- Feb 4, 2016
- 2,520
A new information stealing Trojan called Evrial is being sold on criminal forums and being actively distributed in the wild. Like most infostealing Trojans, Evrial can steal browser cookies and stored credentials, but this Trojan also has the ability to monitor the Windows clipboard for certain text, and if detected, modify it to something else.
First discovered and tracked by security researchers MalwareHunterTeam and Guido Not CISSP, by monitoring the Windows clipboard for certain strings, Evrial makes it easy for attackers to hijack cryptocurrency payments and Steam trades. This is done by replacing legitimate payment addresses and URLs with addresses under the attacker's control.
...
.......
............
Evrial being sold on criminal forums
According to MalwareHunterTeam, Evrial is currently being sold on Russian criminal forums for 1,500 Rubles or ~ $27 USD. In the advertisement, the seller states that after purchasing the product, an attacker gains access to a web panel that allows them to build an executable. This web panel also keeps track of what clipboard modifications have taken place and allows an attacker to configure what replacement strings should be used.
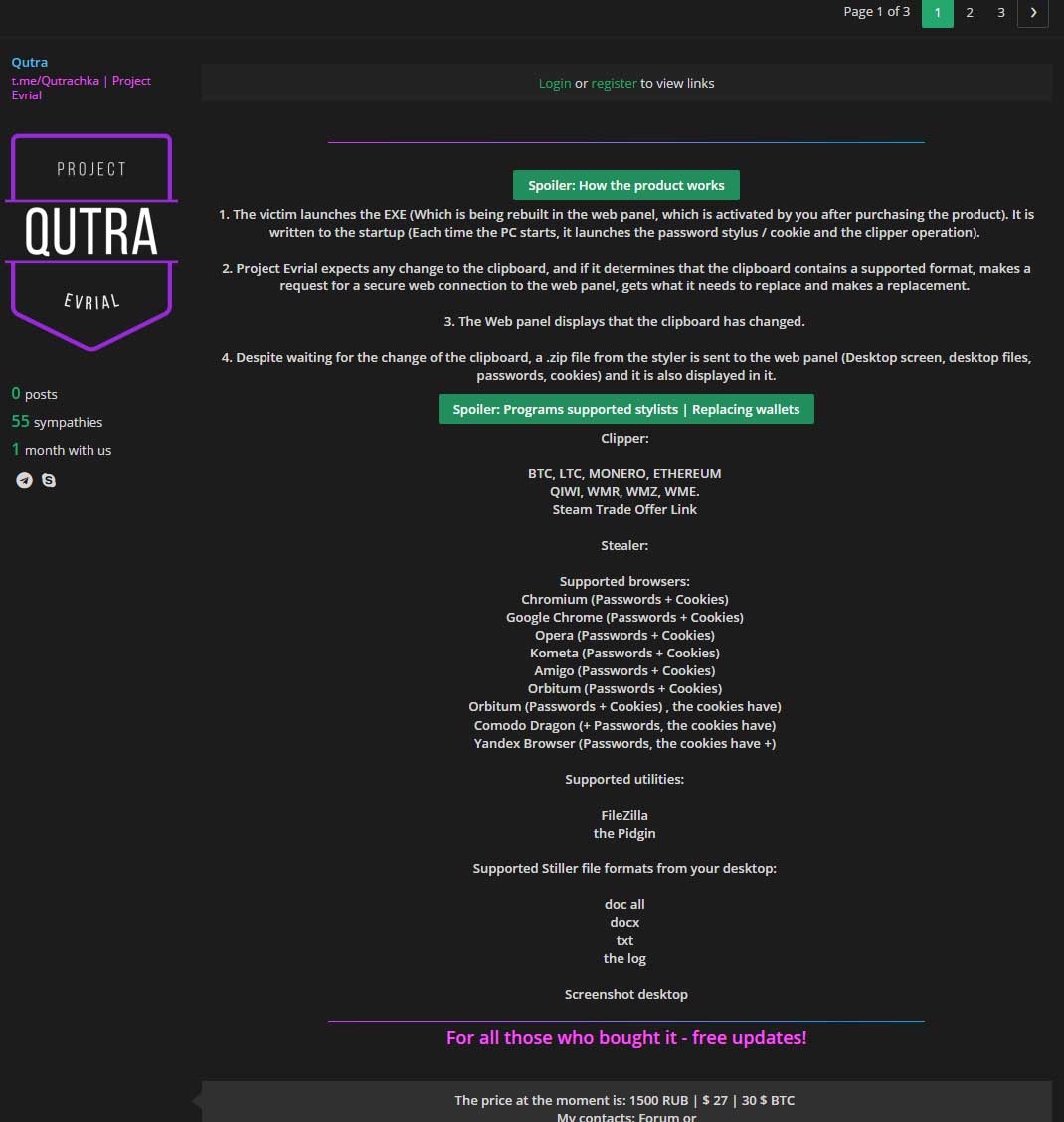
Translated Post on a Russian Forum
Included in the advertisement are some sample screenshots of the web panel as shown below.
Evrial takes control of the Windows clipboard
Evrial's most interesting feature is that it will monitor the Windows clipboard for certain types of strings and replace them with ones sent by the attacker. This allows the attacker to reroute a cryptocurrency payment to an address under their control. While clipboard monitoring is common with programs like this, MalwareHunterTeam has told BleepingComputer that modifications are much more rare.
