- Sep 22, 2014
- 1,767
CTB-Locker, otherwise known as Critroni, is a Windows ransomware that saw wide distribution in the summer of 2014 and slowly decreased in distribution. This is a big month for CTB Locker as they have reinvented themselves by releasing a new variant that I have dubbed "CTB-Locker for Websites" that only targets and encrypts websites. Furthermore, this month CTB-Locker for Windows has also seen an increased distribution, but is still not nearly as active as other ransomware infections such as [URL='http://www.bleepingcomputer.com/virus-removal/teslacrypt-alphacrypt-ransomware-information']TeslaCrypt, CryptoWall, and Locky.
This article will primarily focus on the new website version, but will also cover a new change to the Windows variant. For victim's who requires help with CTB-Locker for Websites you can visit our support topic here: CTB-Locker for Websites Support and Help Topic.
For those who wish to analyze the source code for CTB-Locker for Websites, it was discovered by security researcher Benkow wokned and uploaded to Kernelmode. Feel free to let me know if I made any mistakes in this analysis.
CTB-Locker for Websites
CTB-Locker for Websites is a ransomware that is designed specifically to target websites, encrypt their contents, and then demand a .4 bitcoin ransom to get the decryption key. Websites become infected by the ransomware developers hacking the site and replacing the original index.php or index.html with a new index.php. This new index.php will then be used to encrypt the site's data using AES-256 encryption and to display a new home page that contains information on what has happened to the files and how to make a ransom payment.
This ransom note will state:
Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site.
The CTB-Locker web page also offers the ability to decrypt two prechosen files for free and to send and receive messages with the developer. You can see an example of what a website encrypted by CTB-Locker for Websites looks like.
