The Trojan.U83 pop-ups are a social engineering attack that puts your browser on full screen and displays pop-up messages that won’t go away, essentially locking your browser. These fake error messages aim to trick you into calling an indicated technical support hotline. If you call these scammers, they can offer fake solutions for your “problems” and ask for payment in the form of a one-time fee or subscription to a purported support service.
Apple does not send unsolicited email messages or make unsolicited phone calls to request personal or financial information or fix your device. Treat all unsolicited phone calls or pop-ups with skepticism. Do not provide any personal information.
Your browser may be redirected to the sites that display the “Trojan.U83” fake error messages either by malicious advertisements on the sites you visit or adware. This guide was written to help macOS users remove malware from their devices, if your just looking for a way to block the “Trojan.U83” redirect on a specific site, then you can use a free browser extension like Adblock.
When it comes to adware, these malicious programs are bundled with other free software that you download off of the Internet. Unfortunately, some free downloads do not adequately disclose that other software will also be installed and you may find that you have installed adware without your knowledge.
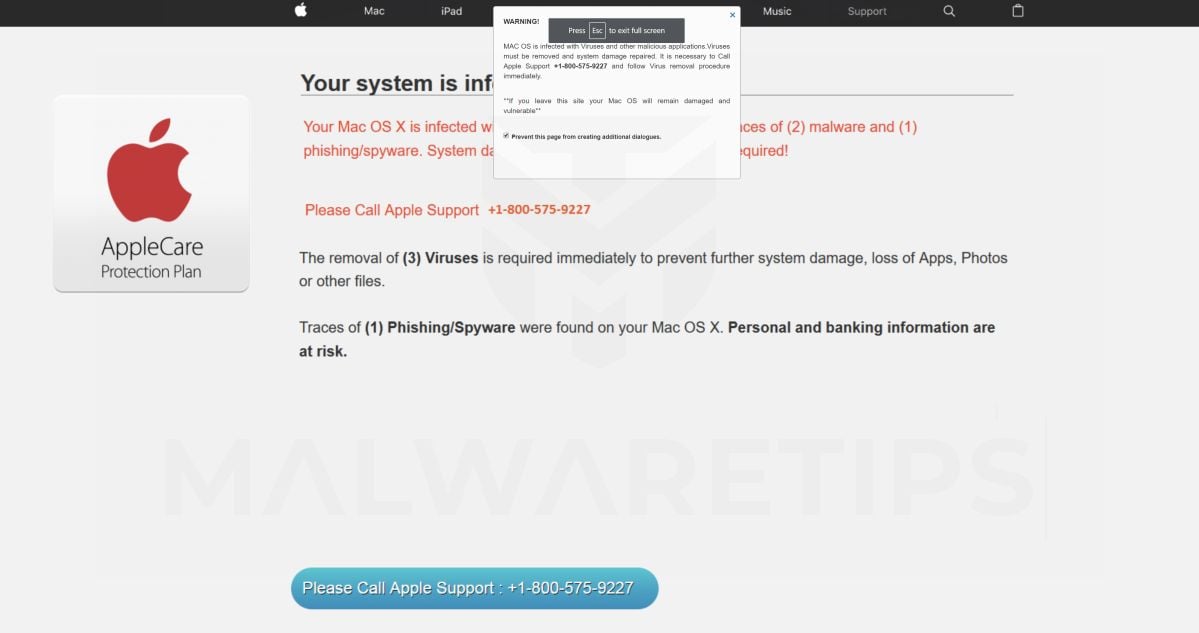
The “Trojan.U83” fake error messages are shown in such a way as to trick the user into thinking their device has crashed or that a virus has been detected. It does this to try and scare the infected user into calling one of the listed numbers in order to receive support. In reality, though, they will only be greeted with people who are trying to sell them unneeded support contracts and services.
The “Trojan.U83” fake error messages will have this message:
IMMEDIATE ACTION REQUIRED
The last website has infected your computer with a Trojan.U83.
Immediate repair is required. Click Ok to continue.
