- Nov 15, 2016
- 867
Chinese Cybersecurity Workers Hacked Firms, US Charges
Hackers Allegedly Stole Data From Siemens, Trimble and Moody's Analytics
Three men who work for a Chinese cybersecurity firm have been charged by the U.S. Department of Justice with hacking into the networks of Siemens, Moody's Analytics and Trimble and stealing valuable business secrets.
See Also: IoT is Happening Now: Are You Prepared?
The alleged hacking campaigns, which relied on spear-phishing emails and malware, ran from 2011 through May, according to a federal indictment dated Sept. 13 and unsealed Monday in U.S. federal court in Pittsburgh.
The indictment charges Wu Yingzhuo, Dong Hao and Xia Lei - all of Guangzhou, China - with conspiracy to commit computer fraud and abuse, conspiring to commit trade secret theft, wire fraud and aggravated identity theft.
While arrest warrants have been issued for all the suspects, none are in custody. "The Justice Department is committed to pursuing the arrest and prosecution of these hackers, no matter how long it takes, and we have a long memory," says Dana J. Boente, the acting assistant attorney general for national security.
All three men have been charged as individuals rather than state-sponsored hackers, Reuters reports.
The U.S. Department of Justice didn't immediately respond to a request for comment about whether it has filed an extradition request for the suspects with China. But a Justice Department spokesman told Cyberscoop News that it reached out to the Chinese government during the Oct. 3 Law Enforcement and Cybersecurity Dialogue in Washington, seeking assistance, but "received no meaningful response."
A Chinese government spokesman didn't immediately respond to a request for comment.
Investigation Led by FBI, NCIS, Air Force
The investigation that led to the charges being filed was conducted by the FBI, the Naval Criminal Investigative Service and the Air Force's Office of Special Investigations.
This indictment aside, cybersecurity relations between the U.S. and China have arguably improved in recent years following a peak in tensions in 2014. In May of that year, U.S. prosecutors indicted five members of the People's Liberation Army on charges related to the theft of intellectual property from U.S. companies (see The Real Aim of U.S. Indictment of Chinese).
In December 2015, however, China and the United States signed an agreement to work more closely together on cyber issues, including addressing intellectual property theft (see U.S.-China Cybersecurity Agreement: What's Next?).
Victims Hit With Spear-Phishing Attacks
The three men named in the indictment work for Bo Yu Information Technology Company Ltd., or Boysec for short, based in Guangzhou in the southeast of China.
The indictment says that Wu (aka "mxmtmw," "Christ Wu," "wyz") and Dong (aka "Bu Yi," "Dong Shi Ye," "Tianyu") are founders and equity shareholders of Boysec, while Xie (aka "Sui Feng Yan Mie") is an employee.
The company's website is currently offline.
The men have been charged with exploiting software vulnerabilities and using malware to steal confidential business information as well as intentionally damage computer systems.
Gothic Panda
Security researchers say Boyusec is also known as APT 3 and Gothic Panda.
The cyber intelligence firm Recorded Future in May concluded that APT3 was working with China's intelligence agency, known as the Ministry of State Security. The group's victims appear to have aligned with industries highlighted in the most recent Five Year Plan - the Chinese government's directive for how the country should focus its efforts - "including green/alternative energy, defense-related science and technology, biomedical and aerospace," Recorded Future says.
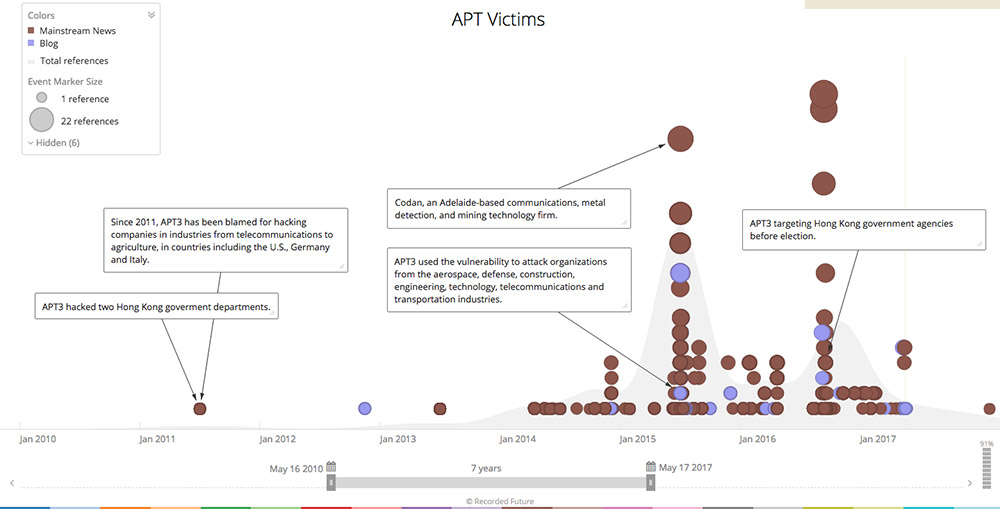
Record of some APT 3 victims. (Source: Recorded Future)
APT 3 has been active since 2007, according to Adam Meyers, a researcher with cybersecurity firm CrowdStrike. Meyers tells the Wall Street Journal that following the 2015 U.S.-China cybersecurity agreement, the Chinese government may have been forced to outsource more of its cyber espionage operations to third-party firms such as Boyusec.
