silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,172
Backdoor and Trojan malware variants are being distributed through a new phishing technique that attempts to lure victims into accepting an "update" to website security certificates.
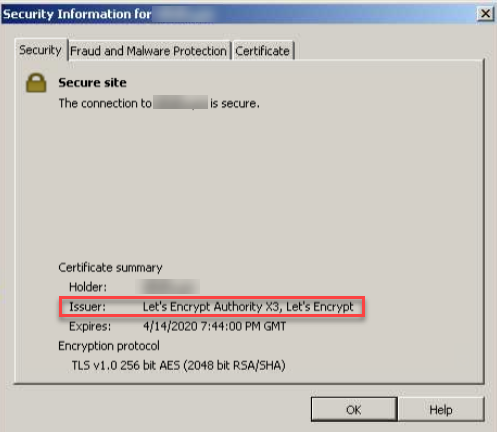
Certificate Authorities (CAs) distribute SSL/TLS security certificates for improved security online by providing encryption for communication channels between a browser and server -- especially important for domains providing e-commerce services -- as well as identity validation, which is intended to instill trust in a domain.
While there are cases of certificate misuse, fraud, and even cybercriminals posing as executives to obtain security certificates to sign off fraudulent domains or malware payloads, a new phishing approach is now abusing the certificate trust mechanism.
On Thursday, cybersecurity researchers from Kaspersky reported that the new technique has been spotted on a variety of websites, ranging from a zoo to an e-commerce store selling vehicle parts. The earliest infections date back to January 16, 2020.
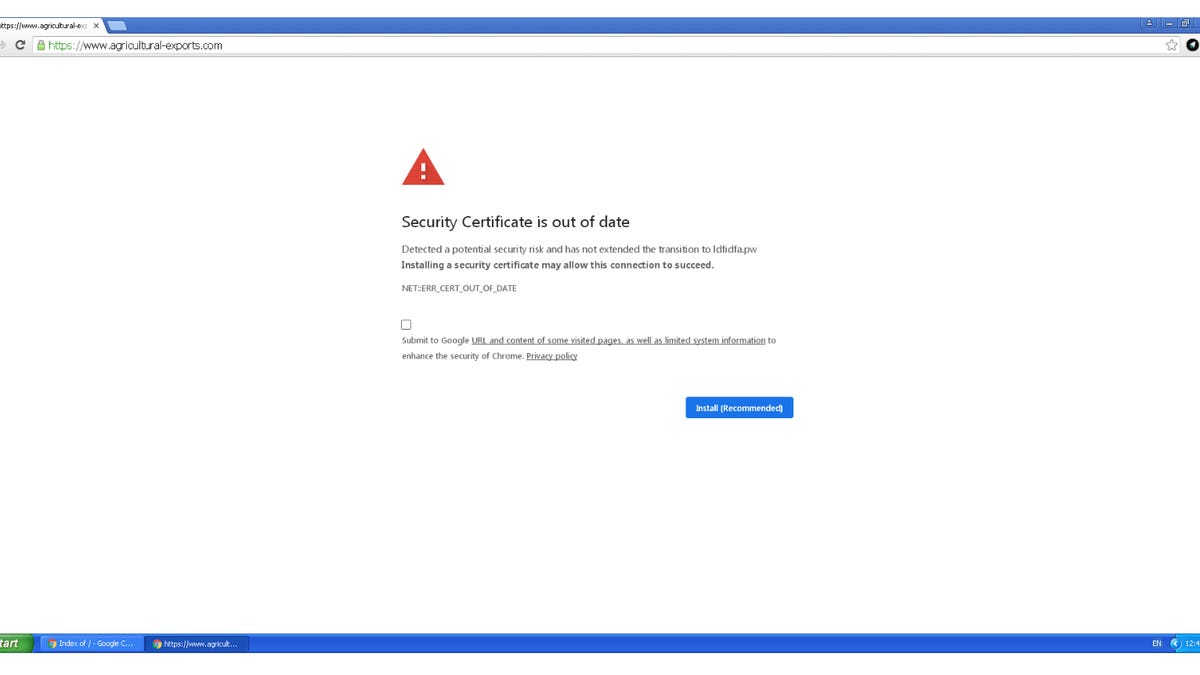
Backdoor malware is being spread through fake security certificate alerts
Victims of this new technique are invited to install a malicious "security certificate update" when they visit compromised websites.
 www.zdnet.com
www.zdnet.com