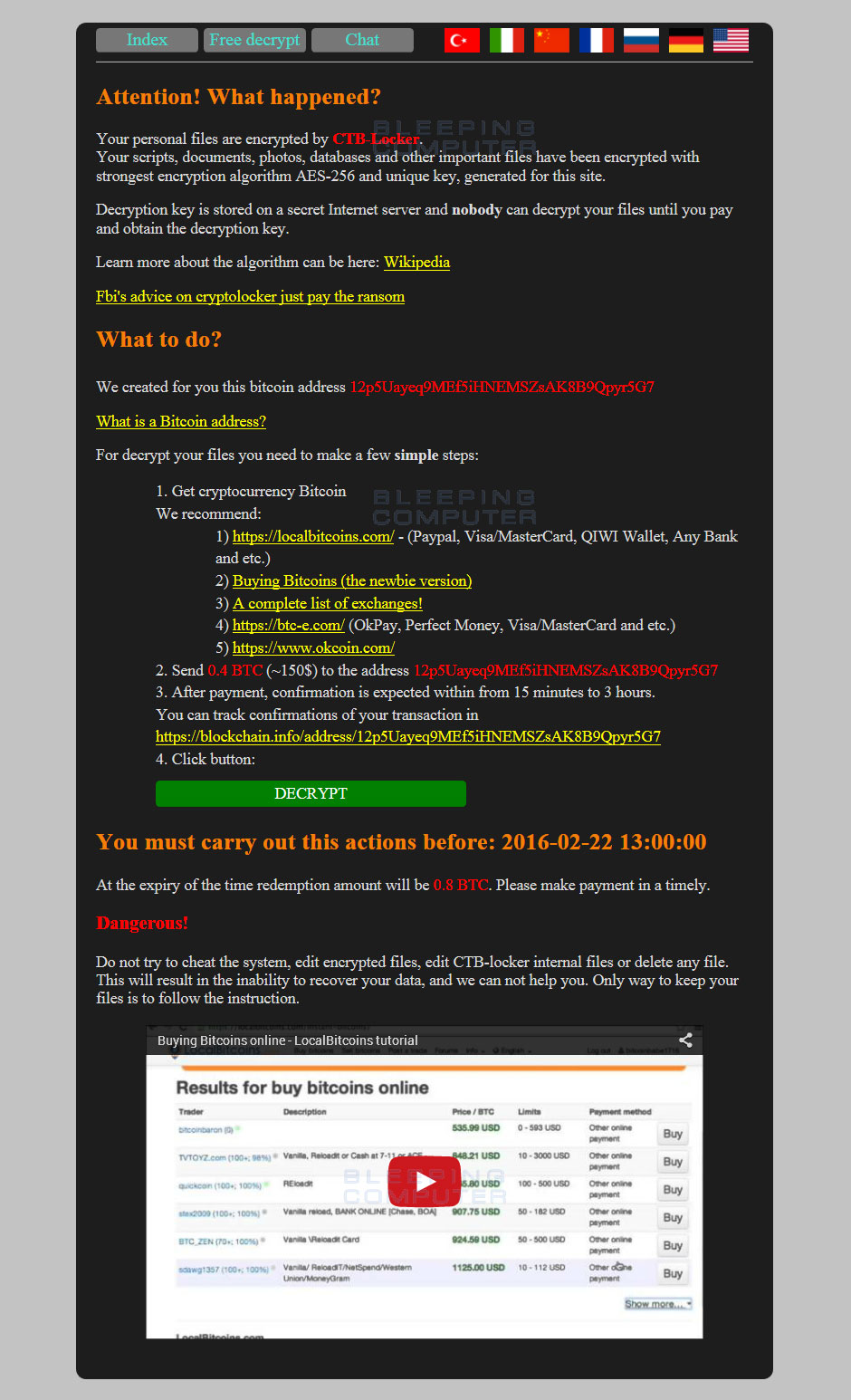
Ransom Note (Click to see full size)
Unfortunately, at this time there is no way to decrypt files encrypted by CTB-Locker for free and the only way to restore your files is via a backup. Anyone who has been affected by this ransomware should immediately contact their hosting provider to determine how the site was compromised and to see if they have any backups available for you. For those who wish to post questions or discuss this ransomware, you can use our dedicated CTB-Locker for Websites Support and Help Topic.
Though CTB-Locker for Websites appears to have affected over a hundred websites based on this Google search, I believe the impact or threat from this ransomware to be smaller than ones that target computers. This is because most website files are static and remain unchanged for quite some time and thus there is a greater chance for an admin to have backups of their current files. Furthermore, most larger websites utilize databases to store their data and these are not touched by the ransomware. Therefore, simply restoring the unencrypted files is all that is necessary to get a site back up and running.
More detailed information about how CTB-Locker for Websites encrypts a site's files, how the free decryption process works, and how to communicate with the developers is detailed below.
The CTB-Locker for Websites Encryption Process
It is currently unknown how a server becomes encrypted by CTB-Locker for Websites, but based on many of the encrypted websites that I examined, I am guessing that they are targeting vulnerable Wordpress sites. Once the developer has access to a site, they rename the existing index.php or index.html to original_index.php ororiginal_index.html. They then upload a new index.php that was created by the developer that performs the encryption, decryption, and displays the ransom note for the hacked site. It should be noted that if the website does not utilize PHP, CTB-Locker for Websites will not be able to function.