Siemens Hacked
Investigators have accused the three alleged Boysec employees named in the indictment of using networks of proxy computers to mask their real IP addresses. Many of the spear-phishing emails the attackers allegedly used were designed to socially engineer - trick - specific recipients into opening malicious attachments or visiting links that led to sites hosting malware. If the attack was successful, attackers would gain long-term, backdoor access to victims' PC, according to the indictment.
Prosecutors allege that the men used these techniques to gain access to the network of German technology giant Siemens in May and June 2014. Dong allegedly used a backdoor to exfiltrate password hashes from the company's systems, and about a year later, attackers stole 470 gigabytes of data related to Siemens' energy, technology and transportation businesses.
A Siemens spokeswoman says that while the company does not comment on internal security matters, "information security is of the highest priority for Siemens worldwide. We rigorously monitor and protect our infrastructure and continually detect and hunt for breaches.
Trimble: No Client Data Breached
Between December 2015 and March 2016, the three Chinese nationals also allegedly targeted Trimble, a Sunnyvale, California-based company that develops GPS software and global navigation satellite systems.
Trimble spent millions of dollars over three years developing a GNSS product that uses a low-cost antenna to improve location data for tablets and mobile phones, the indictment says.
Wu is accused of exfiltrating a 252-megabyte zip file that contained technical, design and marketing documents related to the GNSS project. All told, the men allegedly took 275 megabytes of data that would have aided a Trimble competitor in creating a competing product.
Trimble says the unsealing of the indictment is "the culmination of an aggressive investigation by law enforcement." It says no client data was breached.
"Trimble responded to the incident and concluded that there is no meaningful impact on its business," the company says in a statement. "Trimble and its employees consistently maintain high standards in protecting its worldwide cyber assets."
Influential Moody's Economist Targeted
Officials with Moody's Analytics, which specializes in evaluating risk, didn't immediately respond to a request for comment about the indictment.
But the indictment charges Xia with accessing Moody's email server in August 2011 and creating a rule that forwarded all emails for an influential economist employed by the firm to another, fraudulent email account. The economist was "a public figure in the industry and was viewed by Moody's Analytics as a branding asset," the indictment says.
At least one of the men named in the indictment was allegedly keeping tabs on this economist's efforts. "In 2013 and 2014, defendant Xia regularly accessed those web-based email accounts to access the employee's stolen emails, which contained proprietary and confidential economic analyses, findings and opinions," the indictment says.
APT 3 Out of Commission?
Security researchers say attacks attributed to Boyusec have been seen at least through September.
Christopher Glyer, chief security architect at cybersecurity firm FireEye, says that unlike some APT attackers who focus on attack quantity and simply being "good enough," APT 3 differentiated itself by the quality of the attacks it launched. As a result, however, APT 3 wasn't able to launch as many attacks as some other hacking groups.
APT3 observation. They were likely a small group of elite operators. Although we saw them targets dozens of orgs at once. After moving off initial backdoors (often memory only) - they might go dormant for weeks/months and work their way serially through a prioritized victim list
— Christopher Glyer (@cglyer) November 28, 2017
In the wake of the indictment, it's not clear if APT 3 remains in operation.
Hackers Allegedly Stole Data From Siemens, Trimble and Moody's Analytics

Three men who work for a Chinese cybersecurity firm have been charged by the U.S. Department of Justice with hacking into the networks of Siemens, Moody's Analytics and Trimble and stealing valuable business secrets.
See Also: IoT is Happening Now: Are You Prepared?
The alleged hacking campaigns, which relied on spear-phishing emails and malware, ran from 2011 through May, according to a federal indictment dated Sept. 13 and unsealed Monday in U.S. federal court in Pittsburgh.
The indictment charges Wu Yingzhuo, Dong Hao and Xia Lei - all of Guangzhou, China - with conspiracy to commit computer fraud and abuse, conspiring to commit trade secret theft, wire fraud and aggravated identity theft.
While arrest warrants have been issued for all the suspects, none are in custody. "The Justice Department is committed to pursuing the arrest and prosecution of these hackers, no matter how long it takes, and we have a long memory," says Dana J. Boente, the acting assistant attorney general for national security.
All three men have been charged as individuals rather than state-sponsored hackers, Reuters reports.
The U.S. Department of Justice didn't immediately respond to a request for comment about whether it has filed an extradition request for the suspects with China. But a Justice Department spokesman told Cyberscoop News that it reached out to the Chinese government during the Oct. 3 Law Enforcement and Cybersecurity Dialogue in Washington, seeking assistance, but "received no meaningful response."
A Chinese government spokesman didn't immediately respond to a request for comment.
Investigation Led by FBI, NCIS, Air Force
The investigation that led to the charges being filed was conducted by the FBI, the Naval Criminal Investigative Service and the Air Force's Office of Special Investigations.
