- Oct 23, 2012
- 12,527
Threat actors behind the malicious email campaigns delivering the Dridex banking Trojan seem to be focused on residents in Australia, the United Kingdom and the United States, in this particular order.
Dridex is considered the successor of Cridex, an infostealer that was distributed through spam campaigns leading to pages containing an exploit kit.
Multiple countries impacted by the malware
The malware aims at stealing online banking credentials and carries out its task via web injects in the pages of financial organizations targeted in the configuration file.
Researchers at Trend Micro have identified a recent email campaign that distributes the piece of malware through macros included in a Microsoft Word document. A macro is actually a script with commands designed to automate repetitive tasks.
The text file poses as an invoice or other type of financial document that would entice the unsuspecting user to open it. As soon as launched, if macros are enabled in the Office program, these start the process of compromising the computer with Dridex malware.
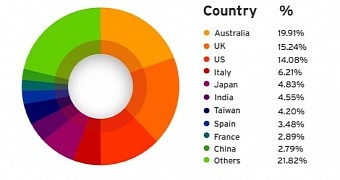
According to telemetry data from Trend Micro, most of the infected computers are located in Australia, accounting for 19.91% of the total number of compromised systems. Next comes the UK, with 15.24%, followed closely by the US with 14.08%. The information has been collected between September and October.
Other countries have also been affected, Italy, Spain, Japan, India, Taiwan, France and China being on the list too.
Mostly Europe-based banks are targeted
Roughly during the same period, Palo Alto Networks (PAN) also monitored a campaign spreading Dridex in the same way as this one. Their data revealed that the US had the largest number of infections, Australia and UK being on the list of the affected countries as well.
The similarities between the two campaigns are so striking (even the email with the malicious Word document is the same) that one could easily conclude that it is one and the same campaign.
As far as the origin of the malicious messages is concerned, Trend Micro provides a large list of countries, with Vietnam, India, Taiwan, Korea and China forming the top five.
After analyzing the threat, the researchers discovered that the configuration file marked financial institutions in Europe, which included Bank of Scotland, Lloyds Bank, Danske, Bank, Barclays, Kasikorn Bank, Santander, and Triodos Bank.
Microsoft recognizes the security risk posed by macro code and has it disabled by default in all Office components. Users are free to enable it and, when doing so, they are informed of the potential danger of the action.
However, if support for macros code is not turned on, cybercriminals may display a message informing the victim that the feature needs to be activated in order to see the content of the document.

Dridex is considered the successor of Cridex, an infostealer that was distributed through spam campaigns leading to pages containing an exploit kit.
Multiple countries impacted by the malware
The malware aims at stealing online banking credentials and carries out its task via web injects in the pages of financial organizations targeted in the configuration file.
Researchers at Trend Micro have identified a recent email campaign that distributes the piece of malware through macros included in a Microsoft Word document. A macro is actually a script with commands designed to automate repetitive tasks.
The text file poses as an invoice or other type of financial document that would entice the unsuspecting user to open it. As soon as launched, if macros are enabled in the Office program, these start the process of compromising the computer with Dridex malware.
According to telemetry data from Trend Micro, most of the infected computers are located in Australia, accounting for 19.91% of the total number of compromised systems. Next comes the UK, with 15.24%, followed closely by the US with 14.08%. The information has been collected between September and October.
Other countries have also been affected, Italy, Spain, Japan, India, Taiwan, France and China being on the list too.
Mostly Europe-based banks are targeted
Roughly during the same period, Palo Alto Networks (PAN) also monitored a campaign spreading Dridex in the same way as this one. Their data revealed that the US had the largest number of infections, Australia and UK being on the list of the affected countries as well.
The similarities between the two campaigns are so striking (even the email with the malicious Word document is the same) that one could easily conclude that it is one and the same campaign.
As far as the origin of the malicious messages is concerned, Trend Micro provides a large list of countries, with Vietnam, India, Taiwan, Korea and China forming the top five.
After analyzing the threat, the researchers discovered that the configuration file marked financial institutions in Europe, which included Bank of Scotland, Lloyds Bank, Danske, Bank, Barclays, Kasikorn Bank, Santander, and Triodos Bank.
Microsoft recognizes the security risk posed by macro code and has it disabled by default in all Office components. Users are free to enable it and, when doing so, they are informed of the potential danger of the action.
However, if support for macros code is not turned on, cybercriminals may display a message informing the victim that the feature needs to be activated in order to see the content of the document.