To begin the encryption process, the malware developer will submit two different AES-256 keys to the new index.php. One of these keys will be used two encrypt two prechosen test files that the victim can decrypt for free and the other key will be used to encrypt the rest of the files in the site. When encrypting the site, the script will first use the test key to encrypt the two files that will be used for free decryption. It will then generate a list of files that match specific file extensions and encrypt them using AES-256 encryption. The extensions that will be encrypted are read from the [web_site_document_root]/extensions.txt file and are currently:
264, 3g2, asf, asx, avi, bik, dash, dat, dvr, flv, h264, m2t, m2ts, 3dm, 3ds, 3gp, 7z, a3d, aa, aac, ace, adp, ai, amr, ape, apk, apng, arj, asm, asp, aspx, aws, bas, bat, bbc, blend, bml, bmp, btm, bzip2, c, c4d, cab, cdr, cfm, cgi, cgm, clear, clf, cmd, coff, cpio, cpp, cpt, cs, csv, dds, deb, dgn, dicom, dif, dll, djvu, doc, docx, dta, dvi, dwg, dxf, edi, elf, emf, eps, exe, fbx, fig, flac, gif, gpx, gzip, h, ha, hdr, htm, html, iff, ihtml, phtml, img, inf, iso, jar, java, jpe, jpeg, jpg, js, jsp, lav, lha, lib, lwo, lws, lzo, lzx, m3d, ma, mac, maf, max, mb, md, mdf, mdl, mds, mhtml, midi, mkv, ml, mmf, mng, mod, mov, mp3, msi, mxf, nrg, obj, ods, odt, ogg, out, pas, pcl, pcx, pdf, pdn, php, pkg, pl, png, pos, prg, prt, ps, psd, py, pz3, rar, raw, rb, rib, rpm, rtf, sai, sd7, sdxf, sgml, sha, shtml, sldasm, sldprt, smc, smil, spr, stdf, stm, stp, svg, swf, sxc, tar, tex, texinfo, tga, tgz, tif, tiff, troff, txt, u3d, unity, uts, vob, vsm, vue, wav, wif, wire, wlmp, wma, wmf, wmv, x, x3d, xhtml, xls, xlsx, xmi, xml, xpm, xz, zip, zoo, m4v, mp4, mpeg, mpg, mswmm, mts, ogv, prproj, rec, rmvb, tod, tp, ts, webm, 3ga, aiff, cda, dvf, gp4, gp5, logic, m4a, m4b, m4p, pcm, snd, sng, uax, wpl, dib, dng, dt2, ico, icon, pic, thm, wbmp, wdp, webp, arw, cr2, crw, dcr, fpx, mrw, nef, orf, pcd, ptx, raf, rw2, csh, drw, emz, odg, sda, abr, ani, cdt, fla, icns, mdi, psb, pzl, sup, vsdx, 3D, 3d, dwfx, lcf, pro, pts, skp, stl, x_t, eot, otf, ttc, ttf, woff, aww, chm, cnt, dbx, docm, dot, dotm, dotx, epub, ind, indd, key, keynote, mht, mpp, mpt, odf, ott, oxps, pages, pmd, pot, potx, pps, ppsx, ppt, pptm, pptx, prn, pub, pwi, rep, sdd, sdw, shs, snp, sxw, tpl, vsd, wpd, wps, wri, xps, 1st, alx, application, eng, log, lrc, lst, nfo, opml, plist, reg, srt, sub, tbl, text, xsd, xsl, xslt, azw, azw3, cbr, cbz, fb2, iba, ibooks, lit, mobi, sdc, xlsm, accdb, accdt, mdb, mpd, one, onepkg, pst, thmx, big, hi, lng, pak, res, sav, save, scn, scx, wotreplay, wowpreplay, g64, gb, gba, mbz, n64, nds, nes, rom, smd, srm, v64, ova, ovf, pvm, vdi, vhd, vmdk, vmem, vmwarevm, vmx, ashx, atom, bc, class, crdownload, css, dlc, download, eml, gdoc, gsheet, gslides, json, part, partial, rss, torrent, xap, ldif, msg, vcf, app, com, cpl, gadget, lnk, scr, tmp, vbs, bin, drv, ocx, sys, vxd, 