This indictment aside, cybersecurity relations between the U.S. and China have arguably improved in recent years following a peak in tensions in 2014. In May of that year, U.S. prosecutors indicted five members of the People's Liberation Army on charges related to the theft of intellectual property from U.S. companies (see The Real Aim of U.S. Indictment of Chinese).
In December 2015, however, China and the United States signed an agreement to work more closely together on cyber issues, including addressing intellectual property theft (see U.S.-China Cybersecurity Agreement: What's Next?).
Victims Hit With Spear-Phishing Attacks
The three men named in the indictment work for Bo Yu Information Technology Company Ltd., or Boysec for short, based in Guangzhou in the southeast of China.
The indictment says that Wu (aka "mxmtmw," "Christ Wu," "wyz") and Dong (aka "Bu Yi," "Dong Shi Ye," "Tianyu") are founders and equity shareholders of Boysec, while Xie (aka "Sui Feng Yan Mie") is an employee.
The company's website is currently offline.
The men have been charged with exploiting software vulnerabilities and using malware to steal confidential business information as well as intentionally damage computer systems.
Gothic Panda
Security researchers say Boyusec is also known as APT 3 and Gothic Panda.
The cyber intelligence firm Recorded Future in May concluded that APT3 was working with China's intelligence agency, known as the Ministry of State Security. The group's victims appear to have aligned with industries highlighted in the most recent Five Year Plan - the Chinese government's directive for how the country should focus its efforts - "including green/alternative energy, defense-related science and technology, biomedical and aerospace," Recorded Future says.

Record of some APT 3 victims. (Source: Recorded Future)
APT 3 has been active since 2007, according to Adam Meyers, a researcher with cybersecurity firm CrowdStrike. Meyers tells the Wall Street Journal that following the 2015 U.S.-China cybersecurity agreement, the Chinese government may have been forced to outsource more of its cyber espionage operations to third-party firms such as Boyusec.
Siemens Hacked
Investigators have accused the three alleged Boysec employees named in the indictment of using networks of proxy computers to mask their real IP addresses. Many of the spear-phishing emails the attackers allegedly used were designed to socially engineer - trick - specific recipients into opening malicious attachments or visiting links that led to sites hosting malware. If the attack was successful, attackers would gain long-term, backdoor access to victims' PC, according to the indictment.
Prosecutors allege that the men used these techniques to gain access to the network of German technology giant Siemens in May and June 2014. Dong allegedly used a backdoor to exfiltrate password hashes from the company's systems, and about a year later, attackers stole 470 gigabytes of data related to Siemens' energy, technology and transportation businesses.
A Siemens spokeswoman says that while the company does not comment on internal security matters, "information security is of the highest priority for Siemens worldwide. We rigorously monitor and protect our infrastructure and continually detect and hunt for breaches.
Trimble: No Client Data Breached
Between December 2015 and March 2016, the three Chinese nationals also allegedly targeted Trimble, a Sunnyvale, California-based company that develops GPS software and global navigation satellite systems.
Trimble spent millions of dollars over three years developing a GNSS product that uses a low-cost antenna to improve location data for tablets and mobile phones, the indictment says.
Wu is accused of exfiltrating a 252-megabyte zip file that contained technical, design and marketing documents related to the GNSS project. All told, the men allegedly took 275 megabytes of data that would have aided a Trimble competitor in creating a competing product.
Trimble says the unsealing of the indictment is "the culmination of an aggressive investigation by law enforcement." It says no client data was breached.
"Trimble responded to the incident and concluded that there is no meaningful impact on its business," the company says in a statement. "Trimble and its employees consistently maintain high standards in protecting its worldwide cyber assets."
Influential Moody's Economist Targeted
Officials with Moody's Analytics, which specializes in evaluating risk, didn't immediately respond to a request for comment about the indictment.
But the indictment charges Xia with accessing Moody's email server in August 2011 and creating a rule that forwarded all emails for an influential economist employed by the firm to another, fraudulent email account. The economist was "a public figure in the industry and was viewed by Moody's Analytics as a branding asset," the indictment says.
At least one of the men named in the indictment was allegedly keeping tabs on this economist's efforts. "In 2013 and 2014, defendant Xia regularly accessed those web-based email accounts to access the employee's stolen emails, which contained proprietary and confidential economic analyses, findings and opinions," the indictment says.
APT 3 Out of Commission?
Security researchers say attacks attributed to Boyusec have been seen at least through September.
Christopher Glyer, chief security architect at cybersecurity firm FireEye, says that unlike some APT attackers who focus on attack quantity and simply being "good enough," APT 3 differentiated itself by the quality of the attacks it launched. As a result, however, APT 3 wasn't able to launch as many attacks as some other hacking groups.
APT3 observation. They were likely a small group of elite operators. Although we saw them targets dozens of orgs at once. After moving off initial backdoors (often memory only) - they might go dormant for weeks/months and work their way serially through a prioritized victim list
— Christopher Glyer (@cglyer) November 28, 2017
In the wake of the indictment, it's not clear if APT 3 remains in operation.