- Feb 7, 2014
- 1,540
“In the following table, first column represents the Anti-Malware, the second the number of samples (without transformations) correctly detected by the antimalware while in the third column (in red) the number of correctly detected samples after transformation process.”
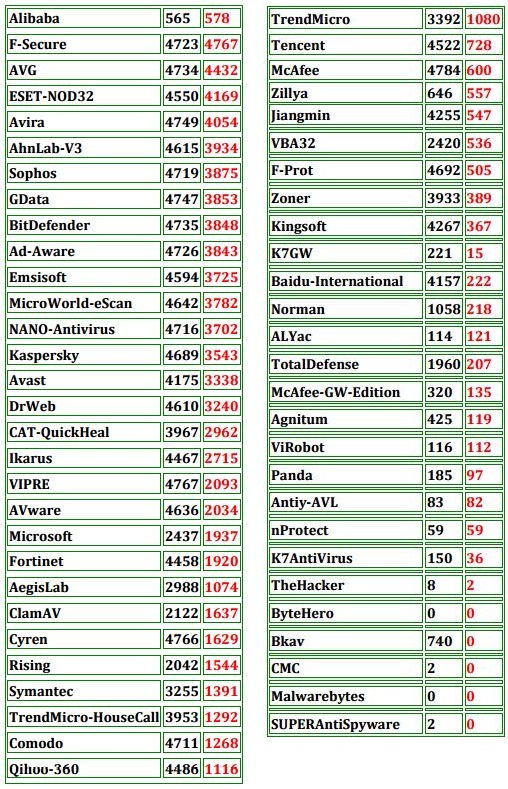
“The results is impressive: the antimalware is not able to recognize the transformed malware (given that it was able to recognize the original malware).
The transformation engine is released for the scientific community with the open source license at the following url: https://github.com/faber03/AndroidMalwareEvaluatingTools“
The details of the test conducted by the Iswatlab are included in the report titled “Evaluating malware obfuscation techniques against antimalware detection algorithms”
This test raises the discussion about the capability to limit the production of malware, the experts at the Iswatlab were able to create new malware without writing any line of new code, but just scrambling some old well-known threats.
You can read the rest of the news here: http://securityaffairs.co/wordpress/51714/malware/evading-antimalware.html

“The results is impressive: the antimalware is not able to recognize the transformed malware (given that it was able to recognize the original malware).
The transformation engine is released for the scientific community with the open source license at the following url: https://github.com/faber03/AndroidMalwareEvaluatingTools“
The details of the test conducted by the Iswatlab are included in the report titled “Evaluating malware obfuscation techniques against antimalware detection algorithms”
This test raises the discussion about the capability to limit the production of malware, the experts at the Iswatlab were able to create new malware without writing any line of new code, but just scrambling some old well-known threats.
You can read the rest of the news here: http://securityaffairs.co/wordpress/51714/malware/evading-antimalware.html