedly tap the F11 key (on some machines its F10 or F2),which should bring up the Boot Menu, from there you can select to boot from your USB.
Next,you’ll need to perform a system scan with HitmanPro as see in the below video:
- After HitmanPro Kickstart has completed its task,you should be able to boot in Windows normal mode,from there you’ll need to perform a system scan (as seen on STEP 2) with Malwarebytes Anti-Malware and HitmanPro to remove the malicious files from your machine.
STEP 2: Remove Decrypt Protect malicious files from your computer
Run a computer scan with Malwarebytes Anti-Malware Free
- You can download Malwarebytes Anti-Malware Free from the below link,then double click on it to install this program.
MALWAREBYTES ANTI-MALWARE DOWNLOAD LINK(This link will open a download page in a new window from where you can download Malwarebytes Anti-Malware Free) - When the installation begins, keep following the prompts in order to continue with the setup process.
DO NOT make any changes to default settings and when the program has finished installing, make sure you leave both the Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware checked,then click on the Finish button.
![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
- On the Scanner tab,select Perform quick scan and then click on the Scan button to start scanning your computer.
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)
- Malwarebytes’ Anti-Malware will now start scanning your computer for Decrypt Protect virus as shown below.
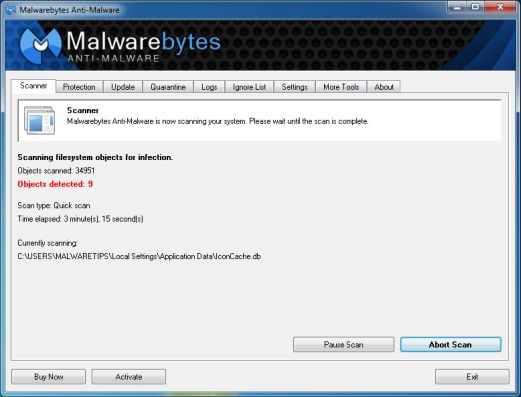
- When the Malwarebytes scan will be completed,click on Show Result.
![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
- You will now be presented with a screen showing you the malware infections that Malwarebytes’ Anti-Malware has detected.Please note that the infections found may be different than what is shown in the image.Make sure that everything is Checked (ticked) and click on the Remove Selected button.
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](//malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)
- After your computer will restart in Normal mode, open Malwarebytes Anti-Malware and perform a Full System scan to verify that there are no remaining threats
Run a computer scan with HitmanPro
- Download HitmanPro from the below link,then double click on it to start this program.
HITMANPRO DOWNLOAD LINK (This link will open a new web page from where you can download HitmanPro)
IF you are experiencing problems while trying to start HitmanPro, you can use the Force Breach mode.To start HitmanPro in Force Breach mode, hold down the left CTRL-key when you start HitmanPro and all non-essential processes are terminated, including the malware process. (How to start HitmanPro in Force Breach mode – Video) - HitmanPro will start and you’ll need to follow the prompts (by clicking on the Next button) to start a system scan with this program.
- HitmanPro will start scanning your computer for Decrypt Protect malicious files as seen in the image below.
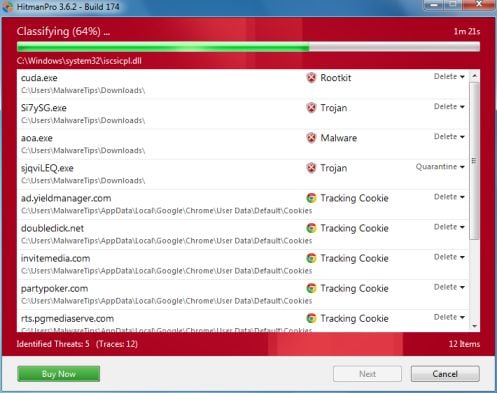
- Once the scan is complete,you’ll see a screen which will display all the infected files that this utility has detected, and you’ll need to click on Next to remove these malicious files.
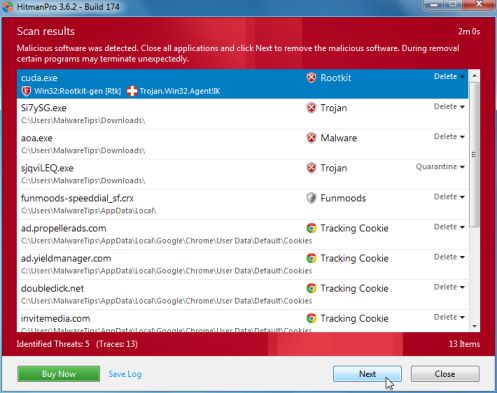
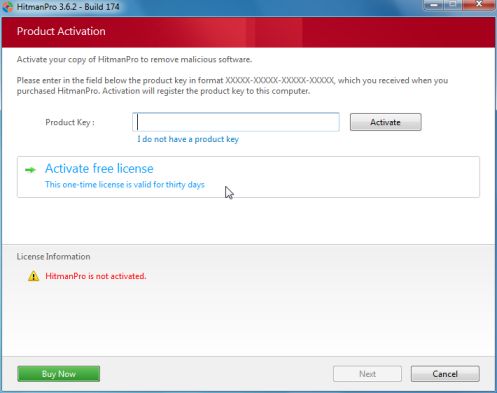
- Click Activate free license to start the free 30 days trial and remove all the malicious files from your computer.
STEP 3: Remove Decrypt Protect .html encryption from your files and folders
The Decrypt Protect virus will encrypt all your personal files, changing their default extension to a HTLM format. To restore your files from the .html to their default extension, we will use the Decrypt Protect decrypter.
This utility will automatically detect the encrypted malware files and tries to recover the file names as well.
- You can download the Decrypt Protect recovery tool from the below link.
DECRYPT PROTECT DECRYPTER DOWNLOAD LINK (This link will open a new web page from where you can download the Decrypt Protect decrypter) - Double click on decrypt_mblblock.exe, then be patience while this utility will automatically scan your hard disk and decrypt the files it found to be infected without deleting the encrypted originals. You can then check the decrypted files if they open properly. Once you verified the files were decrypted properly you can delete the encrypted HTML files.
![Restore files from .html encryption [Image: Restore file from .html encryption]](//malwaretips.com/blogs/wp-content/uploads/2013/05/restore-html-encryption.jpg)

![Remove Decrypt Protect virus (MoneyPak Scam) 1 [Image: Decrypt Protect virus]](https://malwaretips.com/blogs/wp-content/uploads/2013/05/decrypt-protect-virus.jpg)
![Remove Decrypt Protect virus (MoneyPak Scam) 2 [Image: Safe Mode with Networking]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/safemode.jpg)



![Malwarebytes Anti-Malware final installation screen [Image: Malwarebytes Anti-Malware final installation screen]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-installation.jpg)
![Run a Quick Scan with Malwarebytes Anti-Malware [Image: Malwarebytes Anti-Malware Quick Scan]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-quick-scan.jpg)

![Malwarebytes when the system scan has completed [Image: Malwarebytes Anti-Malware scan results]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-scan-results.jpg)
![Click on Remove Selected to get rid of [Image:Malwarebytes removing virus]](http://malwaretips.com/blogs/wp-content/uploads/2013/01/malwarebytes-virus-removal.jpg)





![Restore files from .html encryption [Image: Restore file from .html encryption]](http://malwaretips.com/blogs/wp-content/uploads/2013/05/restore-html-encryption.jpg)


