- Jan 6, 2017
- 835
It can be difficult to know which way to turn when it comes to online security. Learn about viruses, spyware and malware removal as we demystify digital threats.
Online security is a massive concern for organisations and individuals alike, and software which can prevent viruses, or help with malware removal, is highly sought-after. However, with so many different terms being discussed, it can be difficult to know where to turn.
It’s rare these days to go even a month without hearing about a high-level cyberattack. Whether it’s an attack on public services such as the WannaCry incident, which almost brought the UK’s NHS to its knees, or an assault on corporations such as Petya, or NotPetya, which compromised shipping company Maersk and vast amounts of data at Equifax and Deloitte, the threats are real, and no organization of any size should consider themselves exempt from being targeted.
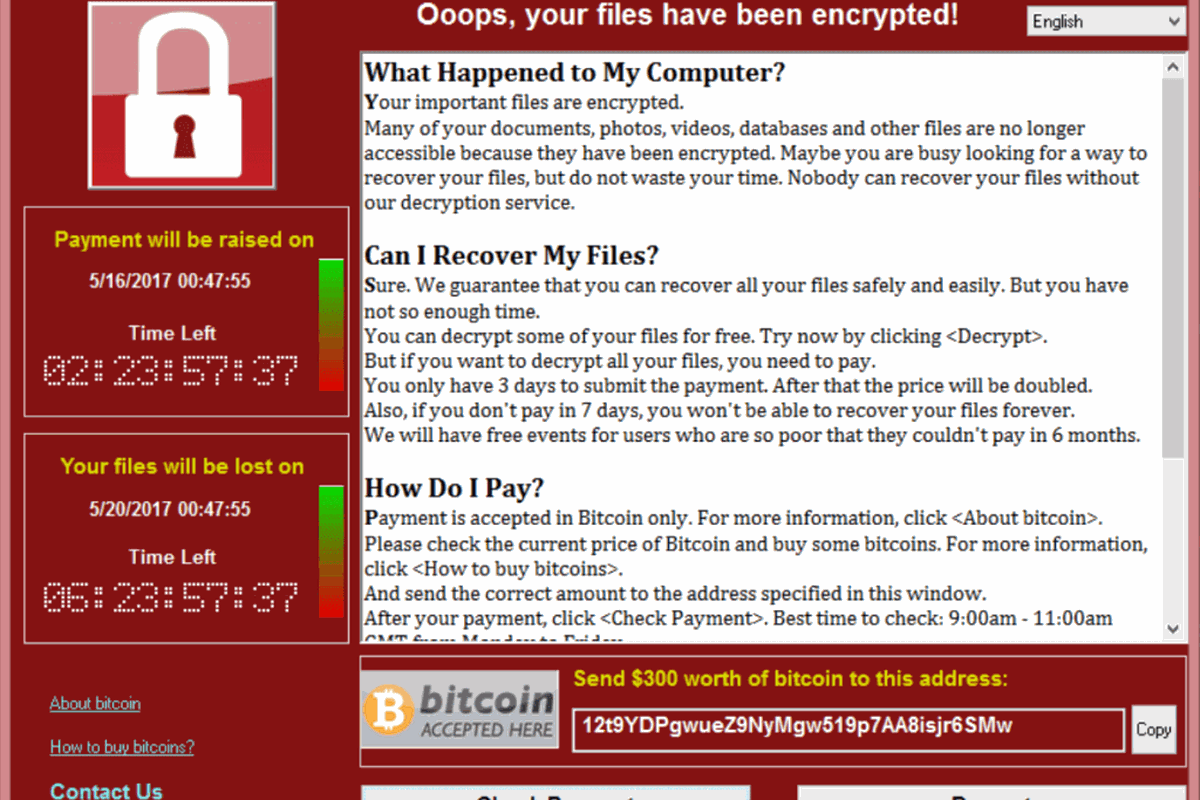
WannaCry ransomware attack hit organisations around the world.
Insurance and risk management experts estimate that, in 2017, cybercrime cost the global economy $450 billion, and the total is expected to hit $6 trillion by 2021. While most of these attacks are aimed at large organisations, many threats are also levelled at individuals. This means that it is essential for the modern internet user to have a good standard of education when it comes to the various types of threat to their own internet security. One size does not necessarily fit all when it comes to fighting these issues, so knowing the differences between them is key.
In our first beginners’ guide to online security, we will be looking at three different terms used to describe digital threats – malware, viruses and spyware – defining them, and looking at ways to help you avoid becoming compromised.
Malware
You’ve probably hear the term malware a lot, but are maybe not sure which specific threat the term refers to. Well, you may be surprised to learn that malware is not a specific type of threat, but rather a catchall term for all harmful and/or intrusive software. The word is a contraction of ‘malicious software’, and covers viruses, worms, ransomware, Trojan horses, spyware, and many other threats.
