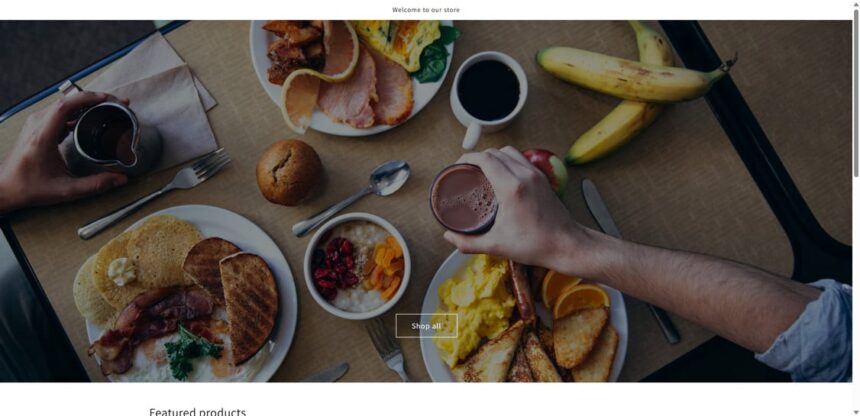
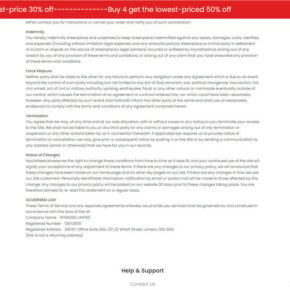
Yityba.shop – Scam or Legit? Why This Store Raises Concerns
This site looks legit at first glance, but the details tell a different story.
Most Read
Latest Scams

Nestshopp.com – Scam or Legit? Read This Shopper Warning
This site looks legit at first glance, but the details tell a different story.
Valerie-mason.com – Scam or Legit? Why You Should Be Careful
This site looks legit at first glance, but the details tell a different story.
Verefre.com – Scam or Legit? Read This Shopper Warning
This site looks legit at first glance, but the details tell a different story.
Ninecasino.c Crypto Casino Scam – What You Need To Know
The promo code is the hook. The “verification” deposit is the trap.
By Categories
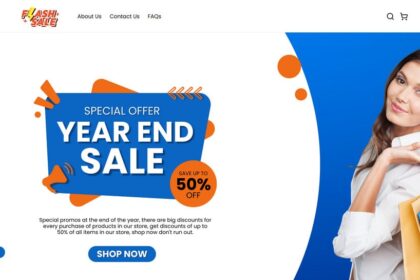
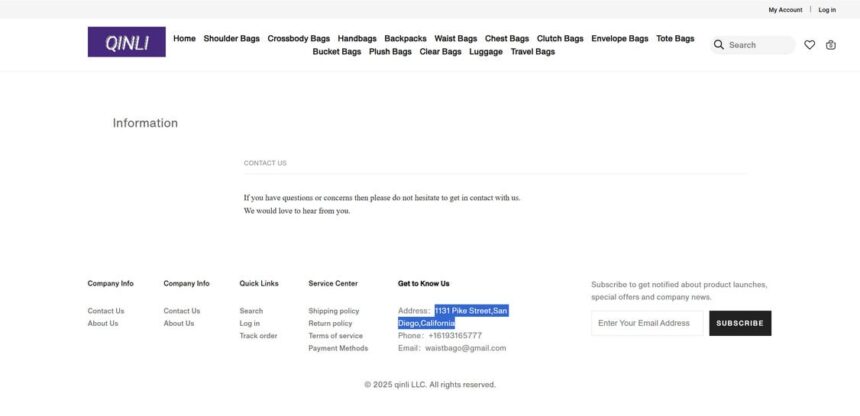
Waistbago.com – Scam or Legit? Buyers Report Serious Issues
This site looks legit at first glance, but the details tell a different story.
Featured
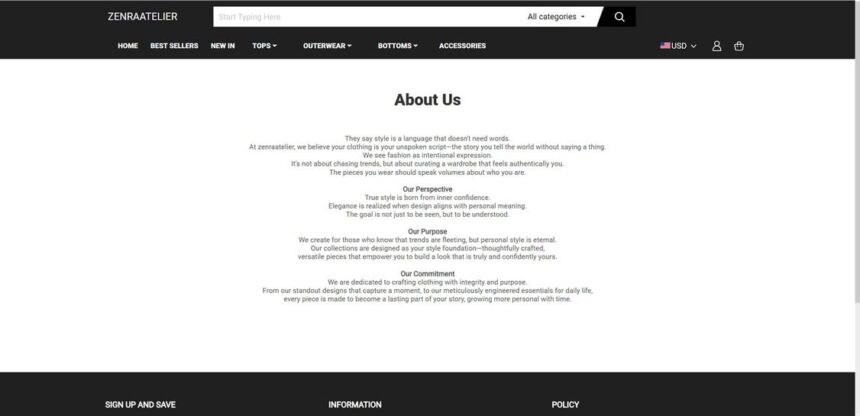
ZenraAtelier.com – Scam or Legit? The Red Flags We Found
This site looks legit at first glance, but the details tell a different story.
ZaveWin.cc Crypto Casino Scam – What You Need To Know
The promo code is the hook. The “verification” deposit is the trap.
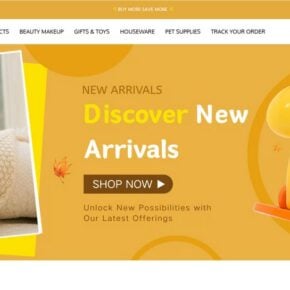
Pluspending.com Scam Store: What You Need To Know
This site looks legit at first glance, but the details tell a different story.
Popandpast.com Scam Store: What You Need To Know
This site looks legit at first glance, but the details tell a different story.
Primewinners.sbs Crypto Casino Scam – What You Need To Know
The promo code is the hook. The “verification” deposit is the trap.
Latest reports
Remove Soninlawalmighty.com Ads [Virus Removal Guide]
If your browser is constantly being redirected to the Soninlawalmighty.com site, then you likely have…
How to remove Noblok.biz adware (Virus Removal Guide)
If your web browser is constantly being redirected to the Noblok.biz site, then it is possible…
Don’t Let It Slide
Send it to us with any proof you have, and help us map the scam so more people can avoid it.

