- Jul 27, 2015
- 5,459
- Content source
- https://www.theregister.com/2021/02/24/dns_cname_tracking/
Boffins based in Belgium have found that a DNS-based technique for bypassing defenses against online tracking has become increasingly common and represents a growing threat to both privacy and security.
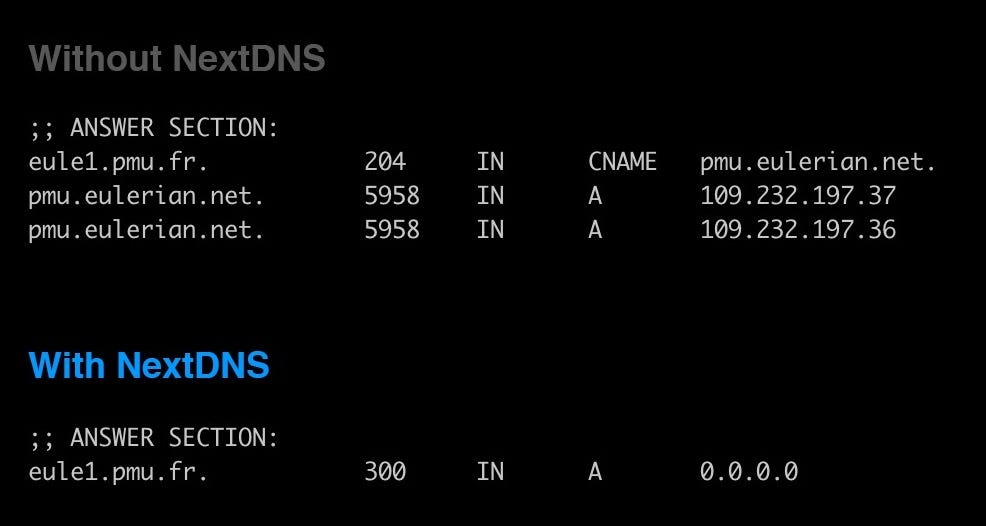
In a research paper to be presented in July at the 21st Privacy Enhancing Technologies Symposium (PETS 2021), KU Leuven-affiliated researchers Yana Dimova, Gunes Acar, Lukasz Olejnik, Wouter Joosen, and Tom Van Goethem delve into increasing adoption of CNAME-based tracking, which abuse DNS records to erase the distinction between first-party and third-party contexts. "This tracking scheme takes advantage of a CNAME record on a subdomain such that it is same-site to the including web site," the paper explains. "As such, defenses that block third-party cookies are rendered ineffective."

What's CNAME of your game? This DNS-based tracking defies your browser privacy defenses
Study sees increasing adoption of cloaking to bypass cookie barriers