Pec1966.com is a fraudulent website that is being used as part of an elaborate job scam that has already defrauded victims out of an estimated €100 million globally. This scam operation involves using messaging apps to contact targets with fake job offers, directing them to complete tedious “training” on Pec1966.com, and extracting upfront fees from them under false pretenses.
In this comprehensive article, we will examine how the Pec1966.com scam works, break down the psychological manipulation tactics used, provide tips on avoiding becoming a victim, and detail steps for those unfortunate enough to have fallen prey to take.
Overview of the Pec1966.com Scam
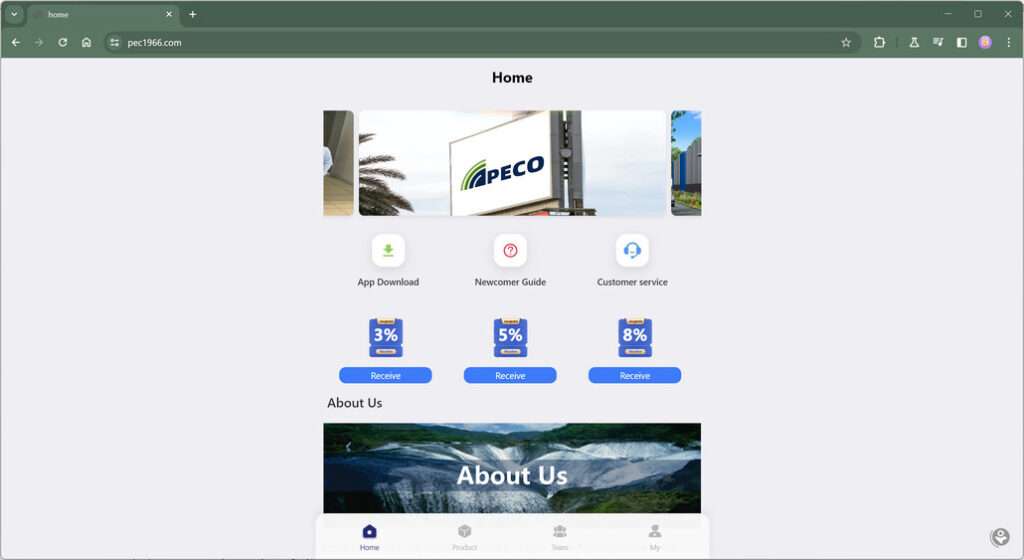
Pec1966.com is a fraudulent website that operates as part of an elaborate criminal scheme to steal money from job seekers across the globe. This insidious scam has extracted an estimated €100 million from trusting victims who believed they were being offered legitimate work opportunities.
The scam typically begins when a target receives an unsolicited message via WhatsApp, Telegram, text message, or another digital platform like Facebook from a person posing as a recruiter at a well-known company. The message convincingly states they saw the recipient’s resume online and would like to discuss an open position that seems like a great fit. If the target expresses interest, the “recruiter” responds with details about a vague but enticing work-from-home job, boasting high hourly wages for easy tasks.
Once hooked, the target is directed to Pec1966.com, which is presented as the “training platform” they must complete to get hired. But in reality, this site is the trap used to execute the scam. Victims are instructed to create accounts and complete mundane repetitive tasks, such as watching videos, clicking links, filling out forms, downloading apps, and even making purchased. They are awarded small sums like a few cents or dollars for each completed task, reinforcing the illusion that persevering on the platform will eventually result in the advertised high earnings.