002, 003, 004, 005, 006, 007, 008, 009, 010, 7zip, a00, a01, a02, a03, a04, a05, air, arc, asec, bar, c00, c01, c02, c03, cso, gz, hqx, inv, ipa, isz, msu, nbh, rar, r00, r01, r02, r03, r04, r05, r06, r07, r08, r09, r10, sis, sisx, sit, sitd, sitx, tar.gz, webarchive, z01, z02, z03, z04, z05, bak, bbb, bkf, bkp, dbk, gho, ipd, mdbackup, nba, nbf, nbu, nco, old, sbf, sbu, spb, tib, wbcat, 000, ccd, cue, daa, dao, dmg, mdx, tao, tc, toast, uif, vcd, crypt, ipsw, npf, pkpass, rem, rsc, gdb, ofx, qif, db, dbf, fdb, idx, msmessagestore, sdf, sql, sqlite, wdb, kml, kmz, map, appx, appxbundle, blf, dump, evtx, kext, mui, sfcache, swp, cnf, contact, deskthemepack, ics, ifo, lrtemplate, m3u, m3u8, pls, skn, svp, template, theme, themepack, trm, wba, plugin, safariextz, xpi, inc, jad, o, rc, scpt, src, cfg, ini, usr, dmp, ksd, pfx, ut, adadownload, cache, temp, 3dr, cal, dct, dic, gbk, md5, prj, ref, upd, upg
When encrypting files on a site it will exclude any files from being encrypted that contain the string /crypt/ orsecret_ or are one of the following:
[web_site_document_root]/index.php
[web_site_document_root]/allenc.txt
[web_site_document_root]/test.txt
[web_site_document_root]/victims.txt
[web_site_document_root]/extensions.txt
[web_site_document_root]/temp
[web_site_document_root]/robots.txt
The CTB-Locker for Websites package utilizes a variety of files that are described below:
Two files can be decrypted for free
CTB-Locker for Websites allows the victim to perform a test decryption of two prechosen files for free. These two files are chosen randomly from the list of files to encrypt when the site if first encrypted. It is not possible for the victim to select the files they wish to perform a test decryption on.
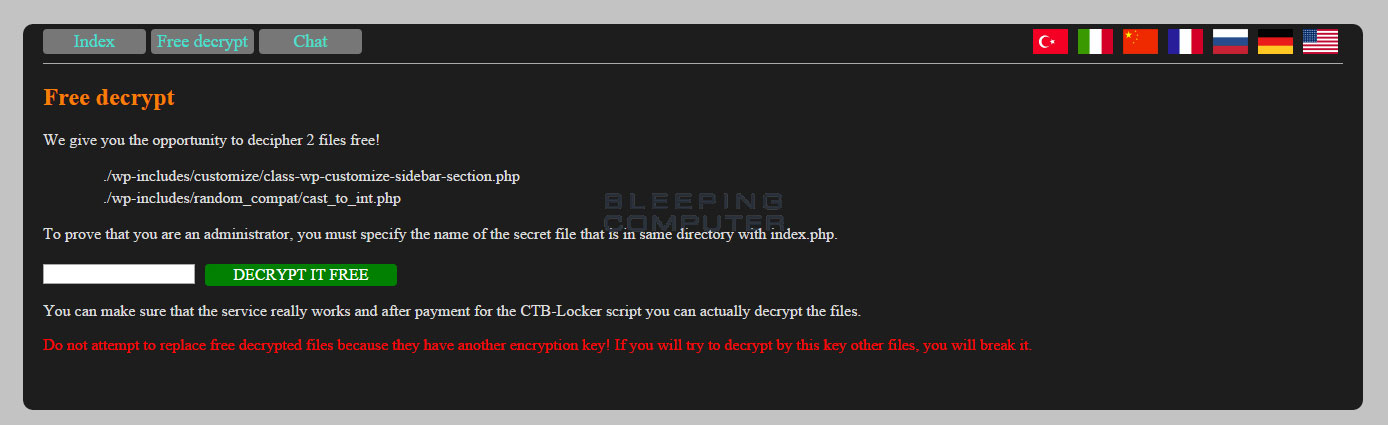
Free Decryption Screen
In order to decrypt the two free files you need to enter the filename that starts with secret_ and is located in the same folder as the index.php file. Once you enter that file and click on the Decrypt it free button, the script will use Jquery to send a request for the test decryption key to one of the Command & Control servers. When the key is received it will decrypt the two files and print Congratulations! TEST FILES WAS DECRYPTED!! to the screen.
Chatting with the developers
It is also possible to send and receive messages to and from the ransomware developer. In order to do this the victim will need to enter both a message and the secret_ filename located in the same folder as the index.php.
