- May 3, 2011
- 3,893
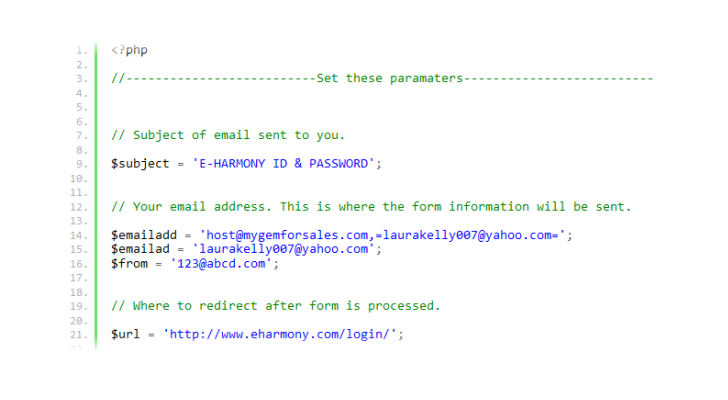
 - Excerpt of a malicious PHP script found by Netcraft
- Excerpt of a malicious PHP script found by NetcraftPopular online dating services are targeted by phishing campaigns, as anti-phishing company finds compromised website with scripts for stealing usernames and passwords.
Out of the 862 PHP malicious scripts discovered, only eight were aimed at banking credentials.
Among the dating websites in the cross-hair of the cybercriminals are match.com, Christian Mingle, PlentyOfFish, eHarmony, Chemistry.com, SeniorPeopleMeet, Zoosk, and Lavalife, says a report from Netcraft, a company that provides Internet security services, which include anti-fraud and anti-phishing.
The post says that the reason behind the phishing campaign could be to commit online dating fraud, an activity that can prove to be lucrative once the criminals gain the trust of the victim.
“Online dating fraud is often orchestrated by criminal gangs who use fake profiles to trick victims into developing long distance relationships. Once the fraudsters have gathered enough sympathy and trust from a victim, they will exploit this by claiming they need money to pay for travel costs, or to afford medical treatment for a family member,” says Paul Mutton of Netcraft.
“After the money has been stolen, the criminals will make up further reasons why they need more money. In some cases, the fraudsters blackmail their victim into sending money - if the victim has sent any explicit photos or videos to the criminals, they may threaten to send them to the victim's friends and family,” Mutton added.
Compromised paid accounts offer the fraudsters protection against being traced, as there is no financial transaction recorded through the website’s payment service.
The latest attacks detected by the company employ a phishing kit with PHP scripts; when credentials are obtained, they are sent to a number of email addresses, more than half being registered for Yahoo! Mail service.
Some of the scripts have been configured to steal log-in information for webmail services, too, the email accounts being used for fraudulent purposes.
The scripts in the phishing kits are similar in functionality and “simply collate a set of POST parameters into the body of an email message, and then send it to two or more email addresses. The subject of the email is modified to describe what type of credentials are in the email (e.g. ‘MATCH ID & PASSWORD’), and after the emails have been sent, the victim is redirected to an appropriate URL on the target website, such as http://www.match.com/login/login.aspx?lid=2,” explains Mutton.
The compromised servers hosting them does not display fraudulent content but accepts information from other sources, like a form hosted on a different website and the victim is then redirected to the legitimate location, without noticing the switch.
Source