**If you leave this page your computer is exposed to being permanently damaged.**
The scammer will typically attempt to get the victim to allow remote access to their device. After remote access is gained, the scammer relies on confidence tricks typically involving utilities built into Windows and other software in order to gain the victim’s trust to pay for the supposed “support” services, when the scammer actually steals the victim’s credit card account information.
How To Remove “Trojan.U83” Pop-up Scam (Mac Guide)
Please perform all the steps in the correct order. If you have any questions or doubt at any point, STOP and ask for our assistance.
- STEP 1: Remove the malicious apps from Mac
- STEP 2: Uninstall malicious extensions from Safari, Chrome, or Firefox
- STEP 3: Use Malwarebytes for Mac to remove “Trojan.U83” adware
This step is needed if the site which is showing the “Trojan.U83” pop-up will not allow you to close your browser.
- On your keyboard, press the Command + Option + Escape keys simultaneously. This will open the “Force Quit” application window.
- In the “Force Quit”, click on Safari, Chrome, Firefox or any other browser in which you are seeing the “Trojan.U83” pop-up.
- Click the button that says “Force Quit“. This will forcefully end your browser, thus closing the “Trojan.U83” pop-up.
If you cannot switch from the unresponsive app, press Command + Option + Shift + Esc for three seconds to force it to quit. This key combination tells macOS to force quit the front-most app. Alternatively, if you are using Safari or any other browser, you can disconnect your Internet, then open the web browser, navigate from the malicious web page, then reconnect to the Internet.
STEP 1: Remove the malicious apps from Mac
In this first step, we will try to identify and remove any malicious app that might be installed on your device.
Open “Finder”
Click the Finder application on your dock.
Click on “Applications”
In the Finder left pane, click on “Applications“.
Find and remove the malicious app.
The “Applications” screen will be displayed with a list of all the apps installed on your device. Scroll through the list until you find the malicious app, right-click it, and then click “Move to Trash”.
Known malicious apps: WeKnow, MacSaver, MacVX (and variants like MacVaX), MacCaptain, MacPriceCut, SaveOnMac, Mac Global Deals or MacDeals, MacSter, MacXcoupon, Shop Brain (or variants like SShoP Braaiin), PalMall, MacShop, MacSmart, News Ticker Remover, Shopper Helper Pro, Photo Zoom, Best YouTube Downloader, ArcadeYum, Extended protection, Video download helper, FlashFree or GoldenBoy.
The malicious app may have a different name on your device. If you cannot find any malicious apps, you can proceed with the next step
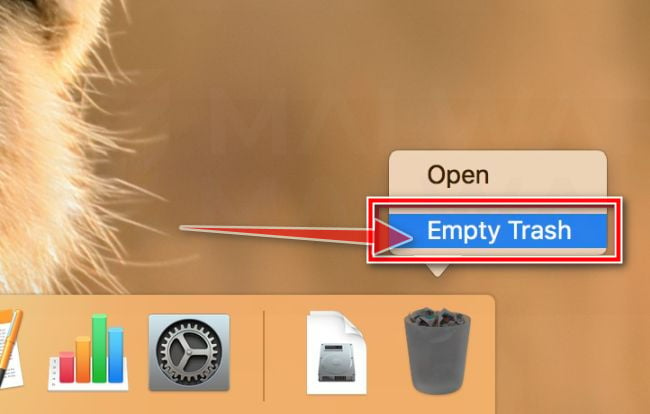
Click “Empty Trash”
On the dock, right-click on the trash icon and select “Empty Trash”. Doing so deletes the Trash’s contents, including the program that you just sent to the Trash.
Some types of malware may also create a new group policy for your device before we proceed with the other steps we need to remove these unwanted changes.
- Go to System Preferences.
- Click Profiles.
- The list will include an item “AdminPrefs“. Select this and click the remove “–” button in the lower left corner.
