- Nov 5, 2011
- 5,855
EITest: Sinkholing the oldest infection chain
proofpoint.com: EITest: Sinkholing the oldest infection chain
April 12, 2018
by Kafeine

Overview
“EITest” is a well-documented infection chain that relies on compromised websites to direct users to exploit kit (EK) landing pages, social engineering schemes, and more. EITest is likely one of the oldest of its kind and has been involved in the delivery of a variety of ransomware, information stealers, and other malware, with clear evidence of its use dating back to 2011. Recently, however, Proofpoint researchers, in collaboration with researchers from brillantit.com and abuse.ch, sinkholed EITest, rendering the infection chain ineffective and preventing as many as two million potential malicious redirects a day.
History
As we wrote in January 2017 [1], shortly after EITest started to use social engineering schemes, researchers traced the chain via server side artifacts and some historical analysis of server side compromises to infections as early as 2011 when it was redirecting to a private EK known as Glazunov. The infection chain appears to have paused between the end of 2013 and the beginning of July 2014, when it began directing into Angler (Figure 1).
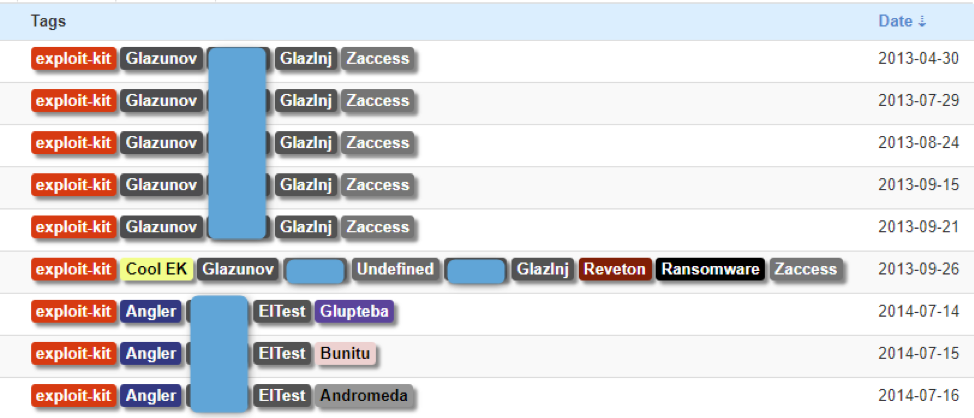