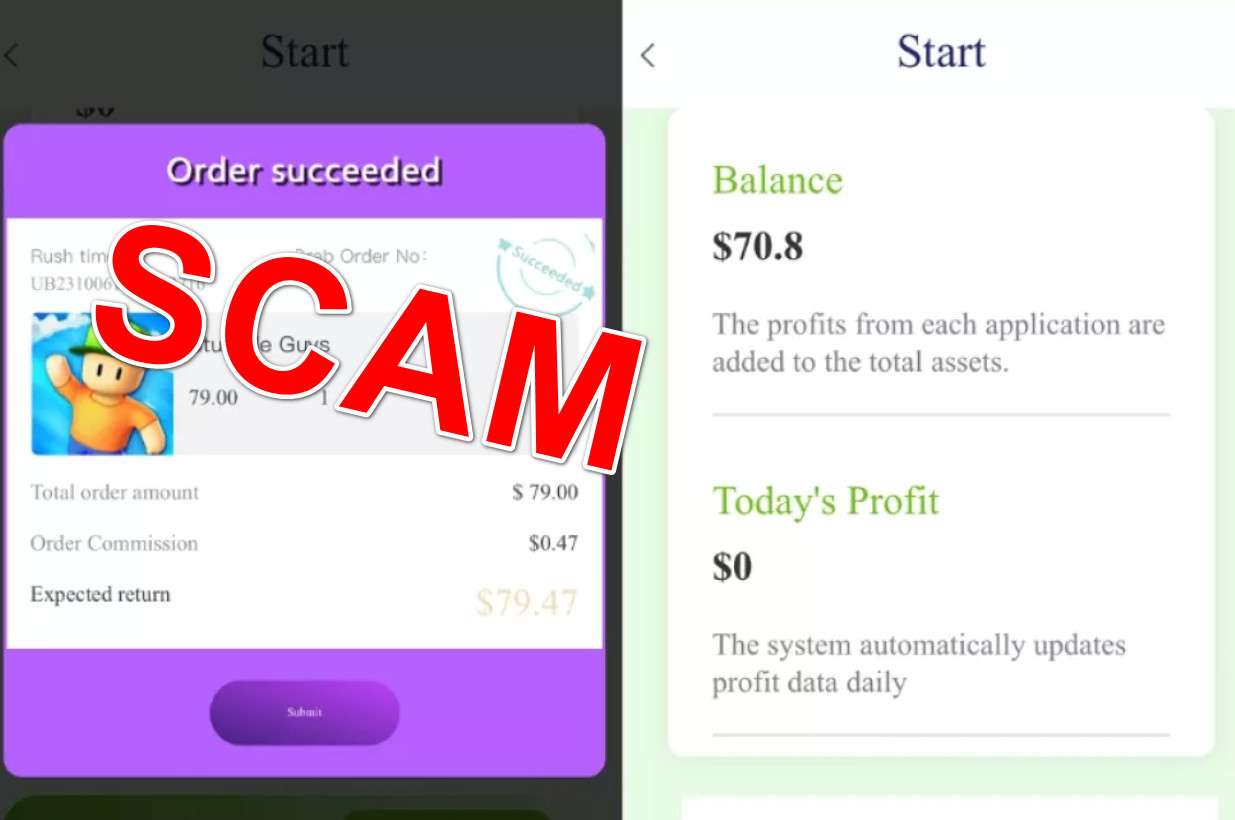
However, after grinding through the basic tasks, victims are soon informed they must purchase “upgrades” and pay escalating upfront fees to unlock higher value tasks necessary to reach the elevated pay levels originally promised. These upgrades can cost hundreds or even thousands of dollars. Victims are manipulated into paying the exponentially increasing fees through psychological tactics and false promises.
In the end, no matter how many tasks are completed or how much money is paid into the criminal-run Pec1966.com platform, the advertised earnings never materialize. Excuses are invented for why victims cannot withdraw their money, and then they are ghosted once no longer of use.
Detailed accounts from multitudes of victims reveal how technically sophisticated and deceitfully convincing this scam is. It exploits human emotions and vulnerabilities surrounding unemployment and financial instability. This drives people to ignore red flags and continue funneling money into the black hole of Pec1966.com long after it becomes clear it is a fraud.
There are multiple reported cases of victims paying enormous cumulative sums into Pec1966.com and associated sham platforms, sometimes even over $10,000. Tragically, this leaves devastated victims not only unemployed but now destitute and in debt. It can take years to recover, if ever, putting dreams, homes, and futures in jeopardy.
This extremely unethical scam is believed to be orchestrated by organized international criminal networks that strategically target English speakers in countries around the world. They operate Pec1966.com and other similar sites to systematically steal money from struggling job seekers. The ability to hide behind the anonymity of the internet allows them to perpetrate this scam with relative impunity.
How the Pec1966.com Scam Works
The criminals running the Pec1966.com scam have crafted a devious sequence of events to ensnare their victims while hiding the fraudulent nature of the operation. Here is a step-by-step breakdown of how this scam typically plays out:
Step 1 – Initial Contact
The first point of contact usually occurs via WhatsApp, Telegram, text message, or another messaging platform. The victim receives a text claiming to be from a recruiter at a reputable company and expressing potential interest in hiring the victim for a work-from-home job.
For example: “Hi this is Jennifer from Google. I came across your profile and think you’d be a great candidate for a virtual customer service job we are hiring for. Can I send you more details?”
This piques victims’ interest, as the message gives the appearance of a personalized job lead from a known legitimate company. In reality, the sender is a criminal posing as a recruiter using spoofing technology.
Step 2 – Offer of Fake Remote Job
If the victim responds asking for more information, the scammer sends a follow-up message pitching a work-from-home job opportunity that sounds very enticing:
“We are hiring online customer service reps to work remotely. You can set your own hours and earn up to $30/hr. Let me know if you’d like me to forward you info about the position!”
The flexibility, high pay, and remote nature make this sound like an unbelievable opportunity. This convinces victims to engage further with what they believe is a legitimate recruiter.