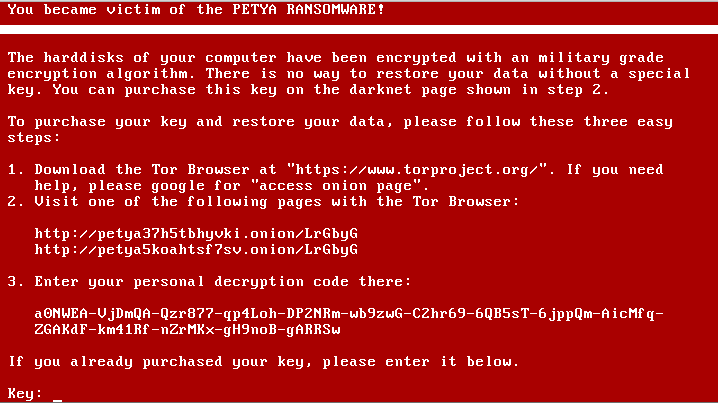
Petya spread rapidly through networks using Microsoft Windows.
So, when you are searching for malware removal software – such as Malwarebytes – you know that, if the application states it tackles malware, it will locate and eliminate a wide range of online threats.
Malware can also be an intentional element of otherwise legitimate software. For example, a few years ago, it was discovered that a piece of software released by Sony was secretly installing malware on their customers’ computers. The software was designed to fight piracy, but the type of software it was based on – and its ability to install itself secretly – carried with it inherent risks that can lead to the security of the target system being compromised. The scandal caused no small amount of trouble for Sony, and the software was recalled as a result.
Viruses
As its name suggests, a computer virus works much in the same way as its biological namesake. Once the malicious file is deployed, the virus’s code begins to rapidly replicate and replace the existing computer code.
But why would anyone want to infect your computer with a virus? Well, from blackmailing a victim into handing over money in exchange for removing the virus (ransomware), to political motives such as shutting down an opponents’ site or spreading false information – the motives for a virus attack are varied. Indeed, many viruses are developed by anonymous coders just for fun – they get a thrill from a successful attack. And some are even created out for apparently “noble” reasons, such as to highlight a flaw in a system’s security.
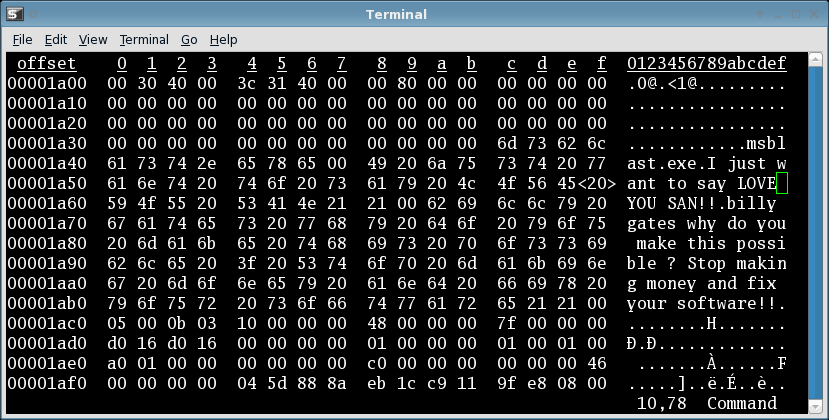
Blast(er) from the past: Blaster Worm virus spread on PCs running Windows XP and 2000, back in 2003.
The perpetrators of virus-based attacks will normally use social engineering to trick their victims into activating the malware. They might send an email, claiming to be from Microsoft Security or a similar body, saying that several viruses have been found on the target’s computer and they need to click a link or download a file to activate a malware removal program. However, once the target has clicked the link, the software is installed, and their computer is now truly infected. This is known as a phishing scam. Sometimes attackers will phone the target and attempt to deceive them into allowing access to their system.
The best advice we can give you is to never click a link in an email, and never believe anyone who calls you out of the blue. If they purport to be from a company you really do business with, then head to the company’s website manually and log in that way. However, if you have made a mistake and believe your computer to be infected, you’ll need to install some malware removal software to find and delete the virus.
If you no longer have control over your system, then you should contact an IT professional or the police for advice.
Spyware
Broadly speaking, spyware is any malware which secretly collects data on its target, or takes control over a computers’ functions. Once installed, the software is typically very hard to detect and can send data to a source where it can then be used to blackmail the target, or to damage their lives in some way – making explicit photographs public, for example.
Spyware can have a legitimate function, such as the code which allows Facebook and other companies to access your browsing habits so they can present you with targeted advertising. Most people accept this application as the price they must pay for free online services – but it’s important to be alert to any potential misuse of this power.
Many anti-spyware software packages have been developed to deal with these threats, and can help block your computer from any software – both legitimate and malicious – which aims to track your usage and/or data.