Figure 1: A selection of documented events tied to EITest before and after their pause in the first half of 2014
Looking at the history in Figure 1, we observed that the actor was spreading the Zaccess Trojan as an affiliate member, most likely for the actor’s own purposes using the Glazunov EK. Glazunov was a private EK used only by the EITest operators. It was a cousin of Kore/Sibhost EK, which in turn was exclusively used by the Urausy group [2] Examining the creation dates of EITest command and control (C&C) domains, it appears that the actor started to rework infrastructure around November 2013.
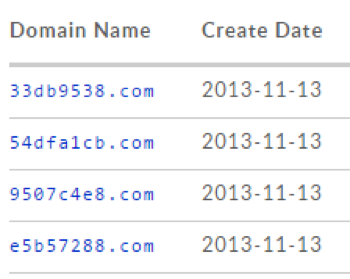
Figure 2: EITest C&C domain creation dates
In July 2014, the chain reappeared with a new infection pattern spreading multiple payloads. This sort of downstream activity is generally associated with two possible scenarios:
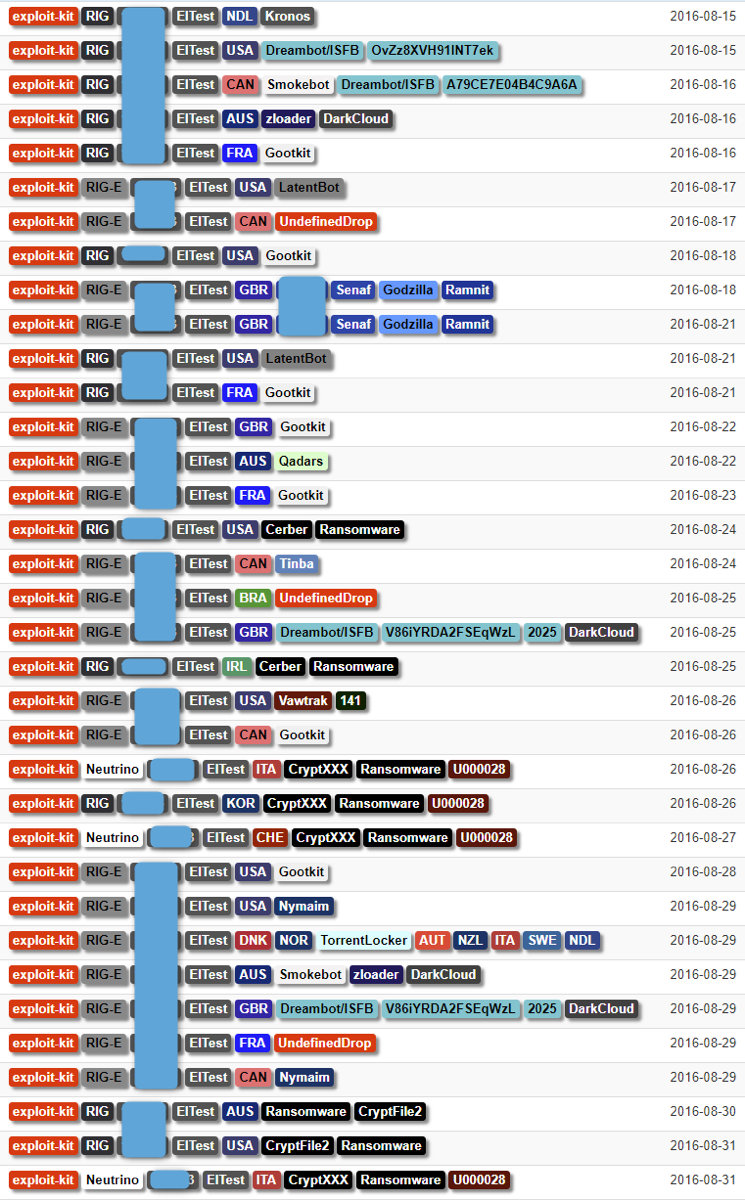
Figure 3: Two weeks of documented events tied to EITest suggesting that the actor was reselling traffic based on the diversity of EKs and payloads.
Based on EITest actor activity on underground forums and insights from Empire EK (see Appendix), we confirmed that the actor was selling traffic. In 2014, we found that the actor was selling traffic in blocks of 50-70,000 visitors for US$20 per thousand, generating between $1,000 and $1,400 per block of traffic.
