silversurfer
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Malware Hunter
Well-known
- Aug 17, 2014
- 10,148
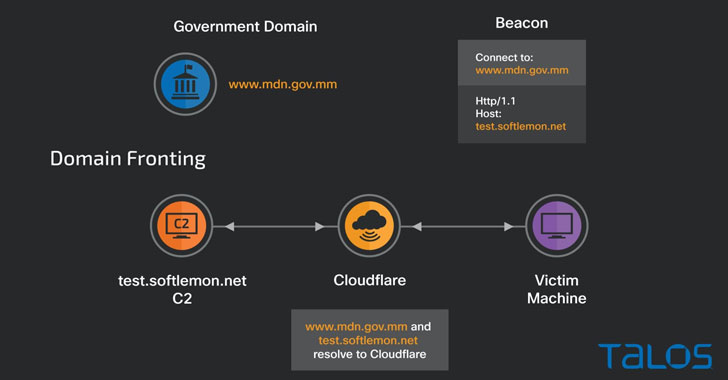
A malicious campaign has been found leveraging a technique called domain fronting to hide command-and-control traffic by leveraging a legitimate domain owned by the Myanmar government to route communications to an attacker-controlled server with the goal of evading detection.
The threat, which was observed in September 2021, deployed Cobalt Strike payloads as a stepping stone for launching further attacks, with the adversary using a domain associated with the Myanmar Digital News network, a state-owned digital newspaper, as a front for their Beacons.
"When the Beacon is launched, it will submit a DNS request for a legitimate high-reputation domain hosted behind Cloudflare infrastructure and modify the subsequent HTTPs requests header to instruct the CDN to direct the traffic to an attacker-controlled host," Cisco Talos researchers Chetan Raghuprasad, Vanja Svajcer, and Asheer Malhotra said in a technical analysis published Tuesday.

Hackers Targeting Myanmar Use Domain Fronting to Hide Malicious Activities
Hackers Targeting Myanmar Use Domain Fronting to Hide Malicious Activities
 thehackernews.com
thehackernews.com