In today’s turbulent job market, scammers are capitalizing on desperate job seekers by promoting fraudulent “work-from-home” opportunities. One prolific scam that has recently emerged is the fake “Brecks Group” recruitment scam.
The fake “Brecks Group” recruitment scam targets victims via spam emails, texts, social media posts, and messaging apps. By promising outrageous salaries and benefits for a “remote” customer service or data entry role, the scammers hook unsuspecting applicants. However, the “job” is merely a facade to siphon money from the victims.
This article will provide an in-depth look at how the fake Brecks Group recruitment scam operates. Understanding the tactics and psychology behind this racket can help job seekers avoid this malicious trap.
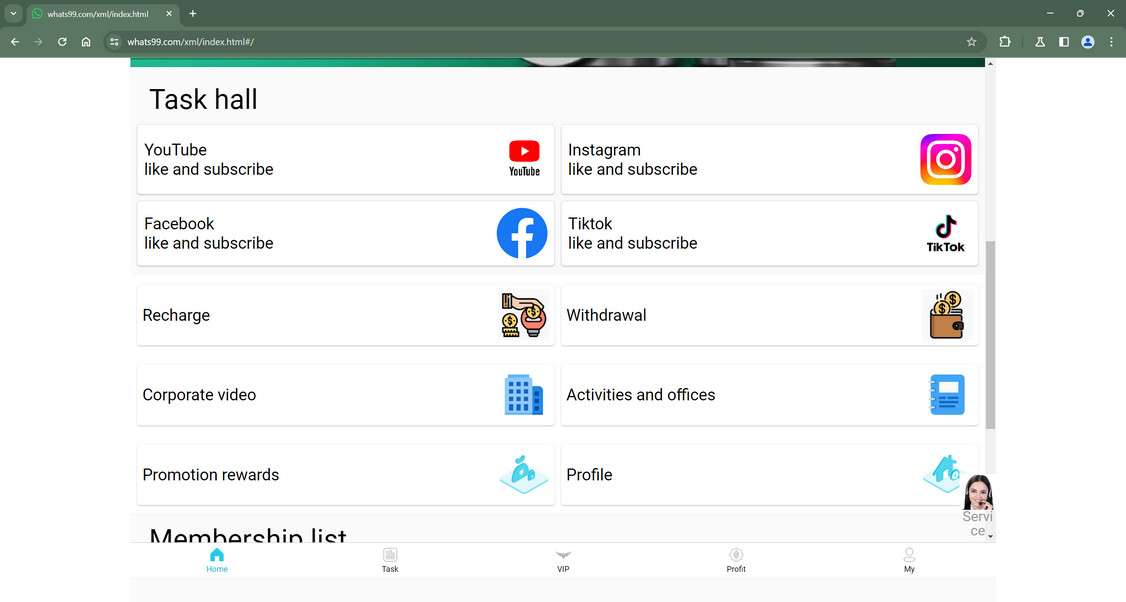
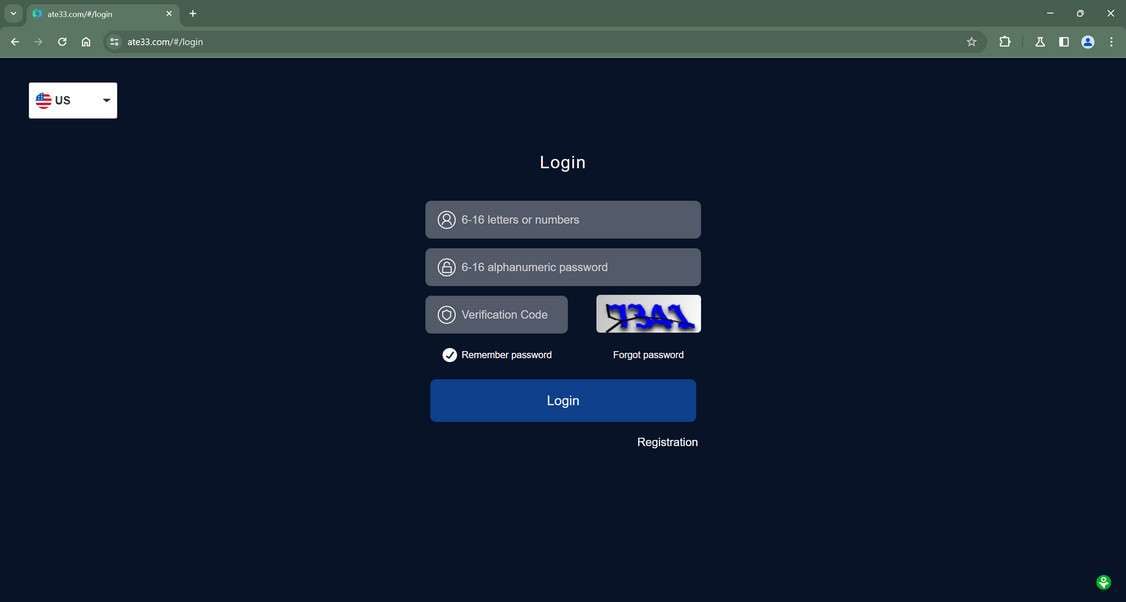
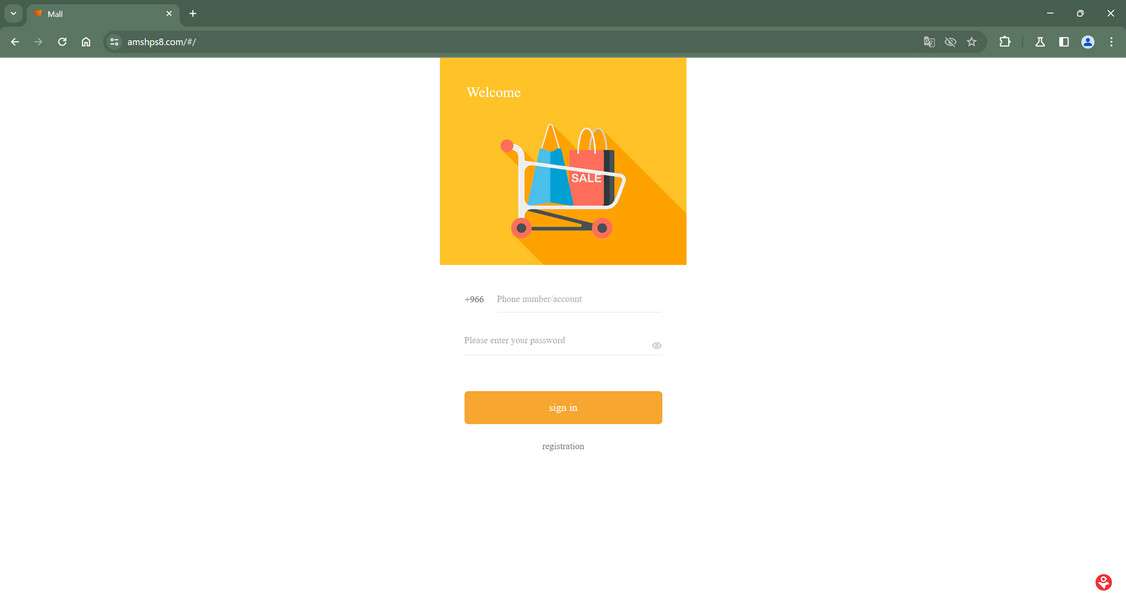
Overview of the Scam
The Brecks Group job offer scam preys on job seekers by falsely claiming to be the legitimate Brecks Group company. This real company has no association with the scam. By illegitimately using the trusted Brecks Group name, the scammers send messages advertising fictional customer service or data entry openings to dupe victims.
The scam job postings are usually vague one-liners sent via text/SMS, email, social media platforms, job boards, or messaging apps. They read something like:
- “You applied to our customer service agent role. Interview immediately for $24/hour work from home job.”
- “Your resume fits our data entry clerk position. Huge benefits. Text back to schedule an interview.”
- “Looking for people nationwide to fill remote customer service roles. No experience required. Message to learn more about this opportunity.”
These messages often show up out of the blue and reference some kind of application or resume the recipient supposedly submitted. To make the texts and emails appear more legitimate, the scammers sometimes purchase stolen resumes and contact lists on darknet cybercrime markets. So the messages may contain personal details that make the recipient believe it is a genuine recruiter.