Step 3 – Directing to Pec1966.com
After expressing interest in the job, the victim is sent a link to Pec1966.com and told this is the website for the training program required before new hires can begin working. For example:
“Here is the portal for our virtual onboarding course – all new team members must complete training before accessing job systems and functions. Follow the course materials closely so you are ready to start!”
The professional look of Pec1966.com and the promise of getting hired after completing the “training” causes victims to believe this is a real job vetting process.
Step 4 – Completing Basic Tasks
Once at Pec1966.com, the victim must setup an account and complete a series of repetitive low-effort tasks described as the “training program” for the job, such as:
- Watching videos
- Clicking on links
- Filling out forms
- Submitting email addresses
- Downloading apps
- Making small purchases
The ability to complete these mundane tasks and earn a few cents to dollars convinces victims they are making real progress toward the lucrative job.
Step 5 – Escalating Fees for Upgrades
After finishing the beginner-level tasks, the victim is instructed they must now purchase “upgrades” to unlock higher earning tasks necessary to qualify for the job. These upgrades cost anywhere from $25 up to $500+ in fees.
Many desperate victims end up paying escalating upgrade fees ranging into the thousands, believing each payment gets them closer to unlocking the fake job. In reality, they are just fattening the wallets of scammers.
Step 6 – Zero Payout
Despite completing endless tasks and paying exorbitant upgrade fees, the promised payouts never materialize. Victims find it impossible to withdraw any earnings, receive vague excuses when trying to collect payment, and get ghosted when they are no longer useful to the scam.
No real job exists. Pec1966.com simply extracts as much money as possible from victims through deception and psychological manipulation, while providing zero income in return.
This carefully crafted process instills trust, makes victims feel invested in the “opportunity”, exploits psychological principles, and disguises the fact no legitimate work opportunity exists – only an incredibly sly scam.
Spotting Pec1966.com Scam Recruitment on Social Media
The criminals behind the Pec1966.com scam leverage popular social media platforms like Facebook and Instagram to find potential victims and initiate contact.
They create profiles presenting themselves as recruiters and HR professionals at reputable companies. The profiles seem legitimate at first glance, with a smattering of stock photos, motivational quotes, and made up career details. However, upon closer inspection, several red flags may arise:
- Profile was created recently and/or has very low number of posts and connections
- Vaguely lists a supposed recruiting role but for unnamed companies
- Uses generic stock images rather than photos of an actual person
- Lacks detailed employment history and verification badges
These fake recruiter profiles send out connection requests and messages to those looking for jobs, especially people who have openly posted about being unemployed or job searching. The messages are personalized with the target’s name and feature friendly tone and solid grammar to build trust. They make vague allusions to exciting openings that seem like a perfect match.
Targets lured in by the initial outreach on Facebook and Instagram are soon instructed to continue the conversation via WhatsApp or Telegram. This allows the criminals to operate in the less regulated messaging environment.
On WhatsApp and Telegram, the fraudsters continue building rapport with targets through friendly small talk and flattery. Eventually they make their job offers for easy at-home work paying extremely generous hourly wages. Public-facing profiles on legitimate platforms grant these scammers an appearance of credibility that carries over into private conversations on messaging apps.
The Pec1966.com recruitment scam on social media follows the same playbook outlined earlier. The criminals artfully progress victims through messaging conversations to the point of ultimately directing them to Pec1966.com and its training program. This illustrates how social media provides fertile hunting grounds to initiate contact with targets who are then migrated to other platforms to carry out the scam.
Warning Signs To Spot the Pec1966.com Scam
While this scam can appear authentic at first, there are multiple red flags victims should watch out for:
- Unsolicited Contact – Being contacted out of the blue about an employment opportunity should raise suspicion, especially via unconventional channels like WhatsApp.
- Vague Details – The “job” offers lack specifics about roles, responsibilities, required skills, and application process. This is a major warning sign.
- Communication Only Via Apps – Interaction is limited to messaging apps and texting. No phone calls or video chats take place.
- Grammatical Errors – Messages often contain spelling, grammar, or formatting errors indicating possible foreign origins.
- Overly Generous Pay – The pay and benefits advertised are excessively high for easy remote positions requiring no specific skills or qualifications.
- Upfront Fees – Having to pay just to apply or train for a job is a tell-tale indicator of a money-making scam.
- Inability to Withdraw Funds – Excuses are always presented when attempting to withdraw earnings from the platform.
- High Pressure Tactics – Aggressive demands are used insisting victims purchase upgrades and invest more into the platform.
Any program soliciting unprompted participation paired with requests for upfront payments should be treated with extreme caution and skepticism.