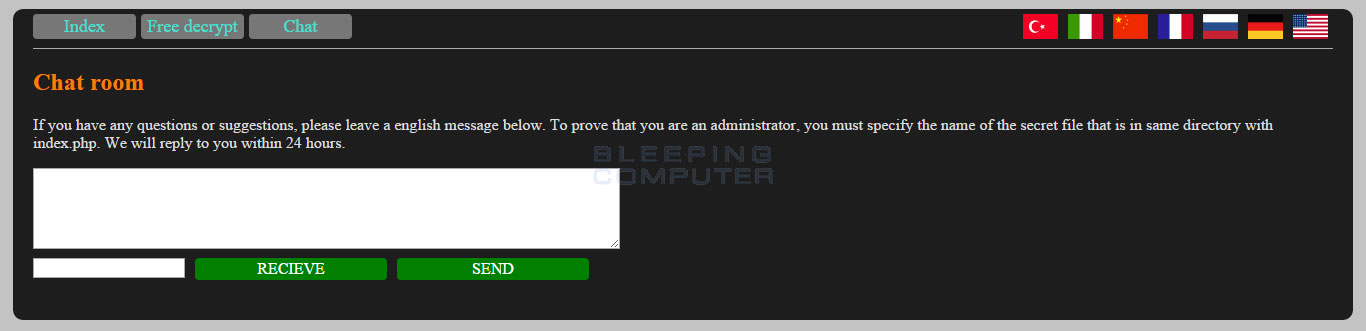
Chat screen
If you do not enter the correct secret filename, the victim will not be able to send or receive messages.
CTB-Locker for Windows is now signed with a stolen certificate
CTB-Locker for Websites is not the only new development with this ransomware. The new Windows distribution of CTB-Locker is now using executables that have been code signed with a stolen certificate. Software developers use code signing certificates to sign their programs in order to generate trust that their programs have not been tampered with and come straight from the developer. In order to get a code signing certificate a developer has to purchase one from a company that does some background checks to confirm that the developer is actually who they say they are.
Another ransomware developer named Jeiphoos allows people to go to his Encryptor RaaS Tor site and sign any executable using a stolen code-signing certificate. It appears the group behind CTB-Locker is using this free service as their signature is exactly the same as the one offered by Jeiphoos.
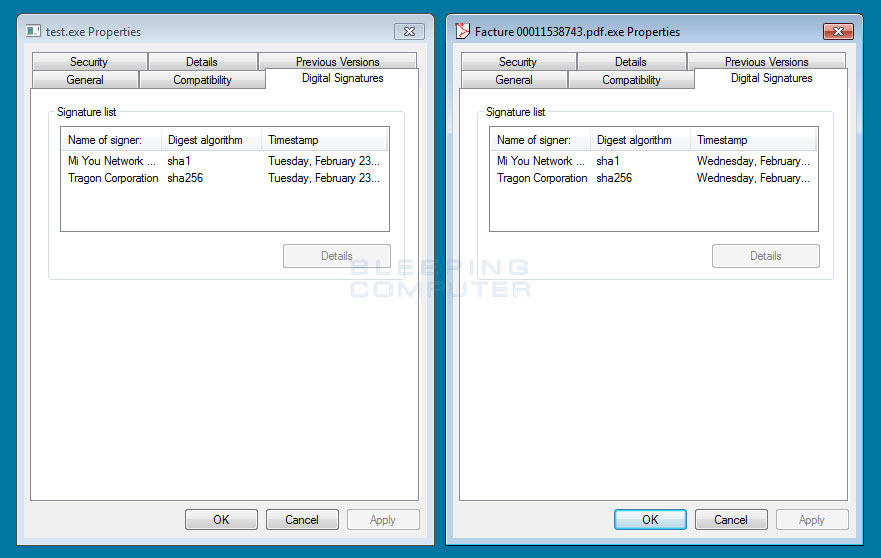
Executables signed with Jeiphoos' stolen certificates
Above is a picture of a CTB-Locker installer and a test file I signed from Jeiphoos' site. As you can see they both utilize the same code signing signature.