STEP 2: Uninstall the malicious extensions from Safari, Chrome, or Firefox
Safari
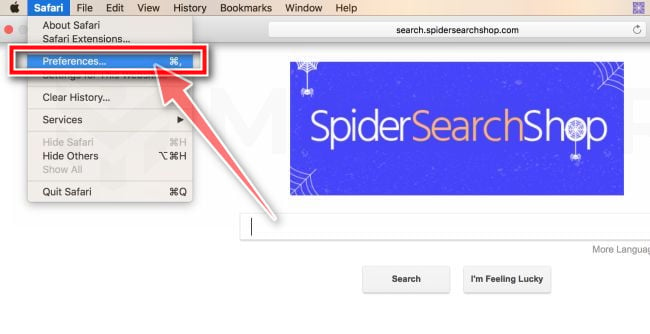
Go to Safari’s “Preferences”.
On the menu bar, click the “Safari” menu and select “Preferences”.
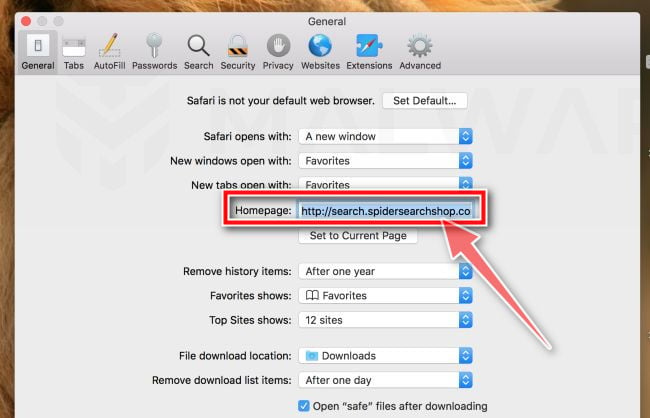
Check Homepage.
This will open a new window with your Safari preferences, opened to the “General” tab. Some browser hijackers may change your default homepage, so in the Homepage field make sure it’s a web page you want to use as your start-up page.
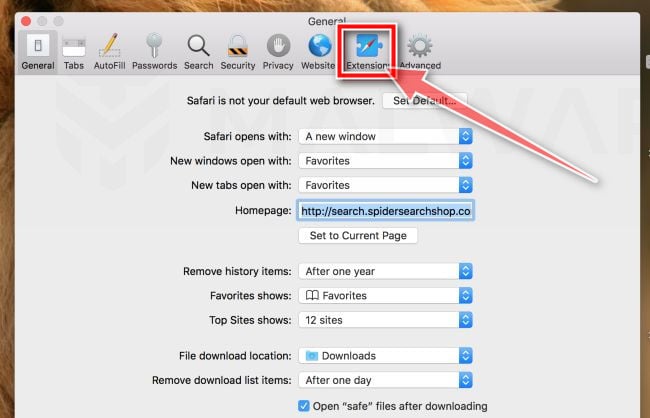
Click “Extensions”
Next, click on the “Extensions” tab.
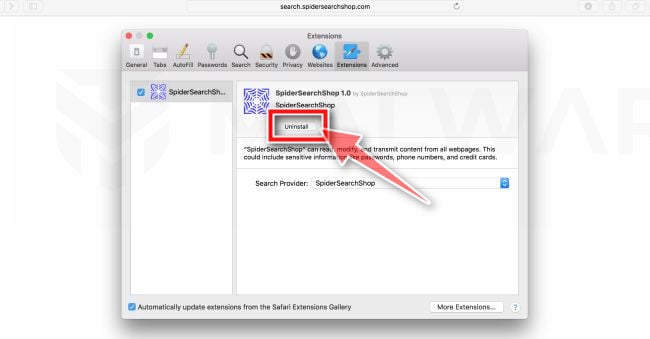
Find and uninstall the malicious extension.
The “Extensions” screen will be displayed with a list of all the extensions installed on Safari. Scroll through the list until you find the malicious extension, and then click on “Uninstall” to remove it. By default, there are no extensions installed on Safari.
Known malicious extensions: WeKnow, MacSaver, MacVX (and variants like MacVaX), MacCaptain, MacPriceCut, SaveOnMac, Mac Global Deals or MacDeals, MacSter, MacXcoupon, Shop Brain (or variants like SShoP Braaiin), PalMall, MacShop, MacSmart, News Ticker Remover, Shopper Helper Pro, Photo Zoom, Best YouTube Downloader, ArcadeYum, Extended protection, Video download helper, FlashFree or GoldenBoy.