As shown in Figure 4, in the past month the activity behind this infection chain has primarily consisted of social engineering [1] and tech support scams [3] leading to ransomware.
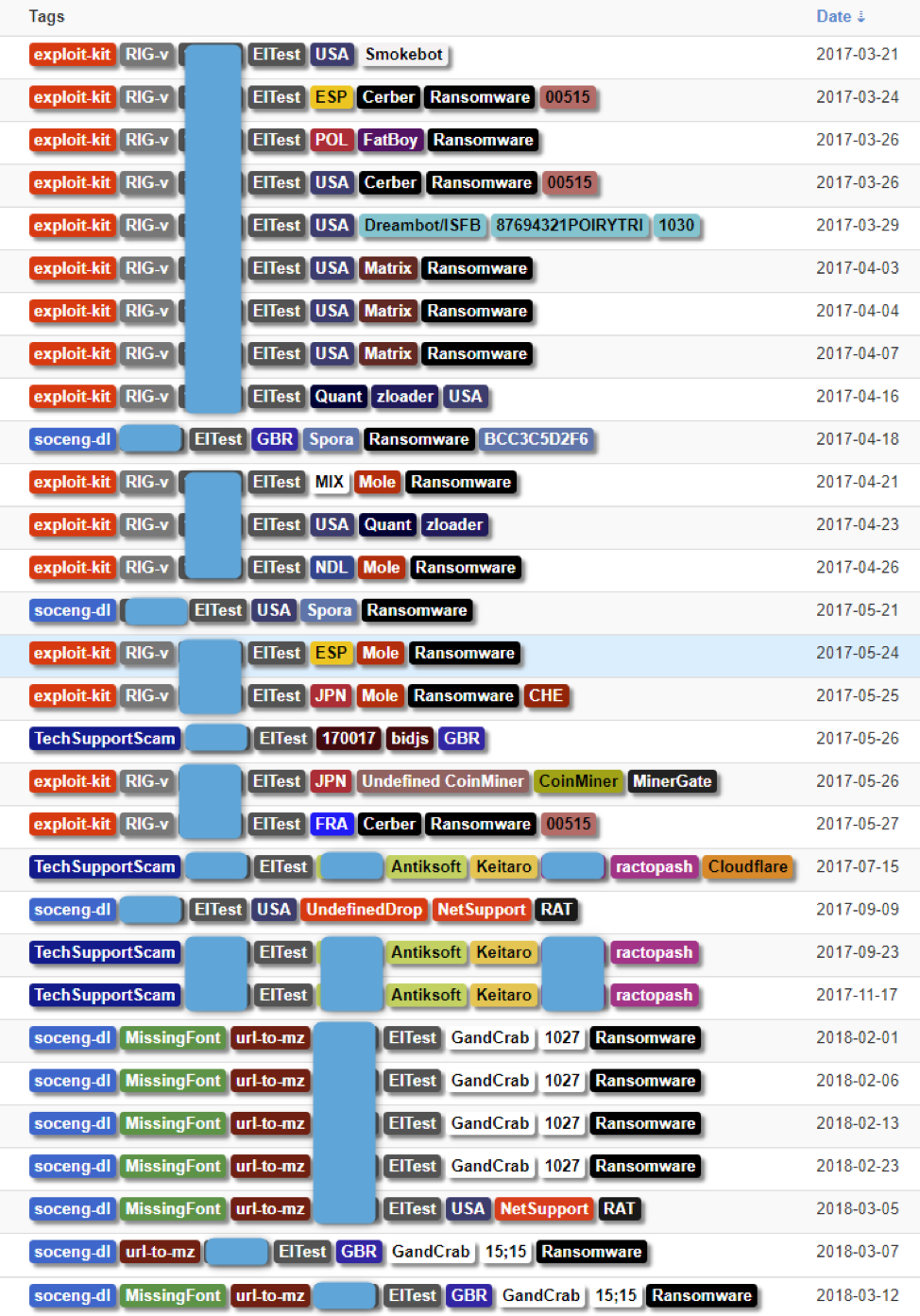
Figure 4: A selection of documented events showing the evolution of the activity behind EITest in the past year.
Sinkholing operation:
On March 15, 2018, working with abuse.ch [5] and @Secu0133 [6], we were able to fully sinkhole the EITest operation.
As @secu0133 explained in his analysis of an EITest php script [7], the C&C domains were generated from the resolution of a key domain “stat-dns[.]com”. Once seized, we pointed that domain to a new IP address to generate four new EITest C&C domains. These, in turn, were pointed to an abuse.ch sinkhole.
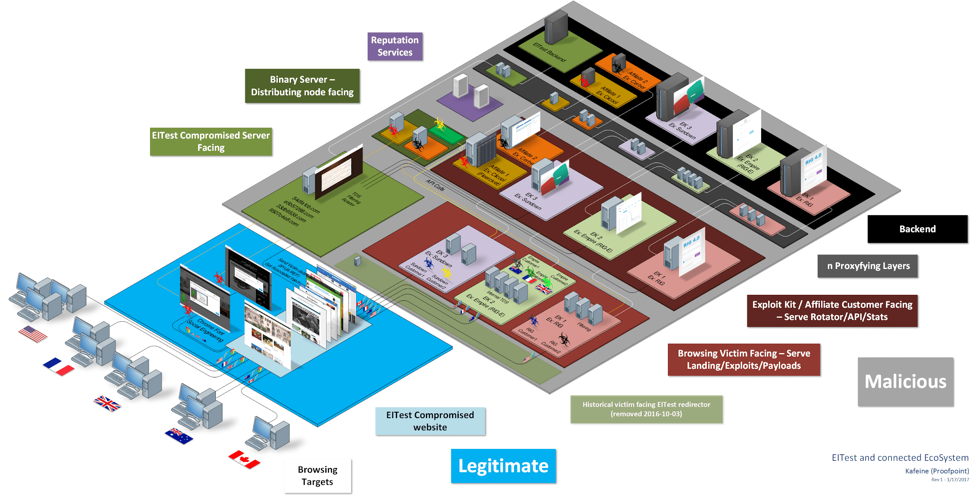
Figure 5: The EITest infrastructure and satellite in January 2017
As a result of generating those new domains, we were able to substitute the malicious server with a sinkhole. We are now receiving the traffic from the backdoors on the compromised websites, freeing them from the EITest C&Cs and their visitors from the resulting malicious traffic and injects.
