- Nov 15, 2016
- 867
North Korea Keeps Hacking for Bitcoins, Researchers Say
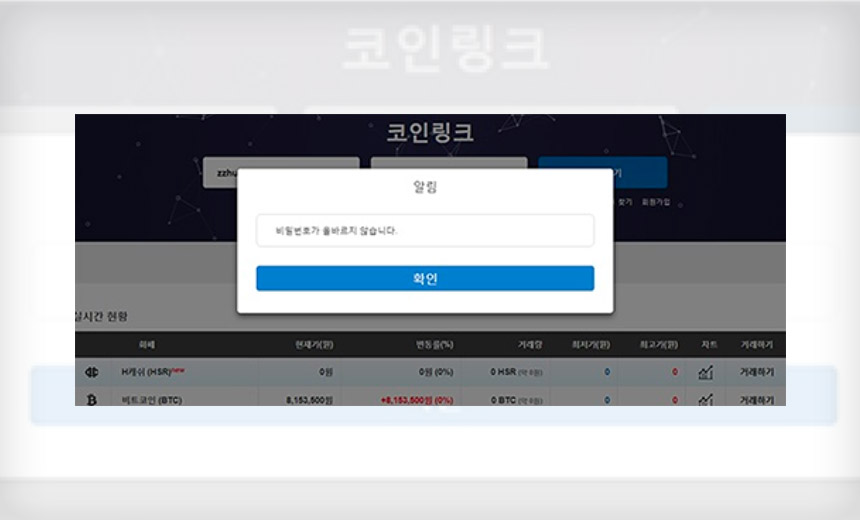
Phishing attack tries to trick recipients into entering their email and password for South Korean cryptocurrency exchange Coinlink. (Source: Recorded Future)
Virtual currency that's been surging in value, stored in internet-connected banks and virtual "hot wallets": What could go wrong?
See Also: Addressing the Identity Risk Factor in the Age of 'Need It Now'
The answer: About $175 million worth of stolen cryptocurrency and counting. And those are just the losses tied to three exchanges that have been hacked in the past year and quantified, at least in part, their losses (see Cybercriminals Go Cryptocurrency Crazy: 9 Factors).
The perils of attempting to keep cryptocurrency such as bitcoin and monero secure are demonstrated by South Korean exchange Youbit, which lost $35 million in cryptocurrencies last April before declaring bankruptcy last month after a second attack in which hackers stole 17 percent of its assets, which it has not yet quantified (see Report: Investigators Eye North Koreans for Exchange Hack).
Investigators continue to eye North Korea for this and many other cryptocurrency heists. Security experts say organized crime gangs tied to North Korea and others have been retooling from hacking banks to bitcoins as the value of the cryptocurrency has soared (see Cryptocurrency Infrastructure Flaws Pose Bitcoin Risks).
Meanwhile, investors continue to pour money into cryptocurrencies, including via initial coin offerings fielded by everyone from Kodak to the government of Venezuea.
While the value of a bitcoin traded below $1,000 before 2017, last year it hit a mid-December peak of $19,850. Cybercriminals who got in on the bitcoin-theft action before November 2017 and waited until December 2017 to cash out could have more than doubled their profits.
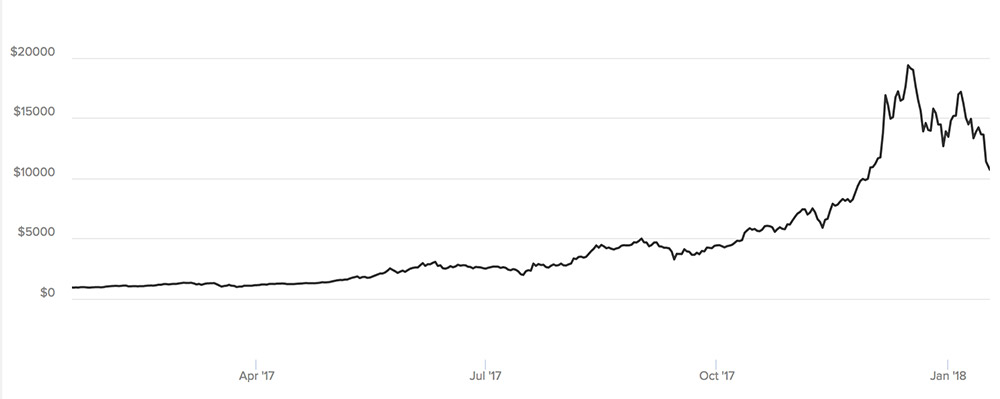
The U.S. dollar value of a bitcoin from Jan. 17, 2017, to Jan. 17, 2018. (Source: CoinDesk)
In recent days, however, bitcoin has been mostly trading above $10,000 after South Korea announced that it might regulate cryptocurrency. Other major cryptocurrencies, including ethereum and ripple, have also plunged in value.
North Korea Targets Cryptocurrency
Many attacks against cryptocurrency exchanges as well as cryptocurrency mining malware campaigns have been attributed to the cash-strapped, Pyongyang-based government of North Korea (see Report: North Korea Seeks Bitcoins to Bypass Sanctions).
Security researchers say a chief culprit is the North Korean-affiliated cybercrime gang known as Lazarus Group, which has existed since at least 2009 and which retooled in 2016 for bank heists, including the attempted theft of nearly $1 billion from the central bank of Bangladesh. That heist, committed by hacking into Bangladesh Bank's infrastructure and issuing fraudulent SWIFT money-moving messages, resulted in the theft of $81 million from the bank's account at the New York Federal Reserve (see Report: DOJ Sees Bangladesh Heist Tie to North Korea).
