- Jan 25, 2018
- 300
Please helpme Hurryup! My license for HitmanPro.Alert will expire in the next days, I'm looking for another product who will can protect me with similar capabilities.
I don't want the protection of MBAE because it is lacking in several aspects, it doesn't allow to add a large list of applications that I want to protect, its interface is very limited.
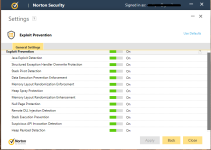
nor ZAL for the same reason because also it is outdated, instead of this two programs (mbae-zal), Ive solved the keylogger vulnerability with the protection of spyshelter in my system against keylogger rootkits and hooks, that is why in HMPA I only use the other remaining modules as you can see on this image.

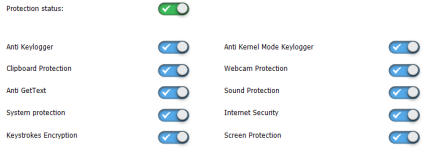
Spyshelter it's better than HMPA against hooks and Encryption keys on my experience, it also preventing the desktop screenshots and stealing text attack (copy-paste).
But Hitman it's better protecting through navigators remote attacks and against malicious exe-dll vulnerabilities comming from signed known companies that sometimes i download from free sources and promo giveaways suspict of cheater setup programmers. I'm looking to mix Eset, Nvtoa, Spyshelter and ???? Thank you.
I don't want the protection of MBAE because it is lacking in several aspects, it doesn't allow to add a large list of applications that I want to protect, its interface is very limited.
nor ZAL for the same reason because also it is outdated, instead of this two programs (mbae-zal), Ive solved the keylogger vulnerability with the protection of spyshelter in my system against keylogger rootkits and hooks, that is why in HMPA I only use the other remaining modules as you can see on this image.
Spyshelter it's better than HMPA against hooks and Encryption keys on my experience, it also preventing the desktop screenshots and stealing text attack (copy-paste).

But Hitman it's better protecting through navigators remote attacks and against malicious exe-dll vulnerabilities comming from signed known companies that sometimes i download from free sources and promo giveaways suspict of cheater setup programmers. I'm looking to mix Eset, Nvtoa, Spyshelter and ???? Thank you.