New research published yesterday reveals that putting your trust in Extended Validation ("EV") SSL certificates will not safeguard you from phishing sites and online fraud.
SSL certificates have become quite a common occurrence on the Internet.
According to Let’s Encrypt, 65% of web pages loaded by Firefox in November used HTTPS, compared to 45% at the end of 2016.
Anyone can get a free or paid SSL certificate to secure a website via HTTPS. A report released by Phish Labs last week shows that
one in four phishing sites currently loads via HTTPS.
EV certificates deployed in 2007 to fight phishing
The people behind the SSL industry knew this abuse was eventually going to happen, albeit they did not know when.
This is why they came up with the concept of "
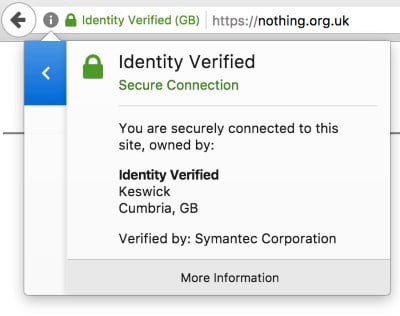
Extended Validation Certificates" in 2007, which are special SSL certificates that are only granted to companies that go through an extended verification process —standardized in the Extended Validation (EV) SSL Guidelines.
These extra verifications include additional paperwork that would create a more extensive paper trail, something that most crooks wouldn't risk leaving behind.
On the other hand, companies that obtain an EV certificate get a reputational boost. In recent years, browsers have started showing the company's name inside the address bar, as a way to reinforce and guarantee the site's identity to users.