- Feb 4, 2016
- 2,520
Kasperksy Lab has revealed today the existence of a new cyber-espionage group that has leveraged MikroTik routers to infect victims in an attack that researchers described as "unique."
Experts codenamed this group Slingshot, and evidence suggests they started operations in 2012 and were still active in February 2018.
Kaspersky experts said that because the group was active for more than half a decade, used extremely complex malware, and carried out very targeted operations; Slingshot appears to be a state-sponsored group and not your regular cyber-criminal operation focused on personal profits.
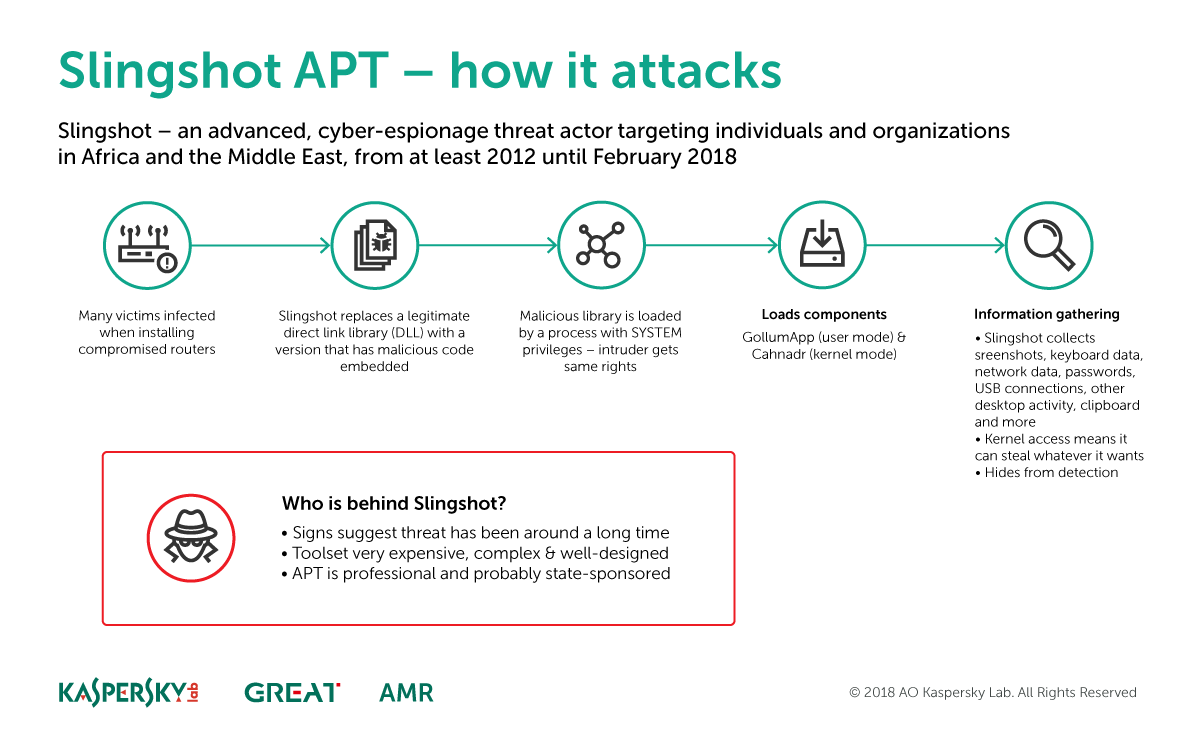
Slingshot relied on Windows exploits, hacked MikroTik routers
What impressed Kaspersky the most was the level of complexity of the entire hacking operation. The malware was very sophisticated, expensive in time and money to develop, didn't trigger errors, and the method of delivery was innovative.
While in some cases Slingshot relied on classic Windows exploits to infect targets, the attacks that stood out the most were the ones where crooks delivered their payloads by hacking into MikroTik routers.
The Slingshot group used these routers as staging points to deliver other payloads to their desired targets. The way they did this was via Winbox Loader, an application developed by MikroTik to help Windows users configure their routers.
This app works by downloading some DLLs from the router itself, but the Slingshot group replaced these files with malicious ones that infected the user when he tried to configure or reconfigure his router via the Winbox Loader app.
