Phishing scams have become increasingly sophisticated in recent years, with cybercriminals constantly finding new ways to trick unsuspecting individuals into revealing their personal information. One such scam that has gained traction is the CPanel ‘Account Verification’ phishing scam. In this article, we will delve into what this scam is, how it works, what to do if you have fallen victim, and provide valuable insights to help you stay safe online.
![CPanel ‘Account Verification’ Phishing Scam [Explained] 1 Scams](https://malwaretips.com/blogs/wp-content/uploads/2023/07/Scams.jpg)
What is the CPanel ‘Account Verification’ Phishing Scam?
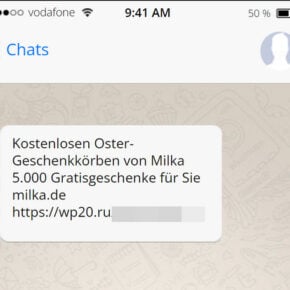
The CPanel ‘Account Verification’ phishing scam is a type of cyber attack where scammers impersonate the popular web hosting control panel, CPanel, to trick users into revealing their login credentials and other sensitive information. CPanel is widely used by website owners and administrators to manage their websites, making it an attractive target for cybercriminals.
The scam typically begins with an email that appears to be from CPanel, informing the recipient that their account needs to be verified due to a security breach or an update in the system. The email often includes the CPanel logo and uses official-sounding language to create a sense of urgency and legitimacy.
How Does the Scam Work?
Once the recipient clicks on the link provided in the email, they are directed to a fake CPanel login page that looks identical to the legitimate one. Unbeknownst to the victim, their login credentials are captured by the scammers when they enter them on the fake page.
After obtaining the login credentials, the scammers can gain unauthorized access to the victim’s CPanel account. This gives them control over the victim’s website, allowing them to steal sensitive data, inject malicious code, or even take the website offline.
Example:
Let’s consider an example to illustrate how the CPanel ‘Account Verification’ phishing scam works:
- The victim receives an email that appears to be from CPanel, stating that their account needs to be verified due to a security breach.
- The email contains a link that directs the victim to a fake CPanel login page.
- The victim enters their login credentials on the fake page, believing it to be the legitimate CPanel login.
- The scammers capture the login credentials and gain unauthorized access to the victim’s CPanel account.
- The scammers can now manipulate the victim’s website, steal sensitive data, or cause other malicious activities.
What to Do If You Have Fallen Victim?
If you have fallen victim to the CPanel ‘Account Verification’ phishing scam, it is crucial to take immediate action to minimize the damage. Here are the steps you should follow:
- Change your passwords: Start by changing the password for your CPanel account. Make sure to choose a strong, unique password that is not used for any other accounts.
- Scan for malware: Run a scan with Malwarebytes Free or any reputable antivirus software to check for any malware or malicious code that may have been injected into your website.
- Review your website: Carefully review your website for any unauthorized changes, such as altered content, new files, or suspicious scripts. Remove any suspicious elements and restore your website to a clean state.
- Inform your hosting provider: Contact your hosting provider and inform them about the incident. They may be able to provide further assistance and guidance on securing your account and website.
- Monitor your accounts: Keep a close eye on your financial accounts, email accounts, and other online accounts for any suspicious activity. If you notice any unauthorized transactions or unusual behavior, report it immediately.
Technical Details of the Scam
The CPanel ‘Account Verification’ phishing scam relies on social engineering techniques to deceive users. By impersonating a trusted brand like CPanel and creating a sense of urgency, scammers manipulate victims into divulging their login credentials.
The scammers often use techniques such as email spoofing to make the email appear as if it is coming from a legitimate CPanel address. They may also use domain names that closely resemble the official CPanel domain to further deceive the victims.
Furthermore, the fake login page used in the scam is designed to closely mimic the legitimate CPanel login page. This includes replicating the design, layout, and even the SSL certificate to make it appear secure.
Statistics on Phishing Scams
Phishing scams, including the CPanel ‘Account Verification’ phishing scam, continue to be a significant threat in the digital landscape. Here are some statistics that highlight the prevalence and impact of phishing:
- According to the 2021 Phishing Activity Trends Report by the Anti-Phishing Working Group (APWG), there were 222,163 unique phishing attacks reported in 2020.
- Phishing attacks cost businesses an estimated $1.8 billion in losses in 2020, according to the 2021 Cost of Cyber Crime Study by Accenture.
- According to the 2021 Verizon Data Breach Investigations Report, 36% of data breaches involved phishing attacks.
Conclusion
The CPanel ‘Account Verification’ phishing scam is a dangerous threat that can lead to unauthorized access to your website and potential data breaches. It is essential to stay vigilant and be aware of the tactics used by scammers.
If you receive an email claiming to be from CPanel asking for account verification, always double-check the email’s legitimacy before clicking on any links or providing any personal information. Remember, CPanel will never ask you to verify your account via email.
If you have fallen victim to the scam, follow the steps outlined in this article to mitigate the damage and secure your accounts. By staying informed and taking proactive measures, you can protect yourself and your online presence from phishing scams.