- Feb 4, 2016
- 2,520
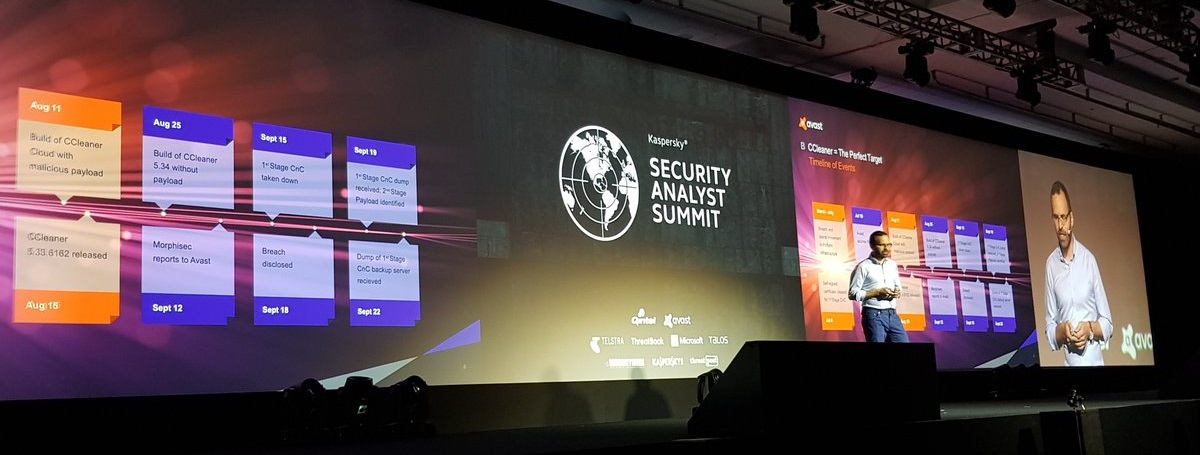
Avast has revealed new details about the 2017 CCleaner hack. Speaking at a conference in Mexico, the company's researchers said they uncovered new evidence to suggest that the hackers who breached CCleaner's infrastructure were preparing to deploy a third malware strain on infected computers.
The CCleaner incident came to light last September when security firms discovered that the 32-bit versions of CCleaner v5.33.6162 and CCleaner Cloud v1.07.3191 had been injected with an infostealer.
A summary of the CCleaner incident
Avast said that 2.27 million users had installed the tainted CCleaner versions, but that the malware collected only basic information, such as computer names and domain data.
The company later discovered that this first-stage infostealer was built as a mass-probing tool meant to identify computers on the internal networks of major tech and telecommunications companies, such as Google, Cisco, Oracle, Intel, Akamai, Microsoft, and many others.
Avast says that attackers deployed a second-stage payload to only 40 of these computers found on these highly sensitive networks.
Avast, Cisco Talos, and Kaspersky said that a (suspected Chinese) cyber-espionage group named Axiom was behind the hack of CCleaner's infrastructure.
Avast detects third malware strain
But yesterday, speaking at the SAS conference in Cancun, Mexico, Avast says it detected evidence of a third malware strain.
This new strain was found on four computers of Piriform employees, Piriform being the company behind the CCleaner app, which Avast bought in July 2017.
These infections went back to April 12, 2017, and Avast believes it was used to scout Piriform's network in preparation for the main hack that was to come over the summer.
Third malware strain is named ShadowPad
The name of this malware is ShadowPad —a multi-purpose and modular malware framework that comes with many plugins which provide various functionality, such as backdoor features, keylogging, and data exfiltration.
ShadowPad was first spotted by Kaspersky researchers in August 2017 on the servers of NetSarang, a South Korean software maker. According to Kaspersky, an unidentified cyber-espionage group injected ShadowPad in NetSarang's software and was using the malware as a backdoor into infected networks.
Avast says it found ShadowPad log files on the four infected Piriform computers. The log files contained encrypted keystrokes, meaning attackers deployed ShadowPad's keylogger plugin.
They also found ShadowPad plugins that could steal passwords from local apps, but also other tools that could download additional ShadowPad plugins.