Other times, the scammers blanket spam the messages en masse to millions of phone numbers, emails, and social media accounts. With so many people desperately looking for jobs, they assume a certain percentage will take the bait.
The messages dangle tantalizing details about the supposed jobs to build interest:
- Work from home – no need to commute or relocate
- Flexible hours – set your own schedule
- $20-$30 per hour salaries with quick “pay increases”
- Excellent benefits like health/dental insurance, 401K plans, paid time off
- No prior experience required – we train you fully
- Easy training done completely online
- Cutting-edge training software and tools provided
For someone unemployed and urgently needing income, the opportunity seems almost too good to be true. Which, unfortunately, is the case. But the scammers rely on the victims’ confirmation bias to overlook any red flags.
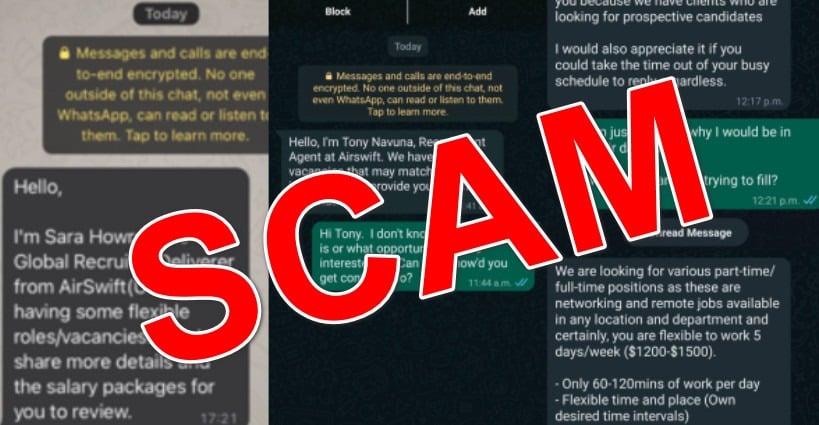
If interest is expressed, the applicant is told to continue the “hiring” process over encrypted messaging apps like WhatsApp, Signal, or Telegram. This allows the scammers conceal their identities and operate anonymously.
The elaborate job interview hoax conducted over these apps forms the core the scam. Applicants are asked to complete peculiar “training” by accessing special software portals. However, these systems are actually just mechanisms to steal cryptocurrency from the victims.
The WhatsApp/Telegram contacts, training portal domains, and any other presence the scammers establish eventually vanish without a trace once funds are extracted. Millions in stolen crypto gets laundered through complex systems so it disappears forever.
Left devastated, the victims have little recourse. The scammers have phony names attached to disposable messaging accounts. The training portal and domains are registered anonymously or with stolen identities. Any payments were made via non-reversible cryptocurrency channels.
Read on to learn how this scam tricks victims.
How the Fake Brecks Group Job Scam Works
The Brecks Group job offer scam ensnares victims through expert social engineering techniques across multiple channels. Here is a step-by-step look at how the con unfolds:
Step 1: Casting a Wide Net via Spam Messages
The scammers blast out mass spam emails and text messages advertising the fake customer service job opportunity. Short messages often read:
“Your resume matched a remote work opening with our company. Salary is $24/hr. Text back for details.”
Messages like this are vague enough to elicit responses from the widest possible audience.
Other times, the scammers purchase or steal actual resumes and contact lists to make their messages appear more targeted and legitimate. They might reference details from your resume, previous work history, or skills.
In addition to emails and texts, the scammers also blanket social media sites like Facebook, Instagram, and LinkedIn with posts about the openings.
Step 2: Moving the Conversation to Anonymous Platforms
If a recipient responds with interest in the role, the scammers immediately attempt to move the conversation to more anonymous platforms like WhatsApp or Telegram.
Their initial response often states:
“Thanks for your interest in Brecks Group! Please message hiring manager Vivian Hughes on WhatsApp at [phone number] to schedule an interview immediately.”
Chatting over WhatsApp or Telegram allows the scammers to hide their real identities and operate with impunity.
Step 3: The Fake “Interview”
The elaborate job interview hoax is the centerpiece of the scam. Once on WhatsApp/Telegram, the applicant is contacted by a person posing as a hiring manager or interviewer.
After asking a few cursory questions about your resume and interests, the faux interviewer explains the peculiarities of this “work-from-home” job:
- You must complete online “training” using special software programs. This is in lieu of traditional new hire training.
- The training software charges fees in Bitcoin/ETH/USDT cryptocurrency for “access passes.” Do not worry, the company will reimburse you after training.
- Each training module you complete will add funds to your online account balance. Once training is finished, you can withdraw your reimbursed wages.
The applicant is then sent links to the “training portal,” which is essentially a scam website crafted to steal cryptocurrency payments.
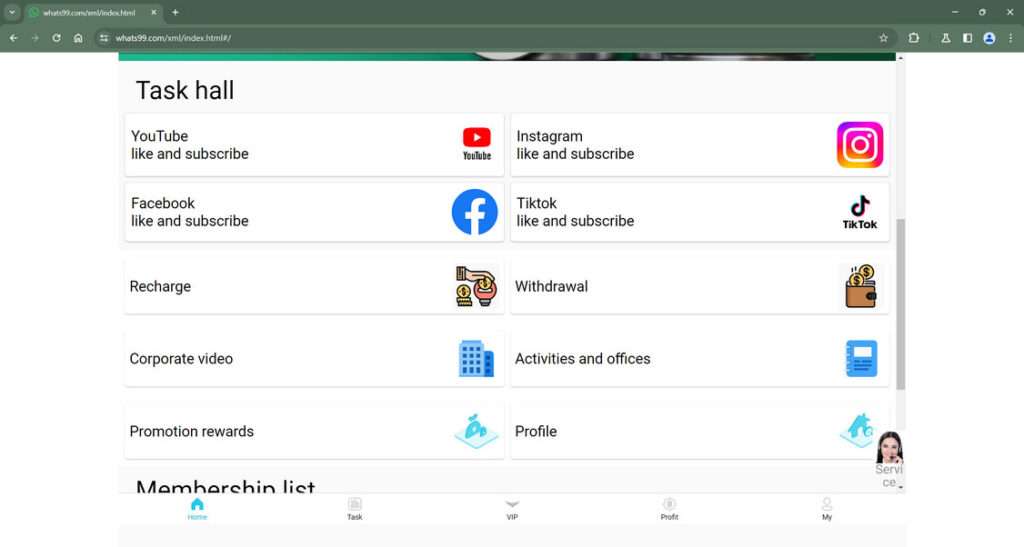
Step 4: The Crypto Training Portal
The training portal, often hosted through a generic domain with a .shop or .vip extension, looks like an amateur web app. It has a login page, account dashboard, and menu of “training modules.”
The modules instruct you to complete meaningless tasks like:
- Watching videos
- Liking social media posts
- Downloading apps
- Buying products
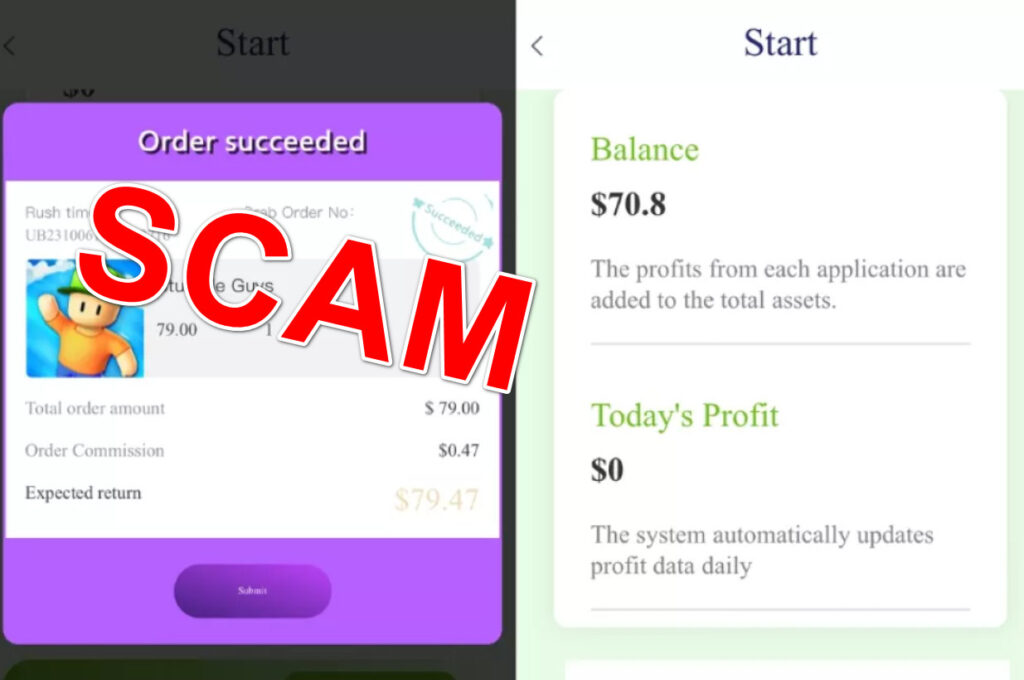
After finishing each task, your account balance increases. However, after accruing a certain amount, you are prompted to “recharge” the account with cryptocurrency to continue.
