- Feb 4, 2016
- 2,520

Google has removed 53 apps from the official Play Store because they were spreading a new breed of Android malware named GhostTeam that could steal Facebook credentials and push ads to infected phones.
Discovered by the mobile security teams at Avast and Trend Micro, researchers say the malware has been active on the Play Store since April 2017, but only recently discovered and reported to the Google team.
GhostTeam uses benign apps to infect devices
GhostTeam's modus operandi is up to par with the latest distribution techniques, currently in vogue with most Android malware developers.
The initial infections occur when users install a clean app with legitimate features. This app is known as a "dropper" and will, at some point, contact a remote command-and-control server from where it will download and install secondary apps that contain the real GhostTeam malware.
This second-stage app is usually disguised as a system-level app. Attackers use fake security alerts displayed via the original app to trick users into installing the second app and gaining admin rights.
Once the second app obtains admin-level access, GhostTeam will primarily show intrusive ads on the user's phone.
Facebook login data theft as a secondary function
As a secondary function, researchers say they've also seen GhostTeam stealing Facebook credentials. The method it uses is somewhat unique, as the app doesn't use fake login screens overlaid on top of the original Facebook app, but steals data from the actual Facebook login page.
It achieves this by detecting when the user tries to open the real Facebook app, and then opening the real Facebook login page inside a native Android headless browser component, such as WebView or WebChromeClient. These are portable browser that developers can embed inside their apps, and over which app developers have full control.
The GhostTeam-infected app loads the real Facebook login page inside these portable browsers, but it also loads malicious JavaScript code that harvests the user's Facebook login credentials. This data is later sent to a remote server under the attackers' control.
Because the login operations take place on the actual Facebook login page and inside a legitimate Android component, mobile security products cannot detect this credentials harvesting method.
Despite this, the top countries affected by GhostTeam are India, Indonesia, and Brazil, all three accounting for 60% of all infections.
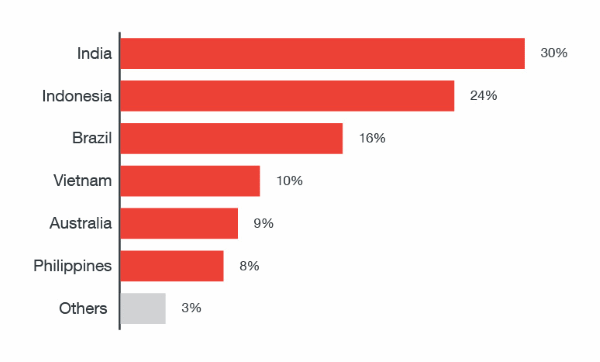
Even if Google has removed most of the malicious dropper apps that installed GhostTeam as a second-stage payload, some of these apps may still be active on some users' phones. Trend Micro has released a list with the names of all malicious apps. Most are unsophisticated apps such as flashlight apps, QR code scanners, compass apps, and device optimization and device cleaning apps.
If users find any of these apps on their phones, they should immediately change their Facebook credentials and enable two-factor authentication.
The two security firm believe miscreants used GhostTeam to earn money via the ads they pushed to infected devices and by surreptitiously liking and sharing content via compromised accounts as part of social promotion services.