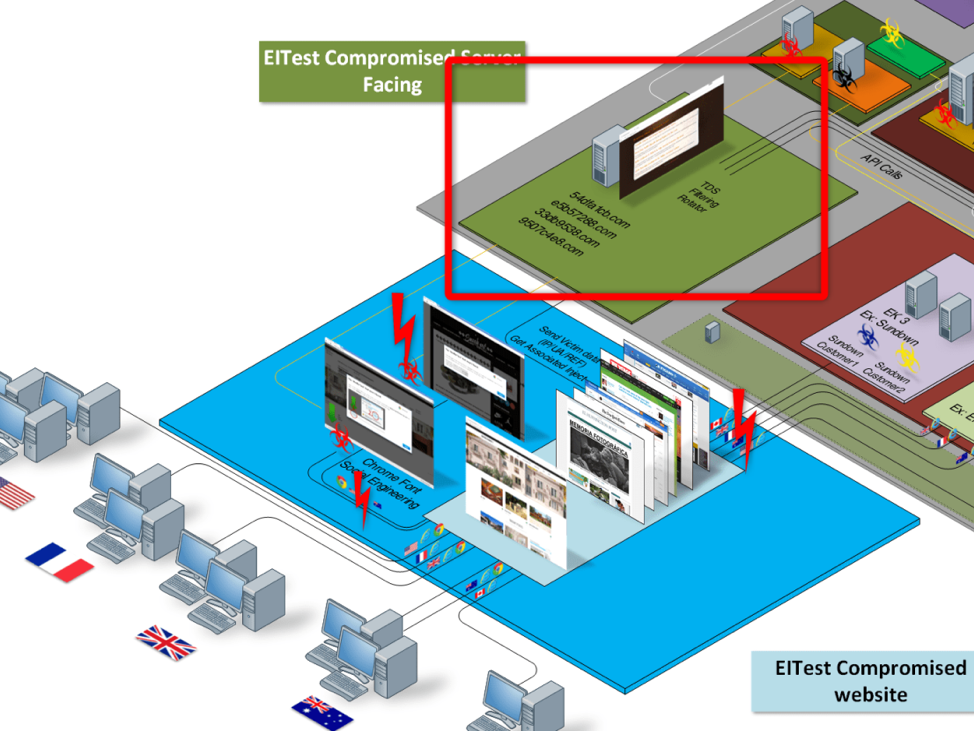
Figure 6: The red box highlights the server we substituted with a sinkhole and the connection to the EITest C&C that was closed by the sinkhole operation.
Analysis of the sinkhole:
We analyzed data from the sinkhole operation from March 15 to April 4, 2018. During that period, the sinkhole received almost 44 million requests from roughly 52,000 servers. Decoding the requests we were able to obtain a list of compromised domains as well as IP addresses and user agents of the users who had browsed to the compromised servers.
Of the compromised websites, we observed multiple content management systems, but the vast majority appeared to be using WordPress.
Figure 7 shows the geographic distribution of the 52,000 compromised servers used by EITest.