Check-tl-ver-18-3.com Virus: What Is It and How to Stop Pop-ups
Recently, many users have reported receiving intrusive pop-up notifications on their computers and mobile devices,…
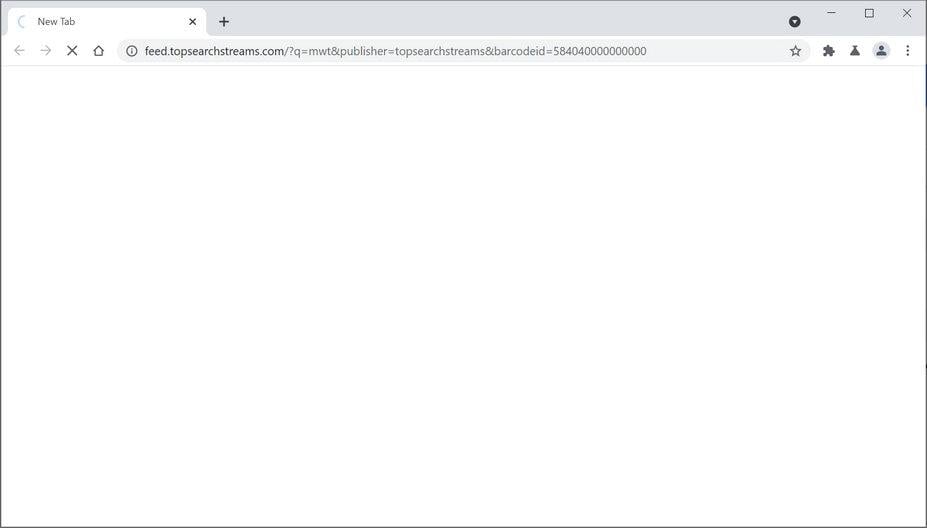
Remove TopSearchStreams Search redirect (Virus Removal Guide)
TopSearchStreams is a browser hijacker that will change your browser search engine to feed.topsearchstreams.com. This…
Spotted a Scam?
Scam Alert Time
Report what you saw and we’ll investigate the details, document the tactics, and warn others quickly.
Weekly top
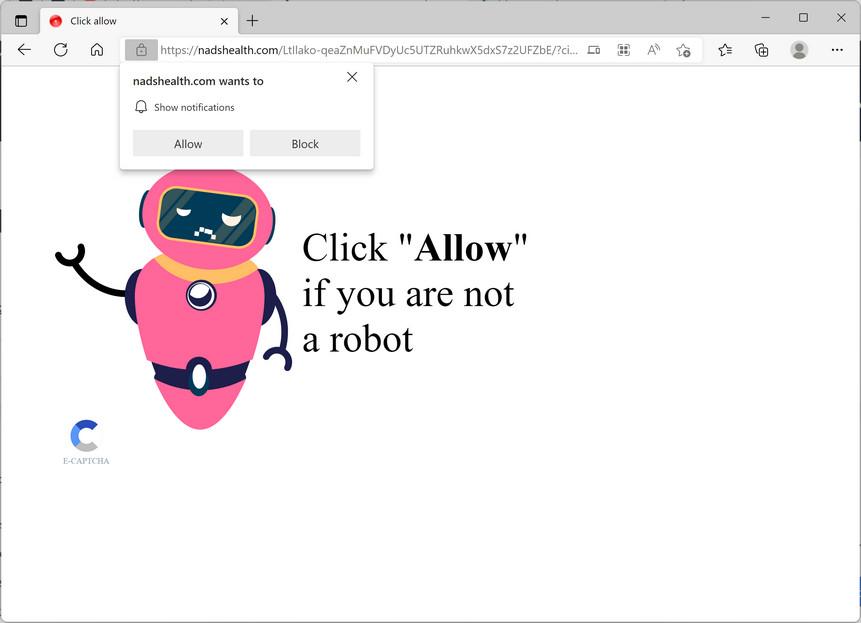
Remove Nadshealth.com Pop-up Ads (Virus Removal Guide)
Nadshealth.com is a site that tries to trick you into subscribing to its push notifications so that it can send…
Remove Dariolespace.com Pop-up Ads [Virus Removal Guide]
Dariolespace.com is a site that tries to trick you into subscribing to its push notifications so that it can send…
Remove MajorLetterSearch from Mac (Virus Removal Guide)
This guide teaches you how to remove MajorLetterSearch browser hijacker for free by following easy step-by-step instructions.
