Airdrops are one of the most popular ways cryptocurrency projects attract attention and reward their communities. Free tokens in exchange for participation or loyalty can sound like a win-win situation. Unfortunately, scammers have capitalized on this excitement by creating fraudulent airdrop portals that trick users into connecting their digital wallets and unknowingly authorizing malicious contracts.
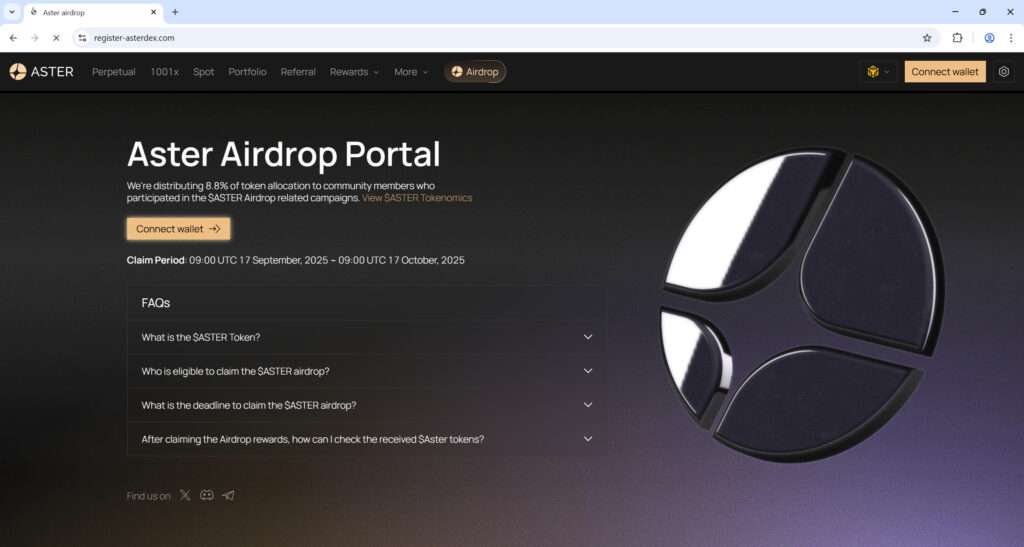
One such scheme is the Aster Airdrop Scam, which has surfaced on websites mimicking the official Aster DEX platform. These scam pages, such as register-asterdex.com, pretend to distribute free $ASTER tokens but are, in reality, a front for a sophisticated crypto drainer. If you connect your wallet, you risk losing all of your digital assets — sometimes within seconds.
This article provides a detailed breakdown of the Aster Airdrop Scam, explaining how it works, what makes it convincing, how to recognize red flags, and most importantly, what to do if you’ve already fallen victim. By the end, you’ll have a clear understanding of the risks and the steps necessary to protect your cryptocurrency holdings.
Scam Overview: The Fake Aster Airdrop
What is Aster?
Aster is presented as a decentralized exchange (DEX) platform that focuses on multi-chain trading and advanced trading tools. Like many real DEX projects, Aster has built a community of crypto enthusiasts who are always on the lookout for updates, token distributions, and new features. This makes Aster — and projects like it — an attractive target for scammers who exploit brand recognition.
The Rise of Fake Airdrops
Legitimate airdrops are common in the crypto ecosystem. They often reward early adopters or incentivize users to participate in governance. However, the popularity of airdrops has created the perfect opportunity for cybercriminals. Fake airdrops prey on the promise of free tokens by setting up fraudulent websites that look nearly identical to official project portals.
In the case of the Aster Airdrop Scam, attackers registered domains such as register-asterdex.com that closely resemble the legitimate Aster DEX site. They copied branding elements like logos, color schemes, and FAQ layouts to build trust. At first glance, the site appears professional, with sections like “Claim Period,” “FAQs,” and wallet connection options that mimic legitimate platforms.
How Victims are Lured
Scammers use multiple strategies to direct unsuspecting users to these fraudulent portals:
- Paid ads and promoted posts on social media platforms.
- Phishing links sent through Telegram, Discord, or email.
- Compromised accounts of influencers or community members that share the fake link.
- Search engine manipulation, where fake websites rank higher than official ones during critical campaign periods.
Once victims land on the fake site, they are greeted with enticing messages such as:
- “Claim your $ASTER tokens now!”
- “8.8% of total supply allocated to community members.”
- “Claim ends in 30 days — don’t miss out.”
This sense of urgency creates fear of missing out (FOMO), which pressures users into acting quickly without carefully verifying the site.
The Wallet Connection Trap
At the heart of the scam lies the “Connect Wallet” button. The fake Aster site offers multiple wallet options, including:
- MetaMask
- Trust Wallet
- WalletConnect (via QR code)
- Uniswap Wallet
- “All Wallets”
This familiar interface is exactly what users expect from legitimate airdrops. Once clicked, the site prompts users to connect their wallet and sign a transaction. But instead of authorizing a legitimate airdrop, users unknowingly sign a malicious smart contract that grants attackers broad permissions.