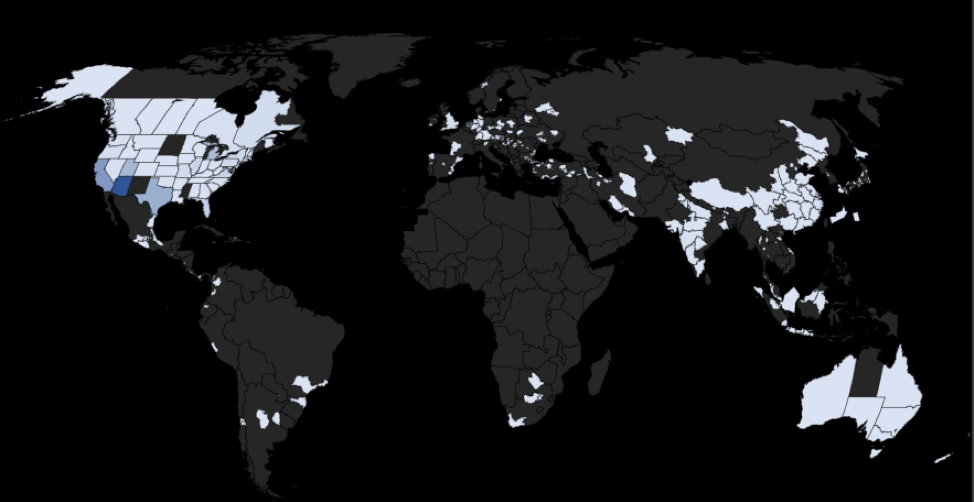
Figure 7: Worldwide distribution of the compromised servers in EITest
Figure 8 shows the worldwide distribution of browsing events -- the geographic location of would-be victims -- that triggered connections from compromised servers to the sinkhole; had the sinkhole not been in place, these events would have triggered a connection to an EITest C&C. The top ten countries by number of triggered connections appear in Figure 9.
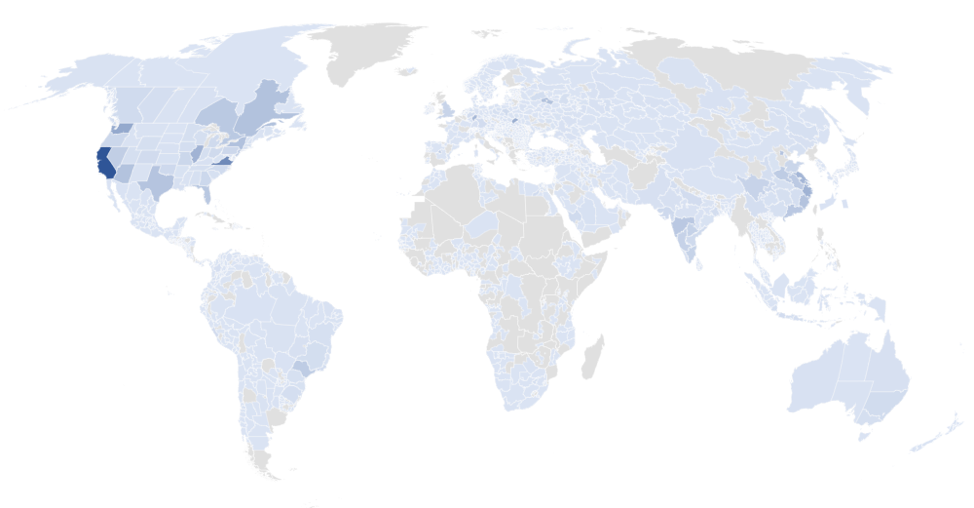
Figure 8: Geographic distribution of the browsing events that triggered connections from the compromised servers to the sinkhole
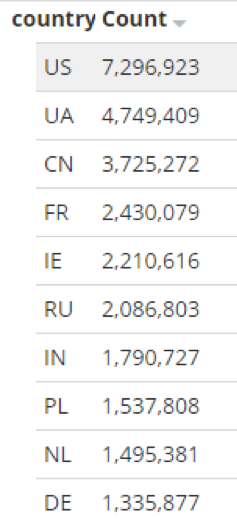
Figure 9: Top ten countries accessing EITest-compromised websites and the associated number of connections to the sinkhole between March 15 to April 4, 2018
Conclusion
EITest is one of the oldest and largest infection chains, which, early in its operation, primarily distributed malware via a private exploit kit. In more recent years, the operators of EITest became prolific sellers of traffic to EK operators and social engineering schemes through their large network of compromised web servers. Sinkholing this infection chain disrupted over two million potential malicious redirects per day with significant implications for downstream buyers of EITest traffic.
Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest. Although we witnessed some encoded calls to the sinkhole that embedded commands we would associate with takeover attempts, we cannot verify whether they were initiated by the operator or other researchers or threat actors attempting to interact with the real EITest C&C. However, we will continue to monitor EITest activity as the EITest actor may attempt to regain control of a portion of the compromised websites involved in the infection chain.
We are sharing the complete list of compromised websites with national CERTs and cleanup efforts are ongoing.
Acknowledgment
We would like to thank abuse.ch and @Secu0133 for their assistance in the sinkhole operation and data collection.
References
[1] EITest Nabbing Chrome Users with a “Chrome Font” Social Engineering Scheme
[2] The missing link - Some lights on "Urausy" affiliate
[3] The King of traffic distribution
[4] Exposing the Flash 'EITest' malware campaign - Malwarebytes Labs
[5] abuse.ch | Fighting malware and botnets
[6] V1rgul3 (@Secu0133) | Twitter
[7] Exposing EITest campaign – Malware Traffic Analysis
Indicators of Compromise (IOCs)
IOC
IOC Type
Description
54dfa1cb[.]com|31.184.192.163
domain|ip
EITest C&C (before sinkholing)
e5b57288[.]com|31.184.192.173
domain|ip
EITest C&C (before sinkholing)
33db9538[.]com|31.184.192.173
domain|ip
EITest C&C (before sinkholing)
9507c4e8[.]com|31.184.192.163
domain|ip
EITest C&C (before sinkholing)
04d92810[.]com
domain
EITest Sinkhole
c84c8098[.]com
domain
EITest Sinkhole
e42d078d[.]com
domain
EITest Sinkhole
498296c9[.]com
domain
EITest Sinkhole
stat-dns[.com
domain
Seized domain controlling the DGA
Appendix - look on the website, please...
proofpoint.com: EITest: Sinkholing the oldest infection chain
April 12, 2018
by Kafeine

Overview
“EITest” is a well-documented infection chain that relies on compromised websites to direct users to exploit kit (EK) landing pages, social engineering schemes, and more. EITest is likely one of the oldest of its kind and has been involved in the delivery of a variety of ransomware, information stealers, and other malware, with clear evidence of its use dating back to 2011. Recently, however, Proofpoint researchers, in collaboration with researchers from brillantit.com and abuse.ch, sinkholed EITest, rendering the infection chain ineffective and preventing as many as two million potential malicious redirects a day.
History
As we wrote in January 2017 [1], shortly after EITest started to use social engineering schemes, researchers traced the chain via server side artifacts and some historical analysis of server side compromises to infections as early as 2011 when it was redirecting to a private EK known as Glazunov. The infection chain appears to have paused between the end of 2013 and the beginning of July 2014, when it began directing into Angler (Figure 1).

Figure 1: A selection of documented events tied to EITest before and after their pause in the first half of 2014
Looking at the history in Figure 1, we observed that the actor was spreading the Zaccess Trojan as an affiliate member, most likely for the actor’s own purposes using the Glazunov EK. Glazunov was a private EK used only by the EITest operators. It was a cousin of Kore/Sibhost EK, which in turn was exclusively used by the Urausy group [2] Examining the creation dates of EITest command and control (C&C) domains, it appears that the actor started to rework infrastructure around November 2013.

Figure 2: EITest C&C domain creation dates
In July 2014, the chain reappeared with a new infection pattern spreading multiple payloads. This sort of downstream activity is generally associated with two possible scenarios:
- The actor is selling loads (infections) or
- The actor is selling traffic (to other actors, a load seller, or both)

Figure 3: Two weeks of documented events tied to EITest suggesting that the actor was reselling traffic based on the diversity of EKs and payloads.
Based on EITest actor activity on underground forums and insights from Empire EK (see Appendix), we confirmed that the actor was selling traffic. In 2014, we found that the actor was selling traffic in blocks of 50-70,000 visitors for US$20 per thousand, generating between $1,000 and $1,400 per block of traffic.
As shown in Figure 4, in the past month the activity behind this infection chain has primarily consisted of social engineering [1] and tech support scams [3] leading to ransomware.

Figure 4: A selection of documented events showing the evolution of the activity behind EITest in the past year.
