silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,154
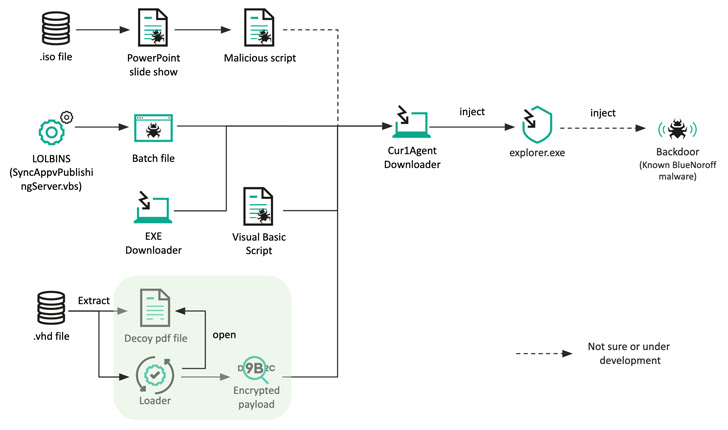
BlueNoroff, a subcluster of the notorious Lazarus Group, has been observed adopting new techniques into its playbook that enable it to bypass Windows Mark of the Web (MotW) protections.
This includes the use of optical disk image (.ISO extension) and virtual hard disk (.VHD extension) file formats as part of a novel infection chain, Kaspersky disclosed in a report published today.
"BlueNoroff created numerous fake domains impersonating venture capital companies and banks," security researcher Seongsu Park said, adding the new attack procedure was flagged in its telemetry in September 2022.
Some of the bogus domains have been found to imitate ABF Capital, Angel Bridge, ANOBAKA, Bank of America, and Mitsubishi UFJ Financial Group, most of which are located in Japan, signalling a "keen interest" in the region.

BlueNoroff APT Hackers Using New Ways to Bypass Windows MotW Protection
BlueNoroff APT hackers are using new techniques to bypass Windows' Mark of the Web protections, including the use of .ISO and .VHD file formats