- Oct 23, 2012
- 12,527
The number of infections with file-encrypting ransomware CTB-Locker has increased during the month of February, on Thursday reaching a new height for this year.
The malware is also known as Critroni and a new version has been spotted towards the end of January, with increased activity ensuing at the beginning of this month
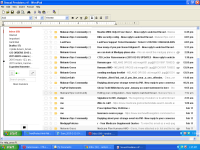
Malicious email campaigns are deployed in bursts
The distribution method for the ransomware are emails, which contain a malicious downloader responsible for retrieving and installing the malware on the affected system.
Researchers at F-Secure observed the intensification of the campaigns delivering CTB-Locker and found that the downloader used is Dalexis. It poses as an archive for a legitimate file attached to an email.
The compressed content is generally an SCR executable, although in some cases a CAB file, also executable, would be attached instead of the archive. Once launched, the downloader runs its routines for infecting the system with CTB-Locker.
As per the data from F-Secure, the activity of the malicious actors started to pick up on February 4, when almost 20% of the infections were recorded. The next day, the number increased to about 23%.
Since then, the activity dropped almost every day, and today the rate of compromised computers was less than 5%.
Although this is good news, it does not mean that the cybercriminals have given up their operation. Malicious email campaigns are generally run in bursts lasting for a few days, then the activity calms down only to restart the cycle a few days later.
File backup is the best protection
F-Secure published the ransomware message displayed by the malware after encrypting the data on the compromised computer and it is from the latest version of CTB-Locker, which increased the grace period for paying the ransom to 96 hours.
The researchers say that once the files are locked by the ransomware there is no possibility to unlock them, unless they can be restored from a backup. Paying the price demanded by the cybercriminals is not recommended to discourage this type of practice. Moreover, there is no guarantee that conforming to the request results in receiving the decryption key.
When creating a backup, users should take into consideration that storing it on network shares may not keep it safe from malware and it could also runs the risk of being encrypted, unless write permission to their location is denied. Another precaution is to mount the shares only when they are needed.
The malware is also known as Critroni and a new version has been spotted towards the end of January, with increased activity ensuing at the beginning of this month
Malicious email campaigns are deployed in bursts
The distribution method for the ransomware are emails, which contain a malicious downloader responsible for retrieving and installing the malware on the affected system.
Researchers at F-Secure observed the intensification of the campaigns delivering CTB-Locker and found that the downloader used is Dalexis. It poses as an archive for a legitimate file attached to an email.
The compressed content is generally an SCR executable, although in some cases a CAB file, also executable, would be attached instead of the archive. Once launched, the downloader runs its routines for infecting the system with CTB-Locker.
As per the data from F-Secure, the activity of the malicious actors started to pick up on February 4, when almost 20% of the infections were recorded. The next day, the number increased to about 23%.
Since then, the activity dropped almost every day, and today the rate of compromised computers was less than 5%.
Although this is good news, it does not mean that the cybercriminals have given up their operation. Malicious email campaigns are generally run in bursts lasting for a few days, then the activity calms down only to restart the cycle a few days later.
File backup is the best protection
F-Secure published the ransomware message displayed by the malware after encrypting the data on the compromised computer and it is from the latest version of CTB-Locker, which increased the grace period for paying the ransom to 96 hours.
The researchers say that once the files are locked by the ransomware there is no possibility to unlock them, unless they can be restored from a backup. Paying the price demanded by the cybercriminals is not recommended to discourage this type of practice. Moreover, there is no guarantee that conforming to the request results in receiving the decryption key.
When creating a backup, users should take into consideration that storing it on network shares may not keep it safe from malware and it could also runs the risk of being encrypted, unless write permission to their location is denied. Another precaution is to mount the shares only when they are needed.