How to Remove Hotbtebiba.today Pop-Ups [Virus Removal Guide]
Hotbtebiba.today is a malicious website designed to trick users into enabling push notifications. It displays misleading prompts, urging visitors to…
Remove Calmer.live Ads (Virus Removal Guide)
If your web browser is constantly being redirected to the Calmer.live site, then you may have adware installed on your…
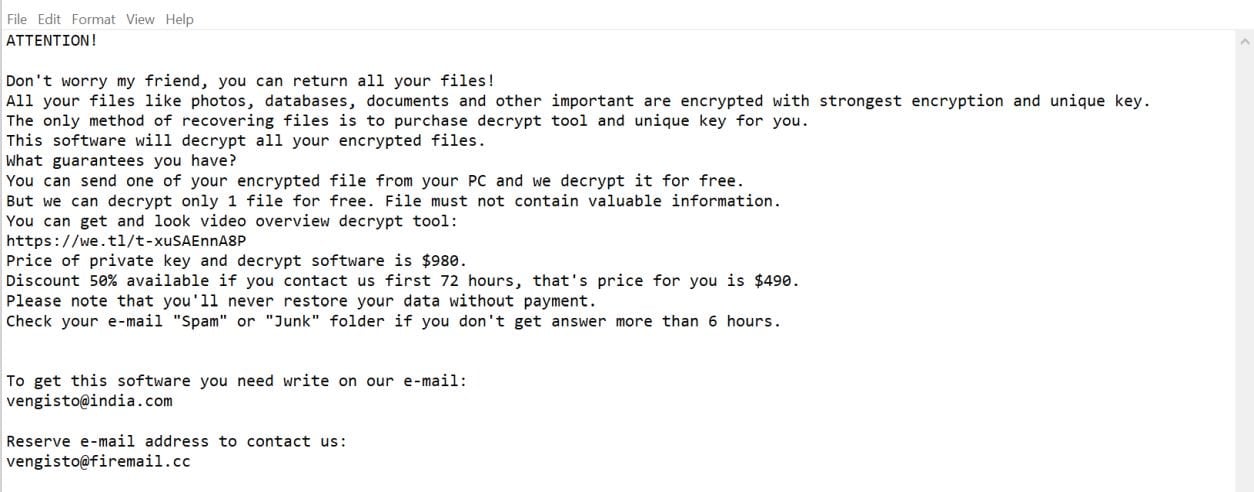
Remove Vengisto@india.com Norvas ransomware (Virus Removal Guide)
If your pictures, documents, or files are encrypted with a Norvas extension, then your computer is infected with the STOP…

Help Bust Scammers
Your report helps us connect the dots across domains, ads, and messages so the next person doesn’t get tricked.





![Remove Soninlawalmighty.com Ads [Virus Removal Guide] 42 Image: Chrome browser is redirected to Soninlawalmighty.com](https://malwaretips.com/blogs/wp-content/uploads/2023/04/soninlawalmighty.com-ad.jpg)

![Remove Dariolespace.com Pop-up Ads [Virus Removal Guide] 52 Dariolespace.com ads](https://malwaretips.com/blogs/wp-content/uploads/2023/06/Dariolespace.com-ads.jpg)