Final Thoughts
Understanding the varying nature of online threats is an important step towards effectively combatting them. Hopefully, in defining a few commonly-used terms, we have shed some light on the sorts of threats to look out for when using internet-connected devices. Remember that smartphones and tablets are also vulnerable to these threats, and need to be protected just as much as your home computer does.
Online security is a massive concern for organisations and individuals alike, and software which can prevent viruses, or help with malware removal, is highly sought-after. However, with so many different terms being discussed, it can be difficult to know where to turn.
It’s rare these days to go even a month without hearing about a high-level cyberattack. Whether it’s an attack on public services such as the WannaCry incident, which almost brought the UK’s NHS to its knees, or an assault on corporations such as Petya, or NotPetya, which compromised shipping company Maersk and vast amounts of data at Equifax and Deloitte, the threats are real, and no organization of any size should consider themselves exempt from being targeted.

WannaCry ransomware attack hit organisations around the world.
Insurance and risk management experts estimate that, in 2017, cybercrime cost the global economy $450 billion, and the total is expected to hit $6 trillion by 2021. While most of these attacks are aimed at large organisations, many threats are also levelled at individuals. This means that it is essential for the modern internet user to have a good standard of education when it comes to the various types of threat to their own internet security. One size does not necessarily fit all when it comes to fighting these issues, so knowing the differences between them is key.
In our first beginners’ guide to online security, we will be looking at three different terms used to describe digital threats – malware, viruses and spyware – defining them, and looking at ways to help you avoid becoming compromised.
Malware
You’ve probably hear the term malware a lot, but are maybe not sure which specific threat the term refers to. Well, you may be surprised to learn that malware is not a specific type of threat, but rather a catchall term for all harmful and/or intrusive software. The word is a contraction of ‘malicious software’, and covers viruses, worms, ransomware, Trojan horses, spyware, and many other threats.

Petya spread rapidly through networks using Microsoft Windows.
So, when you are searching for malware removal software – such as Malwarebytes – you know that, if the application states it tackles malware, it will locate and eliminate a wide range of online threats.
Malware can also be an intentional element of otherwise legitimate software. For example, a few years ago, it was discovered that a piece of software released by Sony was secretly installing malware on their customers’ computers. The software was designed to fight piracy, but the type of software it was based on – and its ability to install itself secretly – carried with it inherent risks that can lead to the security of the target system being compromised. The scandal caused no small amount of trouble for Sony, and the software was recalled as a result.
Viruses
As its name suggests, a computer virus works much in the same way as its biological namesake. Once the malicious file is deployed, the virus’s code begins to rapidly replicate and replace the existing computer code.
But why would anyone want to infect your computer with a virus? Well, from blackmailing a victim into handing over money in exchange for removing the virus (ransomware), to political motives such as shutting down an opponents’ site or spreading false information – the motives for a virus attack are varied. Indeed, many viruses are developed by anonymous coders just for fun – they get a thrill from a successful attack. And some are even created out for apparently “noble” reasons, such as to highlight a flaw in a system’s security.

Blast(er) from the past: Blaster Worm virus spread on PCs running Windows XP and 2000, back in 2003.
The perpetrators of virus-based attacks will normally use social engineering to trick their victims into activating the malware. They might send an email, claiming to be from Microsoft Security or a similar body, saying that several viruses have been found on the target’s computer and they need to click a link or download a file to activate a malware removal program. However, once the target has clicked the link, the software is installed, and their computer is now truly infected. This is known as a phishing scam. Sometimes attackers will phone the target and attempt to deceive them into allowing access to their system.
The best advice we can give you is to never click a link in an email, and never believe anyone who calls you out of the blue. If they purport to be from a company you really do business with, then head to the company’s website manually and log in that way. However, if you have made a mistake and believe your computer to be infected, you’ll need to install some malware removal software to find and delete the virus.
If you no longer have control over your system, then you should contact an IT professional or the police for advice.
Spyware
Broadly speaking, spyware is any malware which secretly collects data on its target, or takes control over a computers’ functions. Once installed, the software is typically very hard to detect and can send data to a source where it can then be used to blackmail the target, or to damage their lives in some way – making explicit photographs public, for example.
Spyware can have a legitimate function, such as the code which allows Facebook and other companies to access your browsing habits so they can present you with targeted advertising. Most people accept this application as the price they must pay for free online services – but it’s important to be alert to any potential misuse of this power.
Many anti-spyware software packages have been developed to deal with these threats, and can help block your computer from any software – both legitimate and malicious – which aims to track your usage and/or data.
Final Thoughts
Understanding the varying nature of online threats is an important step towards effectively combatting them. Hopefully, in defining a few commonly-used terms, we have shed some light on the sorts of threats to look out for when using internet-connected devices. Remember that smartphones and tablets are also vulnerable to these threats, and need to be protected just as much as your home computer does.