Related CTB-Locker Web Server Files
[web_site_document_root]/index.php
[web_site_document_root]/allenc.txt
[web_site_document_root]/test.txt
[web_site_document_root]/victims.txt
[web_site_document_root]/extensions.txt
[web_site_document_root]/temp
[web_site_document_root]/robots.txt
[web_site_document_root]/crypt/
[web_site_document_root]/crypt/secret_[victim_specific_name][/URL]
This article will primarily focus on the new website version, but will also cover a new change to the Windows variant. For victim's who requires help with CTB-Locker for Websites you can visit our support topic here: CTB-Locker for Websites Support and Help Topic.
For those who wish to analyze the source code for CTB-Locker for Websites, it was discovered by security researcher Benkow wokned and uploaded to Kernelmode. Feel free to let me know if I made any mistakes in this analysis.
CTB-Locker for Websites
CTB-Locker for Websites is a ransomware that is designed specifically to target websites, encrypt their contents, and then demand a .4 bitcoin ransom to get the decryption key. Websites become infected by the ransomware developers hacking the site and replacing the original index.php or index.html with a new index.php. This new index.php will then be used to encrypt the site's data using AES-256 encryption and to display a new home page that contains information on what has happened to the files and how to make a ransom payment.
This ransom note will state:
Your scripts, documents, photos, databases and other important files have been encrypted with strongest encryption algorithm AES-256 and unique key, generated for this site.
The CTB-Locker web page also offers the ability to decrypt two prechosen files for free and to send and receive messages with the developer. You can see an example of what a website encrypted by CTB-Locker for Websites looks like.

Ransom Note (Click to see full size)
Unfortunately, at this time there is no way to decrypt files encrypted by CTB-Locker for free and the only way to restore your files is via a backup. Anyone who has been affected by this ransomware should immediately contact their hosting provider to determine how the site was compromised and to see if they have any backups available for you. For those who wish to post questions or discuss this ransomware, you can use our dedicated CTB-Locker for Websites Support and Help Topic.
Though CTB-Locker for Websites appears to have affected over a hundred websites based on this Google search, I believe the impact or threat from this ransomware to be smaller than ones that target computers. This is because most website files are static and remain unchanged for quite some time and thus there is a greater chance for an admin to have backups of their current files. Furthermore, most larger websites utilize databases to store their data and these are not touched by the ransomware. Therefore, simply restoring the unencrypted files is all that is necessary to get a site back up and running.
More detailed information about how CTB-Locker for Websites encrypts a site's files, how the free decryption process works, and how to communicate with the developers is detailed below.
The CTB-Locker for Websites Encryption Process
It is currently unknown how a server becomes encrypted by CTB-Locker for Websites, but based on many of the encrypted websites that I examined, I am guessing that they are targeting vulnerable Wordpress sites. Once the developer has access to a site, they rename the existing index.php or index.html to original_index.php ororiginal_index.html. They then upload a new index.php that was created by the developer that performs the encryption, decryption, and displays the ransom note for the hacked site. It should be noted that if the website does not utilize PHP, CTB-Locker for Websites will not be able to function.