The pass prices range from $50-500 in Bitcoin, Ethereum, Tether, or other coins. If you pay, the cycle continues until you are drained of all funds or realize it’s a sham.
Step 5: Disappearing Act
Once the victim finally recognizes the job is fake, the scammers immediately delete all their accounts and vanish without a trace.
The WhatsApp numbers, Telegram contacts, training portal, and any other presence they established evaporates. Poof – millions in stolen crypto also disappears, usually routed through complex money laundering systems.
The victim is left distraught, embarrassed, and financially devastated. The scammer moves on to repeat the process with their next target.
Upfront Fee Variations
In some reported cases, the Brecks Group job scammers request victims pay an upfront “processing fee” or “equipment fee” before starting the fake online training.
After moving the conversation to WhatsApp or Telegram, the scammer posing as the hiring manager tells the applicant something like:
“Thanks for your interest in the customer service role! We are excited to have you start training and join our team. Our final step is collecting a $200 processing fee and then I can set up your training account. Let me know once you’ve sent the fee payment and we can proceed.”
In other variations, the scammers claim the victim needs to purchase a computer or other equipment in order to properly complete the training:
“Great news, you are hired! Our last step is having you procure the required computer equipment for this work-from-home position. Please purchase the items below for $500 total through our approved vendor. Send me the order confirmation and I will get your training login set up.”
The scammers then provide payment details to wire the funds or purchase gift cards/prepaid debit cards.
However, in both scenarios, once the upfront “processing” or “equipment” fee is paid, the scammers cease all communication and disappear with the money. No training or job ever materializes.
These upfront fee variations demonstrate how the scammers are constantly evolving their tactics to trap victims within the Brecks Group recruitment scam. Job seekers should be wary of any recruiter demanding payments before officially starting training or work. Legitimate companies do not operate this way. If pressured for upfront fees, cease all contact immediately.
What To Do If You Are A Victim
If you already engaged with the scammers and suffered financial losses, here are some important steps to take:
Step 1: Document Everything
Gather all the evidence you can about your experience. This includes:
- Chat logs of your conversation history with the scammers. Take screenshots.
- The job scam emails/texts/posts they used to contact you initially.
- Screenshots of the training portal pages and tasks.
- Records of any cryptocurrency payments you made.
Preserve this documentation – it can help law enforcement track down the criminals.
Step 2: Report the Incident
File reports about the scam to relevant government agencies:
- Call your local police department. Provide the evidence and get an incident report number.
- Submit a complaint to the FBI’s Internet Crime Complaint Center at www.ic3.gov.
- Contact the Federal Trade Commission (FTC) via their online reporting tool or 877-FTC-HELP.
- Report cryptocurrency payments to Coinbase if applicable. They investigate crypto scams.
- Alert social media platforms like WhatsApp, Telegram, Instagram, etc.
Step 3: Notify Your Bank
Contact your bank and any other financial institutions that may linked to payments you made. Alert them that your accounts may have been compromised.
