- Dec 30, 2012
- 4,809
A report released today on the software products with the most security flaws in the past three months reveals that almost a quarter of all entries on the monthly Top 20 list were various types of security products.
The report, released by Flexera Software (formerly Secunia), is based on the Flexera Top 20, a list of software products for which security flaws came to light during a calendar month.
According to Flexera, the Top 20 list for the months of August, September, and October included 46 software products that totaled 2,162 vulnerabilities.
The company with the most vulnerable products during this three-month period was IBM, while the most vulnerable product was the Avant Browser.
11 of the 46 apps (23.91%) that found their way on the Top 20 list were security products, from vendors such as AlienVault, IBM, Juniper, McAfee, Palo Alto, and Splunk.
Most flaws were in third-party libraries, not the apps themselves
In most cases, the security flaws didn't affect the security app per se but was a security issue in one of the third-party components and libraries embedded in such products.
"This highlights how important it is that software producers understand the third-party components used in their products and the vulnerabilities associated with them," the Flexera report reads. "All producers – including those that develop security software – must act quickly to patch vulnerable components and inform customers, in order to avoid exposing them to the risk of exploitation of those vulnerabilities."
Companies such as Google (through Project Zero) and Cisco (through the Talos team) have been busy in the past few months exposing security flaws in security software and third-party libraries often used as the building blocks for these products, and others.
A report from market research company Forrester highlighted the same issue, that most of the time third-party components leave reliable applications exposed to dangerous security flaws.
Many browser flaws also discovered
The Flexera report also shows that second to security products are browsers and PDF readers, which both combined accounted for seven products of the total 46.
The list included browsers such as Apple Safari, Avant Browser, Cyberfox, Google Chrome, and Mozilla Firefox, and PDF readers such as Adobe Reader and Foxit Phantom PDF.
Because of the ubiquity of these products and the high number of security flaws, it is to no surprise why malware authors, exploit kits, and hackers often target these applications. Below are the Top 20 lists for the three aforementioned months.
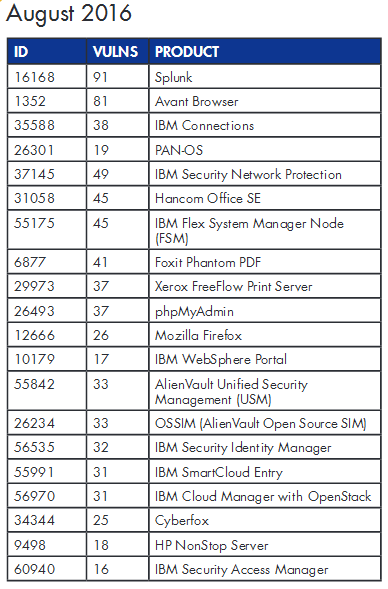
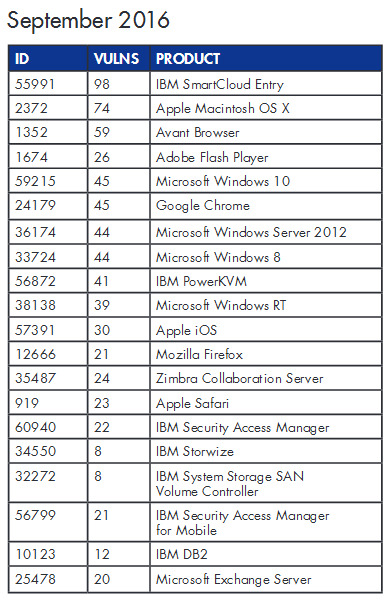
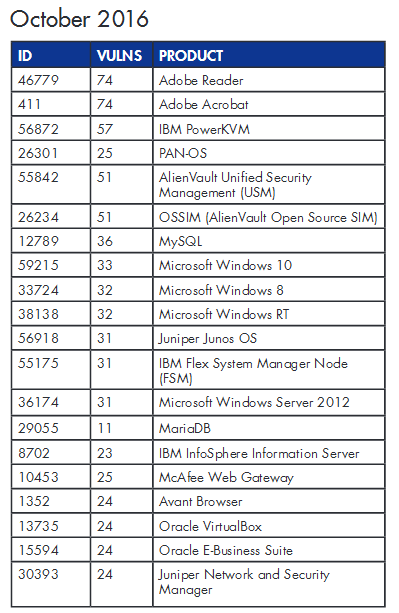
The report, released by Flexera Software (formerly Secunia), is based on the Flexera Top 20, a list of software products for which security flaws came to light during a calendar month.
According to Flexera, the Top 20 list for the months of August, September, and October included 46 software products that totaled 2,162 vulnerabilities.
The company with the most vulnerable products during this three-month period was IBM, while the most vulnerable product was the Avant Browser.
11 of the 46 apps (23.91%) that found their way on the Top 20 list were security products, from vendors such as AlienVault, IBM, Juniper, McAfee, Palo Alto, and Splunk.
Most flaws were in third-party libraries, not the apps themselves
In most cases, the security flaws didn't affect the security app per se but was a security issue in one of the third-party components and libraries embedded in such products.
"This highlights how important it is that software producers understand the third-party components used in their products and the vulnerabilities associated with them," the Flexera report reads. "All producers – including those that develop security software – must act quickly to patch vulnerable components and inform customers, in order to avoid exposing them to the risk of exploitation of those vulnerabilities."
Companies such as Google (through Project Zero) and Cisco (through the Talos team) have been busy in the past few months exposing security flaws in security software and third-party libraries often used as the building blocks for these products, and others.
A report from market research company Forrester highlighted the same issue, that most of the time third-party components leave reliable applications exposed to dangerous security flaws.
Many browser flaws also discovered
The Flexera report also shows that second to security products are browsers and PDF readers, which both combined accounted for seven products of the total 46.
The list included browsers such as Apple Safari, Avant Browser, Cyberfox, Google Chrome, and Mozilla Firefox, and PDF readers such as Adobe Reader and Foxit Phantom PDF.
Because of the ubiquity of these products and the high number of security flaws, it is to no surprise why malware authors, exploit kits, and hackers often target these applications. Below are the Top 20 lists for the three aforementioned months.