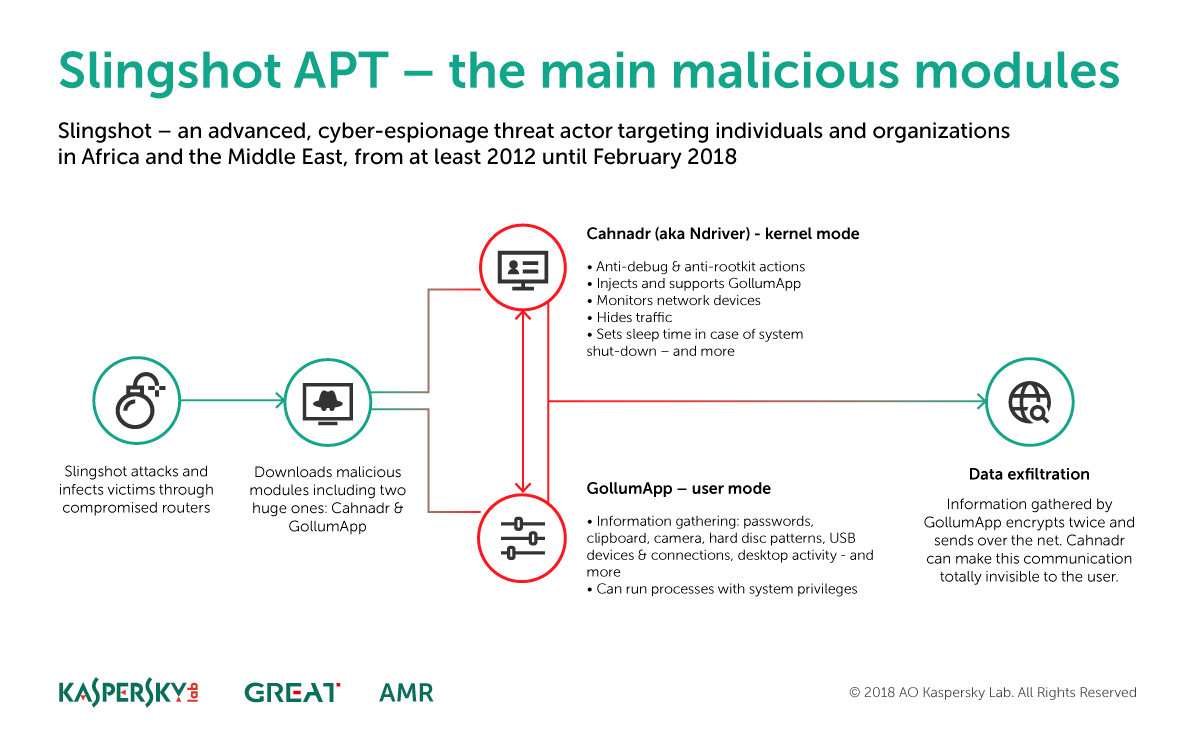
Researchers say that Slingshot usually infected users with two families of malware, namely GollumApp and Cahnadr (detected by other security vendors as NDriver). Both strains work together for information gathering, persistence, and data exfiltration.
Kaspersky says it notified MikroTik about Slingshot's mode of operation and MikroTik has modified the Winbox Loader software so it will not download anything from a local router.
As for attribution, Kaspersky experts have not made any official statements except to say that "text clues in the code suggest [Slingshot] is English-speaking."
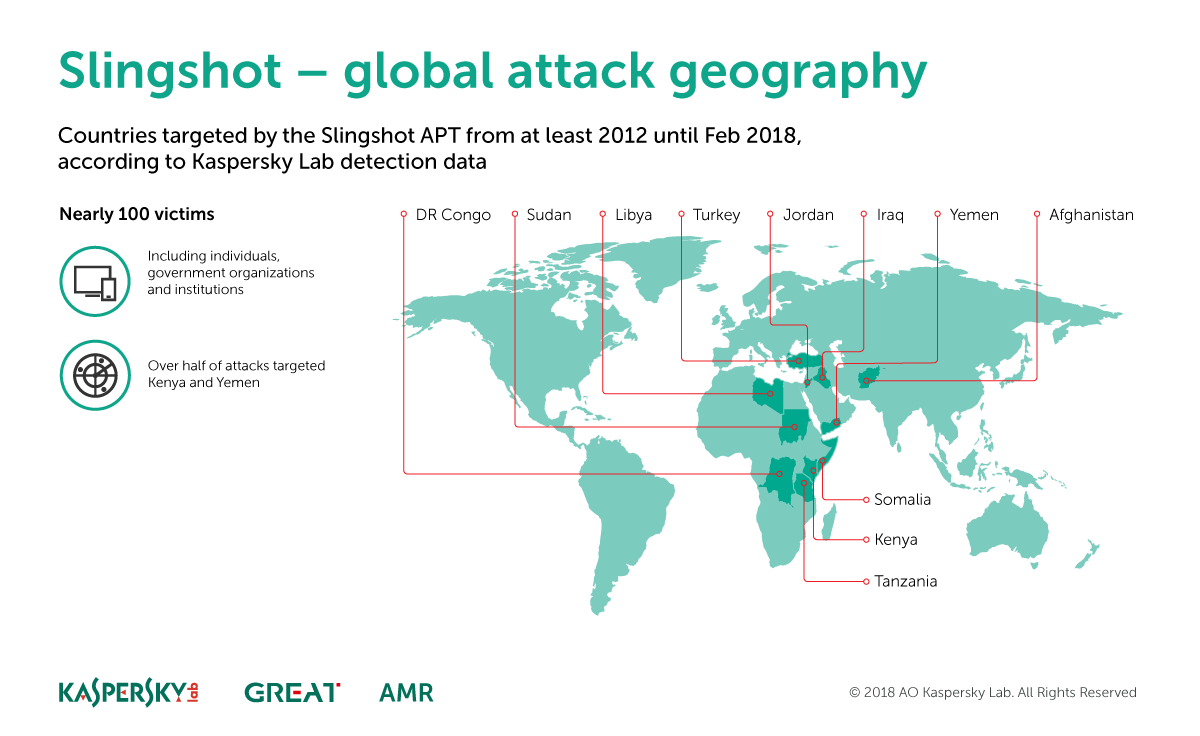
Based on current evidence, Slingshot appears to have focused on infecting lone individuals —not entire organizations— in the Middle East and North Africa.
More details about Slingshot's operations are available in this 25-page report published today by Kaspersky Lab.