Sinkholing operation:
On March 15, 2018, working with abuse.ch [5] and @Secu0133 [6], we were able to fully sinkhole the EITest operation.
As @secu0133 explained in his analysis of an EITest php script [7], the C&C domains were generated from the resolution of a key domain “stat-dns[.]com”. Once seized, we pointed that domain to a new IP address to generate four new EITest C&C domains. These, in turn, were pointed to an abuse.ch sinkhole.

Figure 5: The EITest infrastructure and satellite in January 2017
As a result of generating those new domains, we were able to substitute the malicious server with a sinkhole. We are now receiving the traffic from the backdoors on the compromised websites, freeing them from the EITest C&Cs and their visitors from the resulting malicious traffic and injects.

Figure 6: The red box highlights the server we substituted with a sinkhole and the connection to the EITest C&C that was closed by the sinkhole operation.
Analysis of the sinkhole:
We analyzed data from the sinkhole operation from March 15 to April 4, 2018. During that period, the sinkhole received almost 44 million requests from roughly 52,000 servers. Decoding the requests we were able to obtain a list of compromised domains as well as IP addresses and user agents of the users who had browsed to the compromised servers.
Of the compromised websites, we observed multiple content management systems, but the vast majority appeared to be using WordPress.
Figure 7 shows the geographic distribution of the 52,000 compromised servers used by EITest.

Figure 7: Worldwide distribution of the compromised servers in EITest
Figure 8 shows the worldwide distribution of browsing events -- the geographic location of would-be victims -- that triggered connections from compromised servers to the sinkhole; had the sinkhole not been in place, these events would have triggered a connection to an EITest C&C. The top ten countries by number of triggered connections appear in Figure 9.

Figure 8: Geographic distribution of the browsing events that triggered connections from the compromised servers to the sinkhole

Figure 9: Top ten countries accessing EITest-compromised websites and the associated number of connections to the sinkhole between March 15 to April 4, 2018
Conclusion
EITest is one of the oldest and largest infection chains, which, early in its operation, primarily distributed malware via a private exploit kit. In more recent years, the operators of EITest became prolific sellers of traffic to EK operators and social engineering schemes through their large network of compromised web servers. Sinkholing this infection chain disrupted over two million potential malicious redirects per day with significant implications for downstream buyers of EITest traffic.
Following the successful sinkhole operation, the actor shut down their C&C proxies, but we have not observed further overt reactions by the operators of EITest. Although we witnessed some encoded calls to the sinkhole that embedded commands we would associate with takeover attempts, we cannot verify whether they were initiated by the operator or other researchers or threat actors attempting to interact with the real EITest C&C. However, we will continue to monitor EITest activity as the EITest actor may attempt to regain control of a portion of the compromised websites involved in the infection chain.
We are sharing the complete list of compromised websites with national CERTs and cleanup efforts are ongoing.
Acknowledgment
We would like to thank abuse.ch and @Secu0133 for their assistance in the sinkhole operation and data collection.
References
[1] EITest Nabbing Chrome Users with a “Chrome Font” Social Engineering Scheme
[2] The missing link - Some lights on "Urausy" affiliate
[3] The King of traffic distribution
[4] Exposing the Flash 'EITest' malware campaign - Malwarebytes Labs
[5] abuse.ch | Fighting malware and botnets
[6] V1rgul3 (@Secu0133) | Twitter
[7] Exposing EITest campaign – Malware Traffic Analysis
Indicators of Compromise (IOCs)
IOC
IOC Type
Description
54dfa1cb[.]com|31.184.192.163
domain|ip
EITest C&C (before sinkholing)
e5b57288[.]com|31.184.192.173
domain|ip
EITest C&C (before sinkholing)
33db9538[.]com|31.184.192.173
domain|ip
EITest C&C (before sinkholing)
9507c4e8[.]com|31.184.192.163
domain|ip
EITest C&C (before sinkholing)
04d92810[.]com
domain
EITest Sinkhole
c84c8098[.]com
domain
EITest Sinkhole
e42d078d[.]com
domain
EITest Sinkhole
498296c9[.]com
domain
EITest Sinkhole
stat-dns[.com
domain
Seized domain controlling the DGA
Appendix - look on the website, please...