The malicious extension may have a different name on your device. If you cannot find any malicious extension, you can proceed with the next step.
Google Chrome
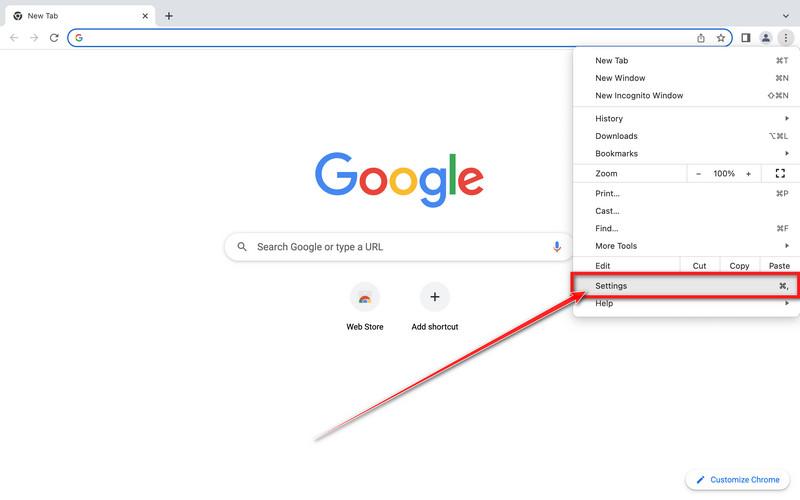
Click on the three dots at the top right and click “Settings”.
Click on Chrome’s main menu button, represented by three dots at the top right corner. Now click on the menu option labeled Settings as shown by the arrow in the picture below, which will open the basic settings screen.
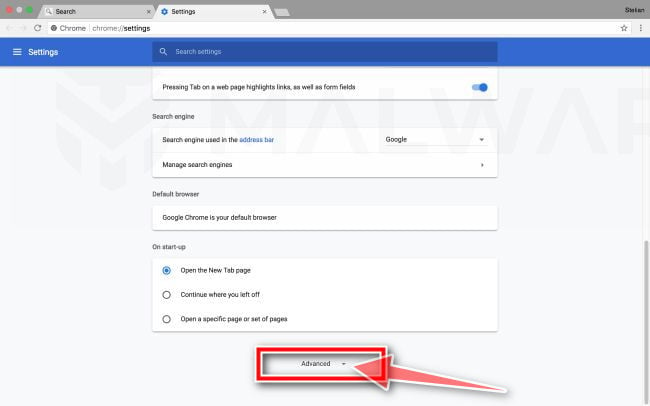
At the bottom, click “Advanced”.
Chrome’s “Settings” should now be displayed in a new tab or window, depending on your configuration. Next, scroll to the bottom of the page and click on the “Advanced” link (as seen in the below example).
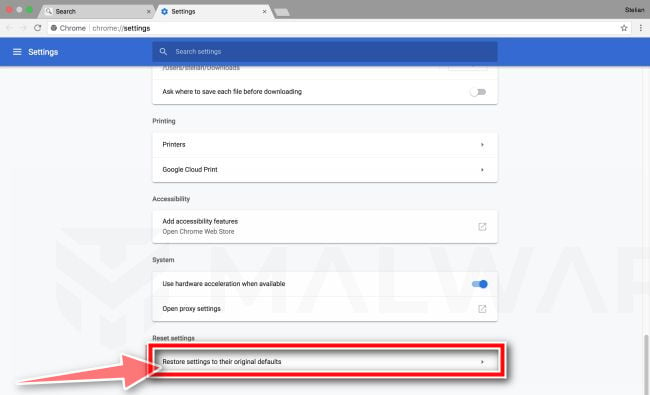
Under the section “Reset,” click “Reset”.