The Role of Crypto Drainers
The malicious contract embedded in these scam sites functions as a crypto drainer. A drainer is a mechanism that siphons funds from connected wallets after the victim grants approval. Unlike direct theft, which requires hacking into a wallet, drainers exploit the permission system in decentralized finance (DeFi). Once you sign an approval giving the drainer contract access, it can move your funds automatically — often prioritizing the most valuable tokens in your wallet.
Why This Scam Works
- Polished design: The site mimics the official brand with professional visuals.
- Social engineering: Urgency and exclusivity push victims to act fast.
- Familiar flow: Wallet connection modals look identical to legitimate ones.
- Complexity of permissions: Many users don’t fully understand what signing an approval actually means.
- Irreversibility of crypto: Once funds are drained, they cannot be recovered by simply calling customer support.
The Real Danger
The Aster Airdrop Scam is not just about losing a few tokens. Victims risk losing:
- Stablecoins (USDT, USDC, DAI).
- High-value tokens (ETH, BNB, MATIC).
- NFTs stored in the same wallet.
- Access to future funds if allowances are not revoked.
Some drainers even remain active for weeks, automatically siphoning any new assets that enter the compromised wallet.
How the Scam Works
Understanding the mechanics of the scam can help you spot it early and avoid falling victim. Here’s a step-by-step walkthrough of how the Aster Airdrop Scam operates:
Step 1: Distribution of Links
Attackers spread the fraudulent link across social platforms, crypto forums, and even through Google ads. Users see these links while searching for “Aster airdrop” or following community announcements. The fake domain looks close enough to the original to pass a casual glance.
Step 2: Arrival at the Fake Portal
When users click the link, they are taken to a sleek website with:
- A claim timer (e.g., “Claim ends October 17, 2025”).
- FAQ sections explaining what the $ASTER token is.
- The prominent “Connect Wallet” button.
The page is designed to look trustworthy, often including fake social media links and tokenomics charts.
Step 3: The Wallet Connection Prompt
Clicking “Connect Wallet” brings up a modal with multiple wallet options. Users who proceed are asked to sign a transaction. For experienced users, this is routine behavior — many dApps require approvals to interact. This familiarity is what makes the scam so effective.
Step 4: Malicious Contract Approval
The transaction isn’t about claiming free tokens at all. Instead, it is a malicious contract requesting approval to access your wallet’s assets. Often, this is an “infinite allowance” approval, which means the contract can spend as much of your tokens as it wants.
Step 5: Activation of the Crypto Drainer
Once approval is granted, the drainer becomes active. It scans the wallet to identify assets of value, then executes transfer functions to move tokens to attacker-controlled addresses. In some cases:
- The drainer immediately drains all available assets.
- It selectively drains high-value tokens first.
- It waits silently, siphoning new assets as they arrive.
Step 6: Laundering the Stolen Funds
The stolen funds are quickly swapped into stablecoins or privacy-focused tokens. Attackers may use decentralized exchanges, cross-chain bridges, or mixers to obfuscate the trail before cashing out on centralized exchanges.
Step 7: Recycling the Scam
Once one domain is flagged, scammers register new domains with slight variations. The campaign continues, targeting new victims who are unaware of the warnings.
What to Do If You Have Fallen Victim
If you connected your wallet to the Aster Airdrop Scam or signed a suspicious transaction, follow these steps immediately:
- Stay calm and act quickly. Time is critical, but panic can cause mistakes.
- Disconnect your wallet from the scam site. While this doesn’t revoke approvals, it stops further direct interaction.
- Check for malicious approvals. Use tools like Revoke.cash or Etherscan Token Approval Checker to review and revoke suspicious allowances.
- Move remaining funds. Transfer any unaffected tokens to a brand-new wallet with a new seed phrase. Do not reuse compromised wallets.
- Secure your seed phrase. If you entered your seed phrase anywhere on the scam site, assume full compromise. Create a new wallet and migrate funds immediately.
- Document everything. Save screenshots, transaction hashes, and domain details. This may help with reporting and investigations.
- Report the scam. Notify:
- The legitimate Aster project team.
- Your wallet provider (MetaMask, Trust Wallet, etc.).
- Anti-phishing organizations and regulators.
- Consider forensic services. For large losses, blockchain forensics firms can trace stolen funds and potentially work with exchanges to freeze them.
- Educate others. Share warnings in crypto communities to prevent others from falling into the same trap.
The Bottom Line: Staying Safe from Airdrop Scams
The Aster Airdrop Scam is a powerful reminder that not all airdrops are legitimate. Scammers are leveraging polished designs, trusted brand names, and the promise of free tokens to lure unsuspecting users into giving away access to their wallets. Once approvals are granted, crypto drainers can silently and efficiently steal assets without any further action from the victim.
To protect yourself:
- Always verify domains and announcements through official channels.
- Never rush into connecting your wallet to claim tokens.
- Regularly audit and revoke token approvals.
- Store long-term holdings in hardware wallets.