To begin the encryption process, the malware developer will submit two different AES-256 keys to the new index.php. One of these keys will be used two encrypt two prechosen test files that the victim can decrypt for free and the other key will be used to encrypt the rest of the files in the site. When encrypting the site, the script will first use the test key to encrypt the two files that will be used for free decryption. It will then generate a list of files that match specific file extensions and encrypt them using AES-256 encryption. The extensions that will be encrypted are read from the [web_site_document_root]/extensions.txt file and are currently:
264, 3g2, asf, asx, avi, bik, dash, dat, dvr, flv, h264, m2t, m2ts, 3dm, 3ds, 3gp, 7z, a3d, aa, aac, ace, adp, ai, amr, ape, apk, apng, arj, asm, asp, aspx, aws, bas, bat, bbc, blend, bml, bmp, btm, bzip2, c, c4d, cab, cdr, cfm, cgi, cgm, clear, clf, cmd, coff, cpio, cpp, cpt, cs, csv, dds, deb, dgn, dicom, dif, dll, djvu, doc, docx, dta, dvi, dwg, dxf, edi, elf, emf, eps, exe, fbx, fig, flac, gif, gpx, gzip, h, ha, hdr, htm, html, iff, ihtml, phtml, img, inf, iso, jar, java, jpe, jpeg, jpg, js, jsp, lav, lha, lib, lwo, lws, lzo, lzx, m3d, ma, mac, maf, max, mb, md, mdf, mdl, mds, mhtml, midi, mkv, ml, mmf, mng, mod, mov, mp3, msi, mxf, nrg, obj, ods, odt, ogg, out, pas, pcl, pcx, pdf, pdn, php, pkg, pl, png, pos, prg, prt, ps, psd, py, pz3, rar, raw, rb, rib, rpm, rtf, sai, sd7, sdxf, sgml, sha, shtml, sldasm, sldprt, smc, smil, spr, stdf, stm, stp, svg, swf, sxc, tar, tex, texinfo, tga, tgz, tif, tiff, troff, txt, u3d, unity, uts, vob, vsm, vue, wav, wif, wire, wlmp, wma, wmf, wmv, x, x3d, xhtml, xls, xlsx, xmi, xml, xpm, xz, zip, zoo, m4v, mp4, mpeg, mpg, mswmm, mts, ogv, prproj, rec, rmvb, tod, tp, ts, webm, 3ga, aiff, cda, dvf, gp4, gp5, logic, m4a, m4b, m4p, pcm, snd, sng, uax, wpl, dib, dng, dt2, ico, icon, pic, thm, wbmp, wdp, webp, arw, cr2, crw, dcr, fpx, mrw, nef, orf, pcd, ptx, raf, rw2, csh, drw, emz, odg, sda, abr, ani, cdt, fla, icns, mdi, psb, pzl, sup, vsdx, 3D, 3d, dwfx, lcf, pro, pts, skp, stl, x_t, eot, otf, ttc, ttf, woff, aww, chm, cnt, dbx, docm, dot, dotm, dotx, epub, ind, indd, key, keynote, mht, mpp, mpt, odf, ott, oxps, pages, pmd, pot, potx, pps, ppsx, ppt, pptm, pptx, prn, pub, pwi, rep, sdd, sdw, shs, snp, sxw, tpl, vsd, wpd, wps, wri, xps, 1st, alx, application, eng, log, lrc, lst, nfo, opml, plist, reg, srt, sub, tbl, text, xsd, xsl, xslt, azw, azw3, cbr, cbz, fb2, iba, ibooks, lit, mobi, sdc, xlsm, accdb, accdt, mdb, mpd, one, onepkg, pst, thmx, big, hi, lng, pak, res, sav, save, scn, scx, wotreplay, wowpreplay, g64, gb, gba, mbz, n64, nds, nes, rom, smd, srm, v64, ova, ovf, pvm, vdi, vhd, vmdk, vmem, vmwarevm, vmx, ashx, atom, bc, class, crdownload, css, dlc, download, eml, gdoc, gsheet, gslides, json, part, partial, rss, torrent, xap, ldif, msg, vcf, app, com, cpl, gadget, lnk, scr, tmp, vbs, bin, drv, ocx, sys, vxd, 002, 003, 004, 005, 006, 007, 008, 009, 010, 7zip, a00, a01, a02, a03, a04, a05, air, arc, asec, bar, c00, c01, c02, c03, cso, gz, hqx, inv, ipa, isz, msu, nbh, rar, r00, r01, r02, r03, r04, r05, r06, r07, r08, r09, r10, sis, sisx, sit, sitd, sitx, tar.gz, webarchive, z01, z02, z03, z04, z05, bak, bbb, bkf, bkp, dbk, gho, ipd, mdbackup, nba, nbf, nbu, nco, old, sbf, sbu, spb, tib, wbcat, 000, ccd, cue, daa, dao, dmg, mdx, tao, tc, toast, uif, vcd, crypt, ipsw, npf, pkpass, rem, rsc, gdb, ofx, qif, db, dbf, fdb, idx, msmessagestore, sdf, sql, sqlite, wdb, kml, kmz, map, appx, appxbundle, blf, dump, evtx, kext, mui, sfcache, swp, cnf, contact, deskthemepack, ics, ifo, lrtemplate, m3u, m3u8, pls, skn, svp, template, theme, themepack, trm, wba, plugin, safariextz, xpi, inc, jad, o, rc, scpt, src, cfg, ini, usr, dmp, ksd, pfx, ut, adadownload, cache, temp, 3dr, cal, dct, dic, gbk, md5, prj, ref, upd, upg
When encrypting files on a site it will exclude any files from being encrypted that contain the string /crypt/ orsecret_ or are one of the following:
[web_site_document_root]/index.php
[web_site_document_root]/allenc.txt
[web_site_document_root]/test.txt
[web_site_document_root]/victims.txt
[web_site_document_root]/extensions.txt
[web_site_document_root]/temp
[web_site_document_root]/robots.txt
The CTB-Locker for Websites package utilizes a variety of files that are described below:
- [web_site_document_root]/index.php - This file is the main component of CTB-Locker for Websites and contains the encryption and decryption routines as well as the payment page.
- [web_site_document_root]/allenc.txt - Contains a list of all encrypted files.
- [web_site_document_root]/test.txt - This file will contain the paths and filenames to two prechosen files that can be decrypted for free.
- [web_site_document_root]/victims.txt - Contains a list of all the files that are to be encrypted. Note that files that are already encrypted will remain in this list.
- [web_site_document_root]/extensions.txt - The list of file extensions that should be encrypted.
- [web_site_document_root]/secret_[site_specific_string] - This file is the secret file that will be used by the Free Decrypt and Chat functions. This file is located in the same folder as the index.php file.
Two files can be decrypted for free
CTB-Locker for Websites allows the victim to perform a test decryption of two prechosen files for free. These two files are chosen randomly from the list of files to encrypt when the site if first encrypted. It is not possible for the victim to select the files they wish to perform a test decryption on.

Free Decryption Screen
In order to decrypt the two free files you need to enter the filename that starts with secret_ and is located in the same folder as the index.php file. Once you enter that file and click on the Decrypt it free button, the script will use Jquery to send a request for the test decryption key to one of the Command & Control servers. When the key is received it will decrypt the two files and print Congratulations! TEST FILES WAS DECRYPTED!! to the screen.
Chatting with the developers
It is also possible to send and receive messages to and from the ransomware developer. In order to do this the victim will need to enter both a message and the secret_ filename located in the same folder as the index.php.

Chat screen
If you do not enter the correct secret filename, the victim will not be able to send or receive messages.
CTB-Locker for Windows is now signed with a stolen certificate
CTB-Locker for Websites is not the only new development with this ransomware. The new Windows distribution of CTB-Locker is now using executables that have been code signed with a stolen certificate. Software developers use code signing certificates to sign their programs in order to generate trust that their programs have not been tampered with and come straight from the developer. In order to get a code signing certificate a developer has to purchase one from a company that does some background checks to confirm that the developer is actually who they say they are.
Another ransomware developer named Jeiphoos allows people to go to his Encryptor RaaS Tor site and sign any executable using a stolen code-signing certificate. It appears the group behind CTB-Locker is using this free service as their signature is exactly the same as the one offered by Jeiphoos.

Executables signed with Jeiphoos' stolen certificates
Above is a picture of a CTB-Locker installer and a test file I signed from Jeiphoos' site. As you can see they both utilize the same code signing signature.
Related CTB-Locker Web Server Files
[web_site_document_root]/index.php
[web_site_document_root]/allenc.txt
[web_site_document_root]/test.txt
[web_site_document_root]/victims.txt
[web_site_document_root]/extensions.txt
[web_site_document_root]/temp
[web_site_document_root]/robots.txt
[web_site_document_root]/crypt/
[web_site_document_root]/crypt/secret_[victim_specific_name][/URL]