Chrome’s advanced settings should now be displayed. Scroll down until the “Reset and clean up” section is visible, as shown in the example below. Next, click on the “Reset settings to their original defaults” button.
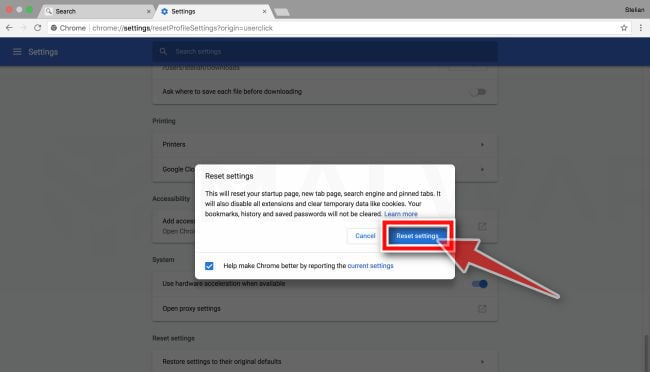
Confirm by clicking “Reset”.
A confirmation dialog should now be displayed, detailing the components that will be restored to their default state should you continue on with the reset process. To complete the restoration process, click on the “Reset Settings” button.
In many cases, changes to Chrome may not be fixed with a simple browser reset. In such a case, it will be easier to completely remove Chrome and all data, then reinstall. To do this, click the Finder icon, from the menu bar. Choose Go, and click Go to Folder, then paste one of the below paths into the window that opens.
You will need to delete all of the below items, but before doing this be aware that this will delete all data for all Google apps you have installed, such as your bookmarks, so you will need to export them before doing this.
/Applications/Chrome.app
/Library/Application Support/Google/
/Library/Google/
~/Library/Application Support/Google/
~/Library/Google/
~/Library/Preferences/com.google.Chrome.plist
After deleting all of the above files, restart your device. You can now download and re-install Google Chrome on your device. You will need to import any exported bookmarks or other data, and may need to reinstall any other Google apps that you use.
Mozilla Firefox
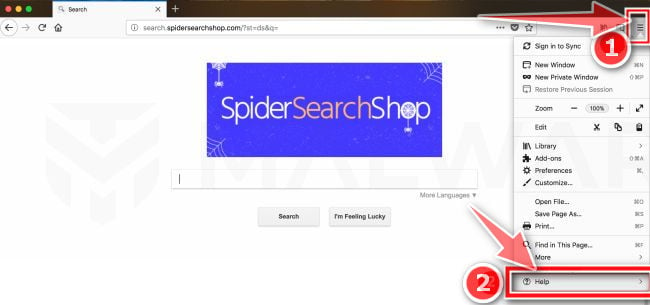
Go to the “Help” menu.
Click on Firefox’s main menu button, represented by three horizontal lines. When the drop-down menu appears, select the option labeled “Help“.
Click “Troubleshooting Information”.
From the Help menu, click on “Troubleshooting Information“.
If you’re unable to access the “Help” menu, type about:support in your address bar to bring up the Troubleshooting information page.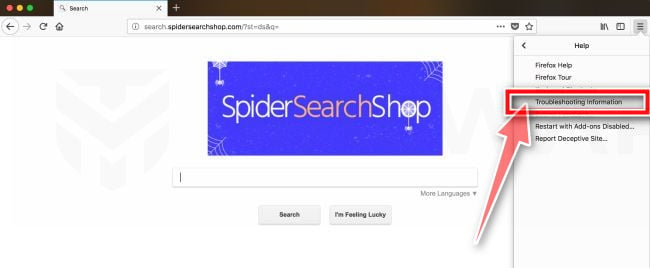
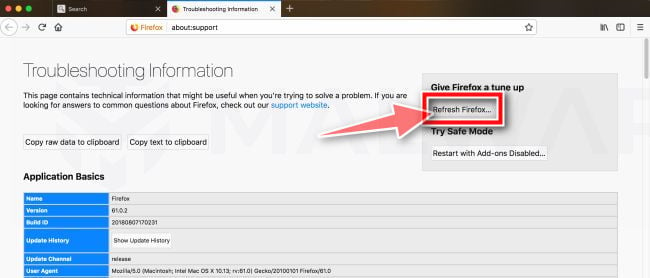
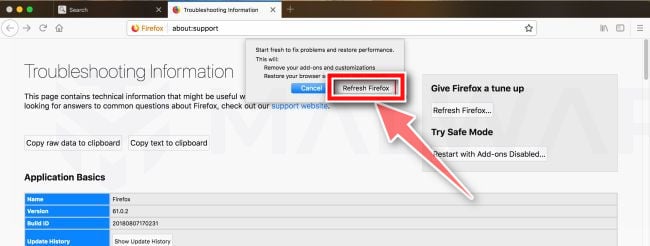
Click on “Refresh Firefox”
Click the “Refresh Firefox” button in the upper-right corner of the “Troubleshooting Information” page.
