- May 16, 2013
- 844
- Content source
- https://threadreaderapp.com/thread/1307614248835731456.html
Today I was on a domain that should only be available via BasicAuth. Then I was really scared when I did not have to login. Even in incognito mode the page was visible without login. Is my BasicAuth broken? Turns out: No, but @Bitwarden has automatically logged in for me. 1/6
Bitwarden sends the HTTP Authorization Header automatically. The HTTP Authorization request header contains the credentials to authenticate a user with a server. This happens even if auto-fill is disabled. Not so tragic, one might think. But it's getting worse. 2/6
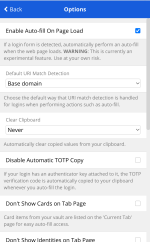
#Bitwarden use "Base domain" as a default URI match detection (bitwarden.com/help/article/u…). That means: bad\.example\.com is the same as good\.example\.com. So, Bitwarden might automatically (!!) leaks my passwords to other subdomains. 3/6
In my case this is not so problematic, because all subdomains belong to me. Nevertheless, Bitwarden still leaks my password to other subdomains and thus possibly to other servers. I think this is a serious attack vector. 4/6
This should not happen, especially not when auto-fill is switched off. The problem has been known since January, so out-of-scope for there bug bounty. Feel free to upvote this Issue on GitHub: github.com/bitwarden/brow… 5/6
Nevertheless I am convinced that Bitwarden belongs to the better password managers. Bitwarden is #OpenSource and can be completely self-hosting. 6/6
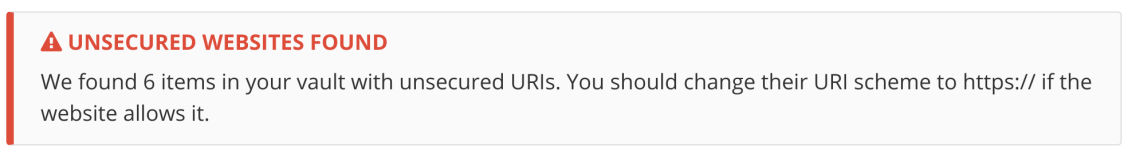
Addendum: Bitwarden also leaks my password to subdomains that do not have HTTPS. 7/6
Bitwarden sends the HTTP Authorization Header automatically. The HTTP Authorization request header contains the credentials to authenticate a user with a server. This happens even if auto-fill is disabled. Not so tragic, one might think. But it's getting worse. 2/6

#Bitwarden use "Base domain" as a default URI match detection (bitwarden.com/help/article/u…). That means: bad\.example\.com is the same as good\.example\.com. So, Bitwarden might automatically (!!) leaks my passwords to other subdomains. 3/6
In my case this is not so problematic, because all subdomains belong to me. Nevertheless, Bitwarden still leaks my password to other subdomains and thus possibly to other servers. I think this is a serious attack vector. 4/6
This should not happen, especially not when auto-fill is switched off. The problem has been known since January, so out-of-scope for there bug bounty. Feel free to upvote this Issue on GitHub: github.com/bitwarden/brow… 5/6
Nevertheless I am convinced that Bitwarden belongs to the better password managers. Bitwarden is #OpenSource and can be completely self-hosting. 6/6
Addendum: Bitwarden also leaks my password to subdomains that do not have HTTPS. 7/6