- Jul 22, 2014
- 2,525
Some smart crooks found a way to insert and deliver the Coinhive in-browser miner inside ads delivered via the Google DoubleClick ad delivery platform.
Ads delivered this way made their way on countless sites, and even on Google's own property —YouTube.
A Trend Micro report released today claims the crooks behind this campaign started abusing Google's DoubleClick platform to deliver the Coinhive in-browser miner around January 18 and significantly ramped up operations on January 23.
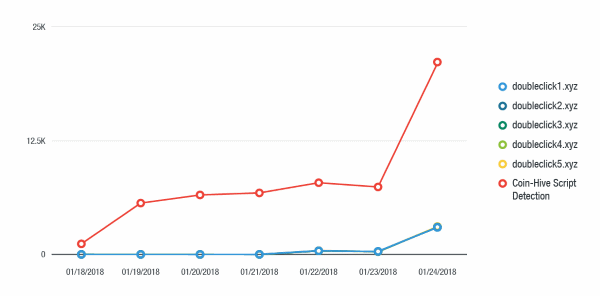
The chart above shows Coinhive detections for this malvertising campaign abusing Google DoubleClick.
Crooks deployed Coinhive on YouTube on January 23
The huge spike represents the moment when crooks decided to deliver the Coinhive-tainted ads on YouTube, the world's largest video hosting platform.
Reports immediately started appearing on Twitter [1, 2, 3, 4, 5, 6, 7, 8]. According to some of these reports, various antivirus products began detecting the Coinhive cryptojacker when users were visiting YouTube, a place where Coinhive would have never been able to load except via malicious JavaScript code hidden in one of the numerous ads displayed on video pages.
...
Ads delivered this way made their way on countless sites, and even on Google's own property —YouTube.
A Trend Micro report released today claims the crooks behind this campaign started abusing Google's DoubleClick platform to deliver the Coinhive in-browser miner around January 18 and significantly ramped up operations on January 23.

The chart above shows Coinhive detections for this malvertising campaign abusing Google DoubleClick.
Crooks deployed Coinhive on YouTube on January 23
The huge spike represents the moment when crooks decided to deliver the Coinhive-tainted ads on YouTube, the world's largest video hosting platform.
Reports immediately started appearing on Twitter [1, 2, 3, 4, 5, 6, 7, 8]. According to some of these reports, various antivirus products began detecting the Coinhive cryptojacker when users were visiting YouTube, a place where Coinhive would have never been able to load except via malicious JavaScript code hidden in one of the numerous ads displayed on video pages.
...
