Gandalf_The_Grey
Level 76
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
- Apr 24, 2016
- 6,567
Through worldwide cooperation of cyber specialists, one of the largest botnets of Emotet threats has been shut down. Unfortunately, however, this network was only one of many, which means that attacks with Emotet still remain a major threat. AV-TEST provides background and explanations.
Admittedly, it was one of the best items of news at the end of January 2021: following in-depth preparation, an action planned by international police and law enforcement agencies led to the intended success. They were able to take down one of the key botnets that was instrumental in coordinating the use of malware attacks with Emotet. The first erroneous interpretation of the press release: it was not the botnet of Emotet that was destroyed but rather one of the largest networks mainly using Emotet as a weapon of attack. While this resulted in a temporary reduction in the number of attacks, in the meantime the gap has been closed by other competing botnets using the same weapons. This is also evidenced by the status of data on registered phishing and malware e-mails recorded in the AV-Atlas.org threat portal.
Behind the scenes of Emotet
The Emotet malware describes an entire malware family and is considered a macro virus. Many mutant specimens have been cropping up for years on the Internet, preying on consumers and corporate users. Emotet is structurally very small and has no arsenal of coded weapons of attack in its quiver. Rather, it is a clever door opener, which then ushers the big-gun attack specialists into the systems.
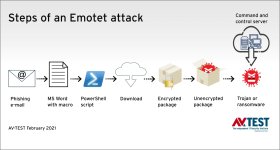
The Emotet attack step-by-step
In general terms, this is how an attack works: first the recipient receives a sophisticated fake e-mail in the name of a known customer or telecom provider, for example. The e-mail either directly contains a word file attachment in *.doc format or links to a malicious file. In the e-mail, the user is informed that it is absolutely necessary to allow active content in the *.doc file (enable macros). The code is so small that analysis is a challenge for security systems.
As soon as the macro code is launched and the PC is infected in this way, Emotet opens the doors and allows access to dangerous threats like malware heavyweights such as Trickbot or Ryuk. Trickbot is a notorious banking Trojan or crypto miner. So it steals log-on details and passwords or launches crypto miner workloads on PCs or servers, and mines for cryptocurrencies. With Ryuk, a known ransomware is introduced into the system, which encrypts the data and starts a classic round of blackmail: those who pay quickly will purportedly receive the respective decryption tool. Emotet continues to hijack the e-mail program, along with the address book, proliferating further. Unfortunately, this is very effective, as the sender is known to the receivers of the new infected e-mail and considered trustworthy.
Thus, the attacks or their consequences are not always the same. What's more, the exact types of Emotet, Trickbot or Ryuk, for instance, often vary. Through analysis with the help of the servers controlling the botnet, Emotet can also find out whether it has landed on a private PC or on a workstation in a corporate network. This also influences how the attacker will further proceed. Once Emotet is in a network, it attempts to directly spread out among additional corporate PCs.
Read the full story here at AV-TEST:

Emotet – Never Let Your Guard Down
Through worldwide cooperation of cyber specialists, one of the largest botnets of Emotet threats has been shut down. Unfortunately, however, this network was only one of many, which means that attacks with Emotet still remain a major threat. AV-TEST provides background and explanations.