More recently, North Korea has been tied to numerous bitcoin heists. One recent campaign tied to Lazarus Group by some researchers targeted users of the Hangul Word Processor, a South Korean language word processing application in widespread use throughout South Korea, including by the government, threat intelligence firm Recorded Future says in a new report.
The malware dropper used in the campaign, it says, attempts to exploit a bypass and remote command execution flaw in Ghostscript, a software suite designed to interpret PostScript and Portable Document Format - PDF - file formats. The flaw, designated CVE-2017-8291, aka "Ghostbutt," was first targeted in the wild in April 2017. An exploit for the flaw is now available via the open source Metasploit penetration testing tool.
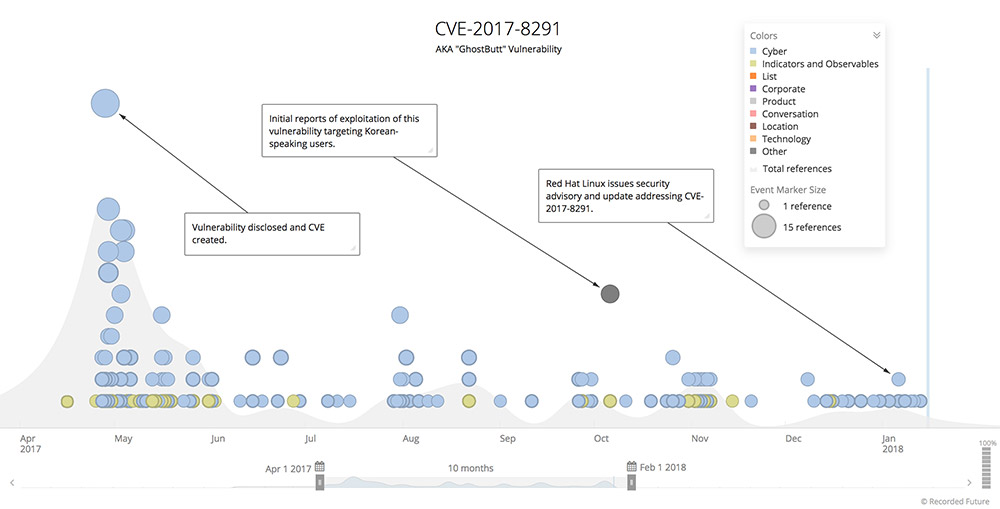
Timeline of CVE-2017-8291 (aka "GhostButt") exploitation. (Source: Recorded Future)
Recorded Future says the campaign used multiple lures:
Target: South Koreans
- Prompts that tell users their emails and passwords for the South Korean cryptocurrency exchange Coinlink are invalid;
- Attached resumes, which appear to be legitimate, from two South Korean scientists with cryptocurrency experience;
- A document about the Winter Olympics happening next month in South Korea.
The campaign targeted South Korean cryptocurrency exchanges and investors, as well as university students interested in foreign affairs, and it reused code from Destover malware, which was previously used against Sony Pictures Entertainment in 2014. It also reused an early version of WannaCry that predated the version seen in the May 2017 outbreak, Recorded Future says.
"The exploit implementation includes Chinese terms possibly signifying an attempted false flag or a Chinese exploit supplier," the firm adds, noting that Lazarus Group may have previously used false flag tactics (see WannaCry's Ransom Note: Great Chinese, Not-So-Hot Korean).
Phishing Email Subject Line: 'Bitcoin'
Describing the same attack campaign last year, Tokyo-based security firm Trend Micro said it used emails with subject lines such as "Bitcoin" and "Financial Security Standardization" and malicious attachments in PostScript format, which was originally designed for printing and desktop publishing.
Samples of decoy documents (Source: Trend Micro)
"PostScript does not have the ability to execute shell commands. However, it does have the capability to manipulate files," Trend Micro said. "This attack instead drops files into various startup folders, and waits for the user to reboot their machine." Such dropped files included executables in the startup folder that run a malicious JavaScript or dynamic-link library - DLL - file.
While the attack targets Hangul Word Processor users, Recorded Future notes that the Ghostscript vulnerability it exploits is widespread - existing, for example, in older versions of the widely used, open source ImageMagick image-editing software suite - and that the attack "could easily be adapted to other software."
Code Reuse Questions
Code reuse alone does not guarantee that the same individual or organization built a piece of malware. Indeed, many malware components can be bought or leased on cybercrime forums.
But Recorded Future sees signs that malware attributed to Lazarus Group is coming from a similar source. "Lazarus malware families - like Hangman, Duuzer, Volgmer, SpaSpe, etc. - overlap, likely as the result of the developers cutting-and-splicing an extensive codebase of malicious functionality to generate payloads as needed," it says. "This erratic composition make the Lazarus intrusion malware difficult to identify and group or cluster, unless they are analyzed at the level of code similarity."
Expect Lazarus to Branch Out
South Korea has been tightening its security following a series of attacks against the country's cryptocurrency exchanges. So expect attackers such as Lazarus Group to begin spending more time targeting other organizations in Asia, and beyond, Priscilla Moriuchi, director of strategic-threat development at Recorded Future and a former head of the National Security Agency's East Asia and Pacific cyber threats office, tells the Wall Street Journal.
"We see that as the trend in 2018," she says.