By staying cautious, informed, and proactive, you can enjoy the benefits of the crypto ecosystem without falling prey to malicious actors. Remember: if it sounds too good to be true, it probably is.
Frequently Asked Questions About the Aster Airdrop Scam
What is the Aster Airdrop Scam?
The Aster Airdrop Scam is a fraudulent scheme that impersonates the legitimate Aster DEX platform. Scammers set up fake websites, such as register-asterdex.com, claiming to distribute free $ASTER tokens. Victims are tricked into connecting their digital wallets and signing approvals that grant malicious smart contracts access to their funds. These approvals enable a crypto drainer to automatically siphon tokens, stablecoins, and NFTs from compromised wallets.
How does the Aster Airdrop Scam work?
The scam follows a predictable step-by-step process:
- Victims are lured to fake airdrop portals through ads, phishing messages, or search engine results.
- The fraudulent site mimics the official Aster DEX, complete with branding, FAQs, and a “Claim Now” button.
- Users are prompted to connect their wallets via MetaMask, Trust Wallet, WalletConnect, or similar services.
- The site requests a signature or approval transaction. This approval secretly grants the attacker contract permission to transfer tokens.
- A drainer script immediately scans the wallet and transfers high-value assets to attacker-controlled addresses.
This process is highly automated, meaning funds can disappear within minutes of signing the transaction.
Is the Aster airdrop real?
No. The so-called “Aster Airdrop” circulating on domains like register-asterdex.com is completely fake. It has no connection to the legitimate Aster DEX platform or any genuine cryptocurrency project. Any site asking you to connect your wallet to claim $ASTER tokens is a scam designed to steal your assets. Always verify official announcements through Aster’s verified channels before participating in promotions.
What happens if I connect my wallet to the fake Aster site?
Connecting your wallet alone doesn’t immediately drain your funds, but it exposes you to risk. If you sign an approval or contract request, the malicious smart contract gains permission to move tokens on your behalf. This can result in:
- Loss of ERC-20 tokens like ETH, BNB, MATIC, USDT, or USDC.
- Theft of NFTs linked to your wallet.
- Continuous draining of new funds if allowances remain active.
Can I recover funds stolen by the Aster Airdrop Scam?
Unfortunately, blockchain transactions are irreversible. Once your tokens are transferred to attacker-controlled wallets, they cannot be reversed. However, you can take steps to mitigate further losses:
- Immediately revoke approvals using tools like Revoke.cash or Etherscan Token Approval Checker.
- Transfer any remaining assets to a secure new wallet.
- Report the scam to the legitimate Aster team, wallet providers, and cybercrime authorities.
- If large sums are stolen, consult blockchain forensic firms that may trace and freeze assets on centralized exchanges.
How do I check if my wallet was compromised?
You can check for suspicious approvals and drainers using:
- Revoke.cash (supports multiple blockchains).
- Etherscan Token Approval Checker (for Ethereum).
- BscScan or PolygonScan (for BNB Chain and Polygon).
Look for allowances granted to unknown or suspicious contracts. If you see unlimited approvals, revoke them immediately.
How can I avoid falling victim to fake airdrop
Here are some proven ways to avoid scams like the Aster fake airdrop:
- Verify domains: Always type the URL manually or use bookmarked official sites.
- Check announcements: Only trust news from official project accounts, not random posts or ads.
- Beware of urgency: Phrases like “limited time only” are classic red flags.
- Audit approvals regularly: Revoke unused or suspicious permissions.
- Use hardware wallets: Keep long-term holdings in cold storage to limit exposure.
Why do scammers use airdrops as bait?
Airdrops are effective lures because:
- They promise free tokens, appealing to both new and seasoned investors.
- Many legitimate projects run airdrops, so the scam feels plausible.
- The process (wallet connection + signing) mimics real DeFi interactions, lowering suspicion.
- The urgency of “claim before the deadline” pressures victims to act without verifying.
What should I do immediately if I connected to the scam site?
If you interacted with the fake Aster airdrop site, take these actions immediately:
- Revoke token approvals using Revoke.cash or Etherscan.
- Transfer remaining funds to a secure, uncompromised wallet.
- Do not reuse the compromised wallet for storing assets.
- Report the scam to prevent others from falling victim.
- Document transaction IDs and addresses for forensic analysis.
Can disconnecting my wallet from the site protect me?
No. Simply disconnecting your wallet from a website only prevents further interaction with that site. It does not revoke token allowances or permissions you may have granted. To truly protect your assets, you must revoke approvals on-chain using dedicated tools.
Are other similar scams active?
Yes. The Aster fake airdrop is part of a larger wave of airdrop and drainer scams that target multiple projects. Other campaigns impersonate popular DEXs, DeFi protocols, and NFT projects. Scammers constantly cycle new domains and branding, so vigilance is necessary. If you see an unsolicited airdrop promotion, always assume it could be fake until verified.


![Remove Ad Block North Extension [Virus Removal Guide] 10 1 83](https://malwaretips.com/blogs/wp-content/uploads/2025/08/1-83-290x290.jpg)