silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,147
A new Dharma ransomware strain is using ESET AV Remover installations as a "smoke screen" technique designed to distract victims while their files are encrypted in the background as detailed by Trend Micro.
The ransomware is pushed by the attackers on their targets' computers using a spam campaign which delivers email attachments containing a Dharma dropper binary packed as a password-protected self-extracting archive named Defender.exe and hosted on the hacked server of link[.]fivetier[.]
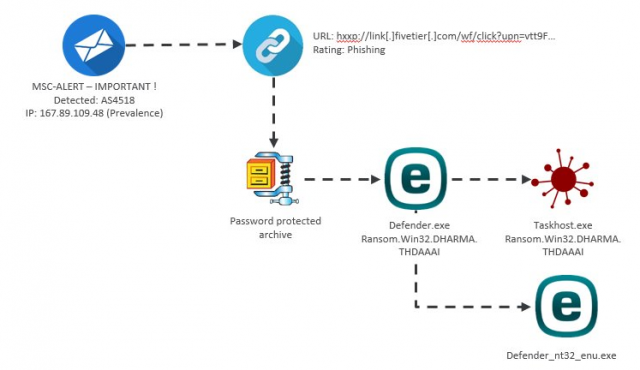
Dharma infection chain
As Trend Micro says in their analysis of this new Dharma behavior, "the ransomware will still encrypt files even if the installation is not started. The malware runs on a different instance than the software installation, so their behavior is not related."
Additionally, "The ransomware will run even if the tool installation is not triggered, and the tool can be installed even if the ransomware does not run. The installation process seems included just to trick users into thinking no malicious activity is going on."
Given that the ESET AV Remover is legitimate software signed with a valid ESET digital signature on June 22, 2017, by bundling it together with their malware the attackers are trying to pull a "magic trick" designed to divert the victims focus, keeping them busy and their attention directed at something else while Dharma quickly renders the data on their hard drives unusable.