Discuss options for recovering lost funds, cancelling compromised cards/accounts, or disputing fraudulent charges. Your swift action can limit damages.
Step 4: Adjust Security Settings
Secure your online presence and accounts to avoid repeat victimization:
- Change passwords, security questions, and enable two-factor authentication everywhere possible.
- Remove personal details from online profiles that scammers can exploit.
- Block contacts, numbers, and emails associated with the scam.
Staying vigilant can help deter future scams as you continue your job search.
Frequently Asked Questions about the Brecks Group Job Scam
The Brecks Group recuritment scam tricks many victims through clever social engineering. Here are answers to some frequently asked questions about this prolific con.
What is the Brecks Group Job Scam?
The Brecks Group recruitment scam is a fraudulent work-from-home job offer used to steal money from applicants. Scammers posing as the real “Brecks Group” company blast messages advertising customer service, brand ambassadors, or data entry openings. They trick victims into paying crypto fees for fake online “training.”
How do the scammers first contact potential victims?
Scammers cast a wide net with spam texts, emails, social posts, and messages about remote jobs at Brecks Group. Vague messages offering high salaries, great benefits, and flexible hours hook targets.
What platforms do they use to communicate?
Initial outreach is via mass spam texts, emails, job sites, and social media. However, they quickly try to move communications to anonymous platforms like WhatsApp and Telegram.
What happens during the fake interview?
Via WhatsApp/Telegram, scammers posing as hiring managers conduct absurd interviews. They tell applicants to complete peculiar online training involving watching videos, liking posts, downloading apps, and buying products.
How does the training portal work?
The portal is a scam website that has victims complete meaningless tasks. After each task, account balances increase. But victims soon must buy crypto “access passes” to continue, which is how the scammers steal funds.
What types of cryptocurrency do victims have to pay?
Scammers demand payment in untraceable coins like Bitcoin, Ethereum, Tether, and others. Access pass fees range from $100 – $500. Victims are drained of money through repeated pass purchases.
How much money have victims lost in this scam?
Total losses are unknown, but likely in the millions in stolen cryptocurrency. The criminals vanish after extracting funds, leaving victims with no recourse.
What techniques do the scammers use?
The con relies on social engineering tricks like conveying a sense of urgency, name dropping legitimate companies, dangling tempting offers, isolating victims on anonymous platforms, and gradual escalation.
What should you do if you encountered this scam?
If you paid any money, document everything, file police reports, notify banks, and secure accounts. Report the scam to authorities at IC3, FTC, Coinbase, and social media platforms.
How can job seekers avoid this scam?
Carefully vet remote jobs, avoid anonymous interviewers, don’t pay fees, use official company domains, and steer clear of requests to chat over WhatsApp or Telegram.
Am I able to recover lost money paid to the scammers?
Unfortunately, recovery of lost cryptocurrency funds is very rare. The anonymity of the payment channels and complexity of money laundering techniques make it extremely difficult. Prevention is key.
Where can victims report this scam and get assistance?
You can report it to agencies like the FBI Internet Crime Complaint Center (IC3), Federal Trade Commission (FTC), Coinbase, local police, social media sites, and cybersecurity researchers.
The Brecks Group recruitment scam has wreaked havoc on job seekers. Being aware of their ruthless techniques is the best defense. With caution, you can identify fake job opportunities and focus efforts on legitimate openings. Don’t let these criminals deter your goals.
The Bottom Line
The Brecks Group recuitment scam reveals the dark side of modern unemployment woes. Scammers are getting extremely sophisticated, using emotional manipulation and elaborate ruses.
But by examining their exact tactics, job seekers can recognize the red flags early and avoid the trap. Do your due diligence, don’t communicate on anonymous channels, watch for unusual interview practices, and never pay strange cryptocurrency fees.
Stay skeptical yet hopeful in the job hunt. With awareness and caution, you can see through the scam and find legitimate opportunities. Don’t let the Brecks Group recruitment scam deter you. Know their tricks and improve defenses so their scheming ends in failure.


![Remove Nova-chainedge.com Pop-up Ads [Virus Removal Guide] 11 McAfee scam 4](https://malwaretips.com/blogs/wp-content/uploads/2023/08/McAfee-scam-4-290x290.jpg)