Steps to Take if You Are Victimized by Pec1966.com
If you unfortunately fell prey to the Pec1966.com scam, here are the critical actions you should take immediately for damage control:
If you fear you have fallen prey to the Pec1966.com scam, here are some important steps to take right away:
1. Stop All Engagement
Immediately cease all communication with the scammers and disable any accounts created on their websites. Do not submit any additional fees on Pec1966.com or other related sites no matter what promises are made.
Continuing participation will only lead to more lost funds. You must break all contact to contain the damage.
2. Document Everything
Compile records of all transactions, messages, and material related to the scam. Save screenshots, photos, emails, receipts, bank statements, cryptocurrency wallet records, and anything else documenting your losses. Detailed documentation will assist recovery efforts.
3. Report it
File reports about the scam with relevant local and international authorities:
- Your country’s national cybercrime agency
- Local police
- Federal Trade Commission (if in U.S.)
- Action Fraud (if in U.K.)
- The cybercrime division of the platform scam originated on (WhatsApp, Telegram, etc)
Reporting exposes the criminals, helps authorities piece together connections between victims, and builds cases for prosecution.
4. Inform Your Bank
Notify your bank or payment providers (credit cards, PayPal, cryptocurrency exchanges, etc) about the fraud if their services were utilized. Providing documentation can help reverse unauthorized charges and prevent further misuse of your accounts.
5. Consult Recovery Experts
Retain professionals who assist victims in tracing and recovering lost funds from online crimes. Reputable ones work on a contingency basis, only collecting a percentage of recovered money. This can significantly increase the chances of getting some financial relief.
6. Seek Legal Representation
Consult an attorney experienced in cases of online fraud and theft. They can provide guidance on pursuing criminal charges and civil lawsuits against the perpetrators, or suing negligent institutions that enabled the scam. Legal action can sometimes increase pressure to return stolen funds.
7. Let Your Story Be Known
Report your experience on scam warning websites, consumer advocacy platforms, social networks, and in comments sections of websites promoting the scam. Increasing public exposure and warnings make it harder for the criminals to find new victims. Your story could prevent someone else from being defrauded.
Frequently Asked Questions About the Pec1966.com Scam
The Pec1966.com scam raises many questions for both its potential victims and concerned citizens. Here are answers to some of the most frequently asked questions about this unethical criminal scheme.
What is the Pec1966.com scam?
The Pec1966.com scam is an elaborate online scam that targets job seekers by tricking them into signing up for a fraudulent website called Pec1966.com. It promises easy work-from-home jobs paying lucrative hourly wages but is simply a front to steal money.
How does the Pec1966.com scam work?
The scam begins with victims receiving messages on apps like WhatsApp for fake job offers. If they show interest, they are directed to Pec1966.com and told to complete tasks to get “trained” for the job. They must then pay escalating upfront fees with the false promise of earning high wages. Ultimately, no payments are ever made.
What are some tactics used in the Pec1966.com scam?
Tactics include unsolicited personalized job offers, exaggerated wages for easy remote work, fake social media recruiter profiles, directing targets to Pec1966.com as a “training program”, slowly increasing fees described as “upgrades”, stalling on withdrawals using endless excuses.
What are some red flags of the Pec1966.com scam?
Red flags include unprompted job offers, vaguely detailed roles, communication only via messaging apps, poor grammar/spelling, wages/benefits too good to be true, required upfront payments, inability to withdraw earnings, and high pressure coercion.
Who is behind the Pec1966.com scam?
It is believed international organized crime rings operate these types of scams to target English speaking populations globally. The anonymous nature of the internet allows them to remain unidentified.
How much money has the Pec1966.com scam made?
Estimates indicate Pec1966.com and related sites have scammed victims out of over €100 million collectively thus far. Individual losses often reach tens or hundreds of thousands of dollars.
How can I avoid the Pec1966.com job scam?
Avoid it by being wary of unsolicited job offers, looking out for red flags, verifying legitimacy of employers, never paying upfront fees, and avoiding shady “training” programs.
The Bottom Line
Pec1966.com falsely portrays itself as a platform for earning online income through quick and easy tasks. But in reality, it is an intricately designed scam operation that carries out theft through deception, manipulation, and social engineering.
This fraudulent website cons countless victims by baiting them with promises of task earnings. After accruing balances, victims suddenly have funds deducted and must pay fees to restore earnings that never actually get reimbursed.
If you encounter Pec1966.com, cease all activity immediately. Document details of your experience in case evidence is needed for investigations. Report Pec1966.com to authorities and warn others of the scam by filing complaints online.
Unfortunately, the anonymous criminals behind these types of scams often never face justice. But by acting swiftly, spreading awareness, and contacting the proper authorities, victims can help limit financial damages and prevent others from falling prey.