An ongoing malware campaign is blasting the Internet with malware that neuters the security of Web browsers, adds malicious browser extensions, and makes other changes to users’ computers, Microsoft said on Thursday. Adrozek, as the software maker has dubbed the malware family, relies on a sprawling distribution network comprising 159 unique domains with each one hosting an average of 17,300 unique URLs. The URLs, in turn, host an average of 15,300 unique malware samples. The campaign began no later than May and hit a peak in August, when the malware was observed on 30,000 devices per day. The attack works against the Chrome, Firefox, Edge, and Yandex browsers, and it remains ongoing. The end goal for now is to inject ads into search results so the attackers can collect fees from affiliates. While these types of campaigns are common and represent less of a threat than many types of malware, Adrozek stands out because of malicious modifications it makes to security settings and other malicious actions it performs.
“Cybercriminals abusing affiliate programs is not new—browser modifiers are some of the oldest types of threats,” researchers from the Microsoft 365 Defender Research Team, wrote in a
blog post. “However, the fact that this campaign utilizes a piece of malware that affects multiple browsers is an indication of how this threat type continues to be increasingly sophisticated. In addition, the malware maintains persistence and exfiltrates website credentials, exposing affected devices to additional risks.”
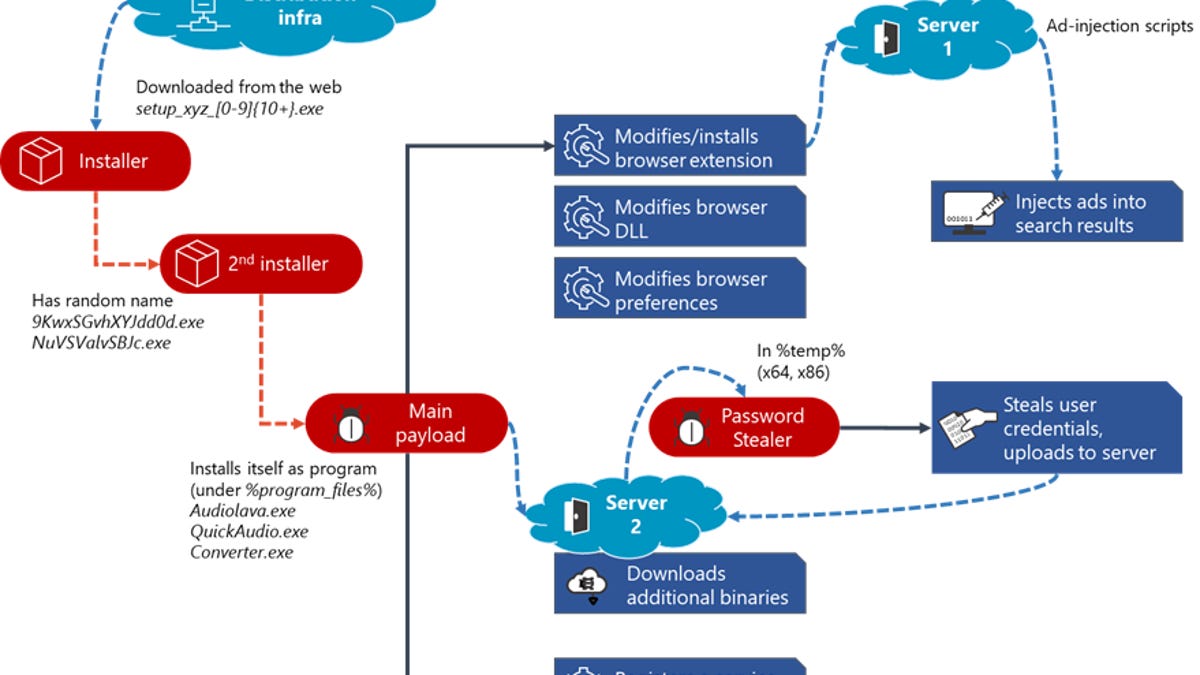
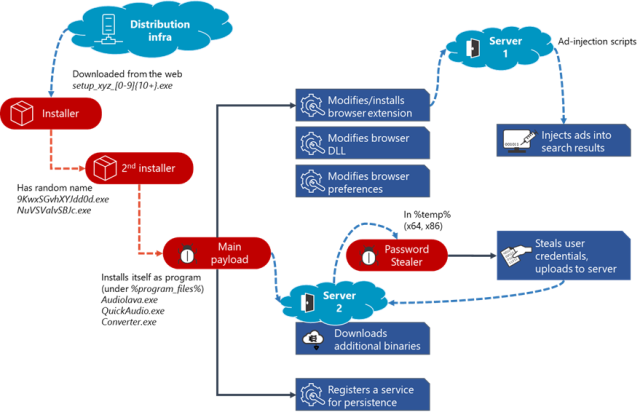
The post said that Adrozek is installed “through drive-by download.” Installer file names use the format of setup__.exe. They drop a file in the Windows temporary folder, and this file in turn drops the main payload in the program files directory. This payload uses a file name that makes the malware appear to be legitimate audio-related software, with names such as Audiolava.exe, QuickAudio.exe, and converter.exe. The malware is installed the way legitimate software is and can be accessed through the Settings>Apps & features and is registered as a Windows service with the same file name.
The graphic below shows the Adrezok attack chain:
Enlarge
Once installed, Adrozek makes several changes to the browser and the system it runs on. On Chrome, for instance, the malware often makes changes to the
Chrome Media Router service. The purpose is to install extensions that masquerade as legitimate ones by using IDs such as “Radioplayer.” The extensions connect to the attacker’s server to fetch additional code that injects ads into search results. The extensions also send the attackers information about the infected computer, and on Firefox, it also attempts to steal credentials. The malware goes on to tamper with certain DLL files. On Edge, for instance, the malware modifies MsEdge.dll so that it turns off security controls that help detect unauthorized changes to the Secure Preferences file. This technique, and similar ones for other affected browsers, has potentially serious consequences. Among other things, the Preferences File checks the integrity of values of various files and settings. By nullifying this check, Adrozek opens browsers up to other attacks. The malware also adds new permissions to the file.
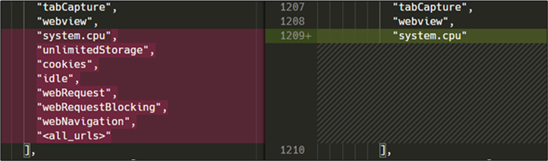
Below is a screenshot showing those added to Edge:
Microsoft
The malware then makes changes to the system settings to ensure it runs each time the browser is restarted or the computer is rebooted. From that point on, Adrozek will inject ads that either accompany ads served by a search engine or are placed on top of them.
Thursday’s post doesn’t explicitly say what, if any, user interaction is required for infections to occur. It’s also not clear what effect defenses like
User Account Control have. Microsoft makes no mention of the attack hitting browsers running macOS of Linux, so it's likely this campaign affects only Windows users. Microsoft representatives didn’t respond to an email asking for details.
The campaign uses a technique called polymorphism to blast out hundreds of thousands of unique samples. That makes signature-based antivirus protection ineffective. Many AV offerings—Microsoft Defender included—have behavior-based, machine-learning-powered detections that are more effective against such malware.