Confirm.
To continue, click on the “Refresh Firefox” button in the new confirmation window that opens.
Click on “Finish”.
Firefox will close itself and will revert to its default settings. When it’s done, a window will list the information that was imported. Click on the “Finish“.
STEP 3: Use Malwarebytes for Mac to remove “Trojan.U83” adware
Malwarebytes is one of the most popular and most used anti-malware apps, and for good reasons. It is able to destroy many types of malware that other software tends to miss, without costing you absolutely nothing. When it comes to cleaning up an infected device, Malwarebytes has always been free and we recommend it as an essential tool in the fight against malware.
The first time you install Malwarebytes, you’re given a free 30-days trial of the premium edition, which includes preventative tools like real-time scanning and specific protection from ransomware. After 30 days, it automatically reverts to the basic free version that will detect and clean up malware infections only when you run a scan.
Download Malwarebytes.
You can download Malwarebytes by clicking the link below.
 MALWAREBYTES FOR MAC DOWNLOAD LINK
MALWAREBYTES FOR MAC DOWNLOAD LINK
(The above link will open a new page from where you can download Malwarebytes for Mac)Double-click on the Malwarebytes setup file.
When Malwarebytes has finished downloading, double-click on the Malwarebytes-Mac-3.x.y.zzz.pkg file to install Malwarebytes on your device. In most cases, downloaded files are saved to the Downloads folder.
Follow the on-screen prompts to install Malwarebytes.
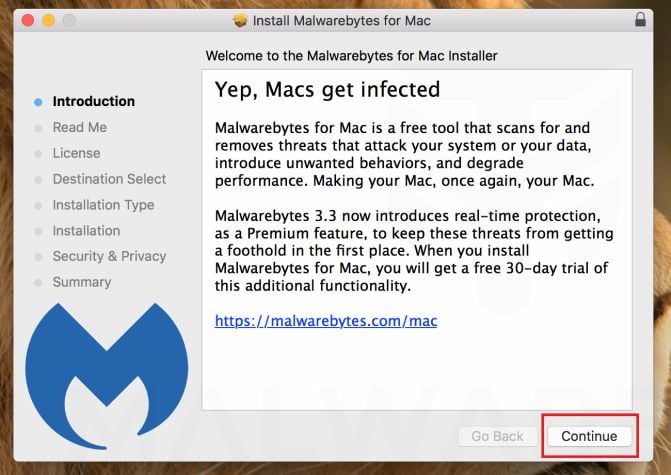
When the Malwarebytes installation begins, you will see the Malwarebytes Setup Wizard which will guide you through the installation process. The setup wizard displays an introduction to Malwarebytes for Mac. Click on “Continue” to complete the installation process.
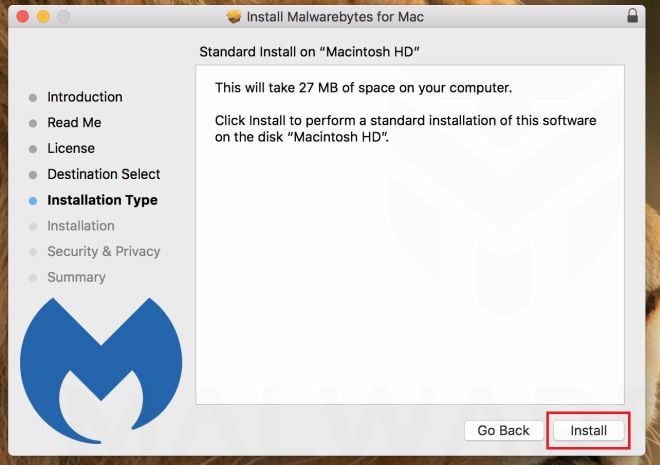
Next, click on “Install“.