For example, bitcoin addresses are not the easiest string of text to type into a program or website. Due to this, when someone sends bitcoins to an exchange or wallet, they typically copy the address that the coins should be sent to into the Windows clipboard and then paste that address into the other app or site that is performing the sending.
When Evrial detects a bitcoin address in the clipboard, it replaces that legitimate address with one under the attacker's control. The victim then pastes that address into their app, thinking its the legitimate one and not realizing its been replaced, and clicks send. Now when the bitcoins are sent, they go to the attackers address rather than your intended recipient.
Evrial is configured to detects strings that correspond to Bitcoin, Litecoin, Monero, WebMoney, Qiwi addresses and Steam items trade urls.
Evrial steals passwords documents
In addition to monitoring and modifying the clipboard, Evrial will also steal bitcoin wallets, stored passwords, documents from the victim's desktop, and a screenshot of the active windows. All of this information will be compiled into a zip file and uploaded to the attackers web panel as shown below.
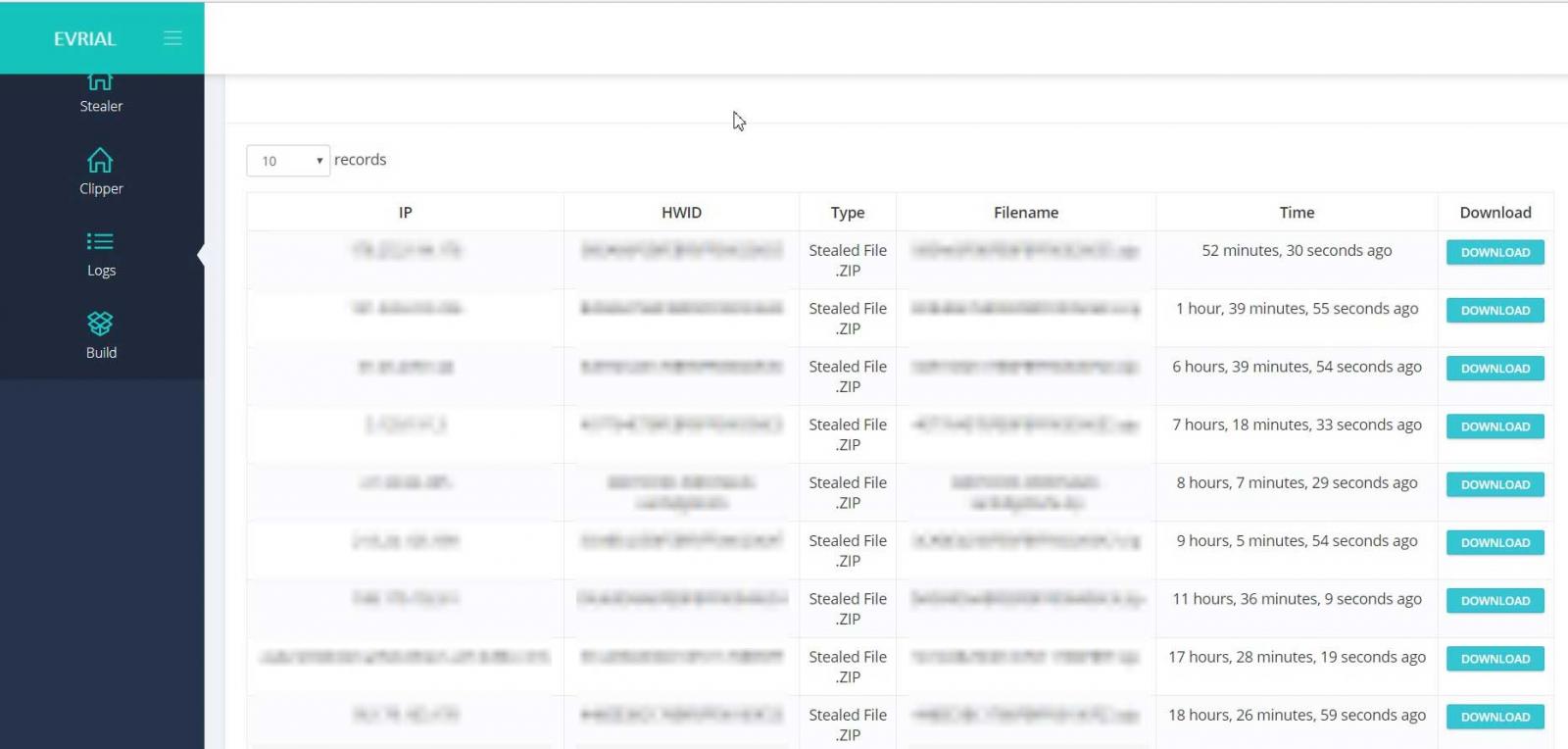
Evrial will determine the location of Bitcoin's wallet.dat file from querying a registry key. If the key exists, it will then steal that wallet so it can gain access to the victim's bitcoins.
How to protect yourself from Evrial
At this time it not 100% known how Evrial is being distributed, but the best way to protect yourself is to practice good computing habits. Make sure that you have security software installed, that you scan attachments that you receive using a site like VirusTotal, and that you practice good and safe computing habits.
A tutorial on how to use your computer safely can be found here: Simple and easy ways to keep your computer safe and secure on the Internet
Last edited:
