silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,154
Malvertising Campaign Steals Traffic From 10,000 Hacked WordPress Sites and Exploits the Online Advertising Supply Chain
Malvertising is neither a new nor insignificant threat -- nor is there any easy solution to stop it. It is the abuse of the online advertising industry to deliver malware disguised as or hidden within seemingly innocuous advertisements.
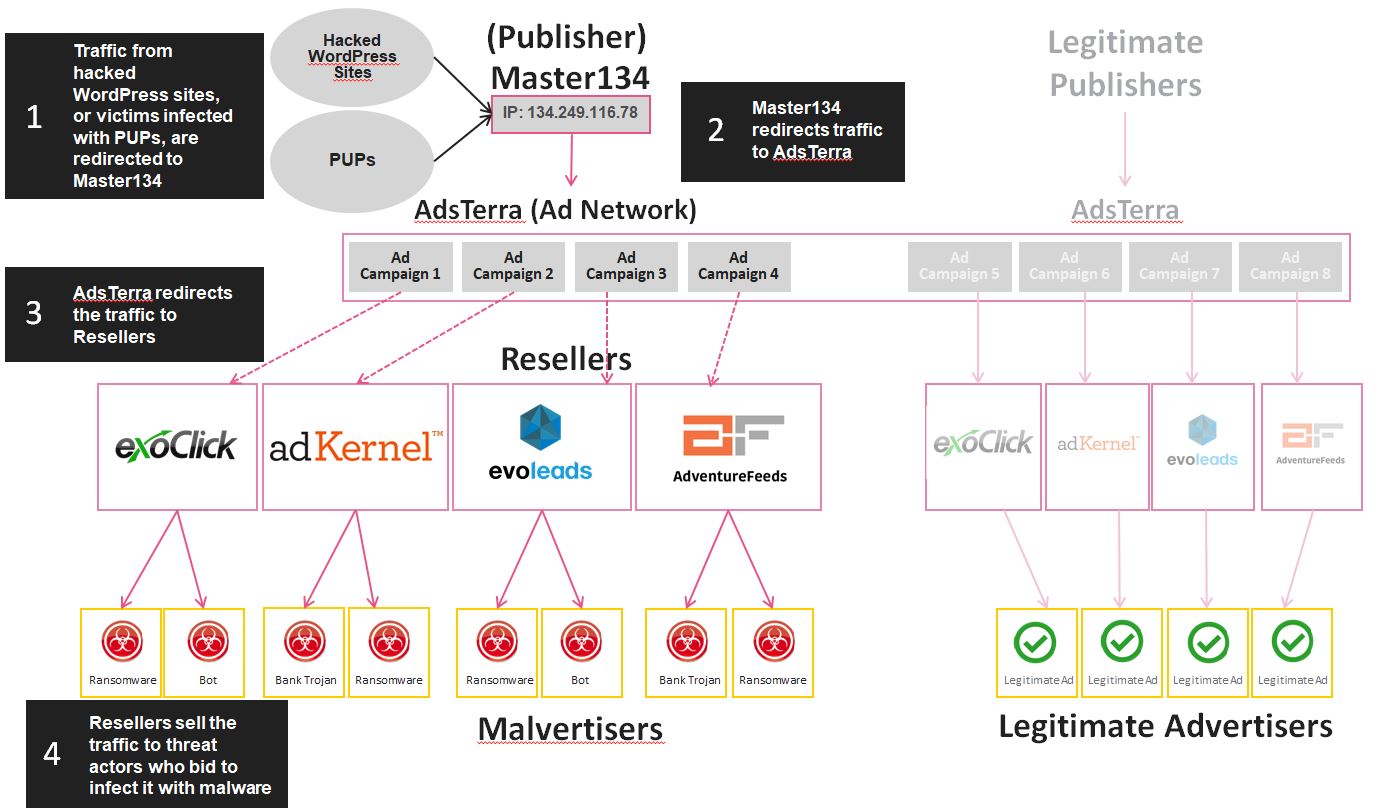
Researchers at Check Point have discovered what they describe as the infrastructure and methods used in a large ‘malvertising’ and banking Trojan campaign, which delivers malicious adverts to millions worldwide through the HiBids online advertising platform.
The campaign starts with a threat actor that Check Point describes as 'Master134'. He sold stolen web traffic from 10,000 hacked WordPress sites to, say the researchers, "AdsTerra, the real time bidding (RTB) ad platform, who then sold it to Resellers (ExoClick, AdKernel, EvoLeads and AdventureFeeds)."