Click on “Scan Now”.
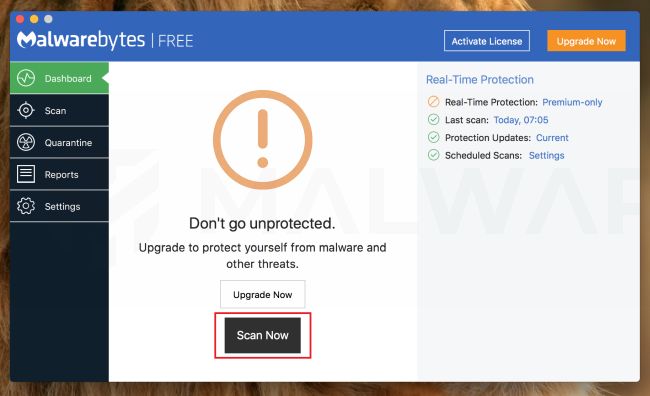
Once installed, Malwarebytes will automatically start and update the antivirus database. To perform a system scan, click on the “Scan Now” button.
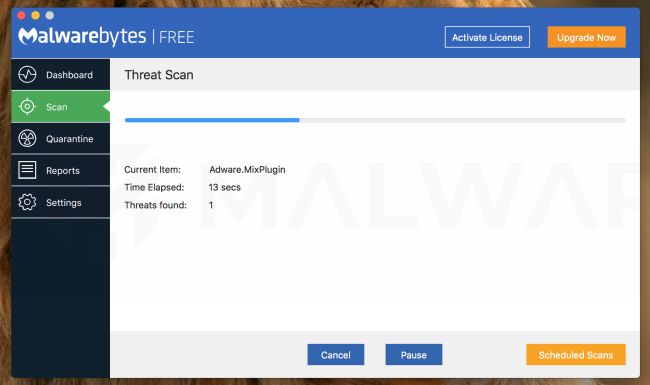
Wait for the Malwarebytes scan to complete.
Malwarebytes will now start scanning your Mac for adware and other malicious apps. This process can take a few minutes, so we suggest you do something else and periodically check on the status of the scan to see when it is finished.
Click on “Confirm”.
When the scan has completed, you will be presented with a screen showing the malware infections that Malwarebytes has detected. To remove the malicious apps that Malwarebytes has found, click on the “Confirm” button.
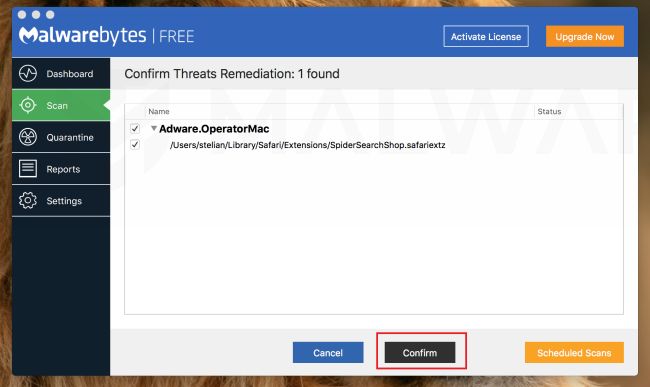
Malwarebytes will now remove all the malicious files that it has found. To complete the malware removal process, Malwarebytes may ask you to restart your device.
The “Trojan.U83” pop-ups should now be removed from your device. If you are still experiencing problems while trying to remove the Trojan.U83 pop-ups from your Mac, please ask for help in our Malware Removal Assistance for Mac forum.



