- Apr 25, 2013
- 5,355
Security experts at Zimperium firm revealed that LinkedIn users could be potentially vulnerable to Man-in-the-Middle attacks leveraging an SSL stripping.
A new research is scaring users of LinkedIn revealing that they could be potentially vulnerable to Man-in-the-Middle (MITM) attacks leveraging an SSL stripping. Despite the US security firm Zimperium reported the problem to LinkedIn more than a year ago, the security issue is still unresolved.
During the MITM attack, the attacker will strip all https:// requests to http:// in order to access the victim’s traffic in plain text and to operate without restriction on it.
Zimperium contacted LinkedIn six times over the last year, but the firm replied that it has already planned the deployment of SSL that will fix the problem. In the MITM attack scenario, hackers could extract LinkedIn credentials and other LinkedIn information (Email address, Read and Sent Messages, Connections “Who viewed my profile”), hijack sessions, and of course impersonate the user (Send invitations to connect, Edit the user’s profile, Edit job postings, Manage company pages).
The attacker would have the full control for the compromised profile, including admin rights to groups and company pages, the bad news is that the attack isn’t overly complex to a skilled attacker.
“Every single user we tested was vulnerable to this attack. In addition, this vulnerability doesn’t just exist when an attacker is on the same network as the target – if an attacker has already compromised a device, once that device enters a different network, the attacker can use the victim’s device to attack other users on the same network,” reported Zimperium in a blog post.
As explained by Zimperium every account is vulnerable even if it isn’t on the same network of the attacker, “the attacker can use the victim’s device to attack other users on the same network.“
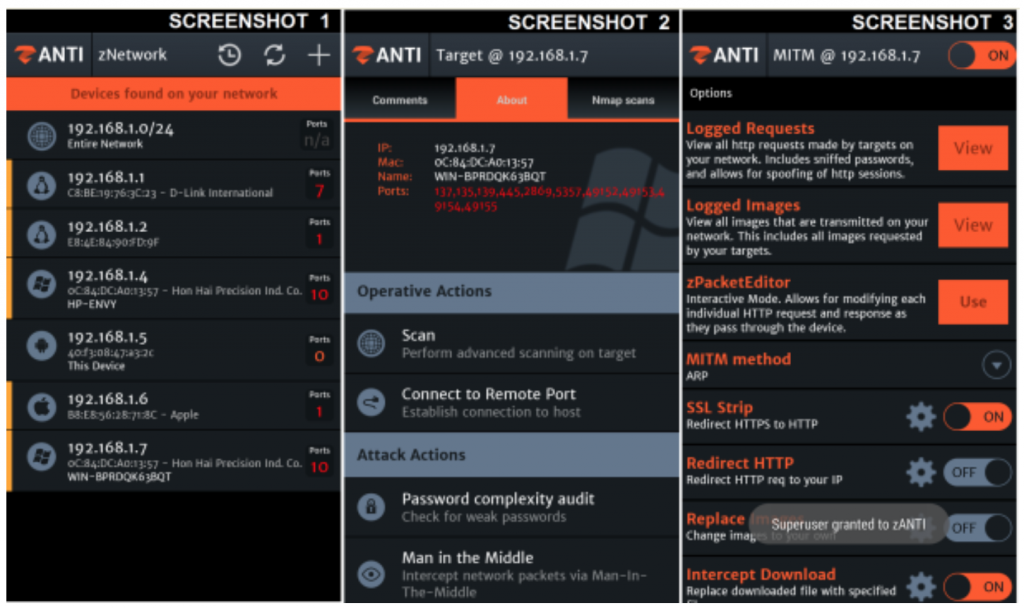
Zimperium provided a proof of concept to demonstrate the feasibility of the attack, its experts used their own tools and accounts, anyway on the market numerous software implements feature to conduct a MITM attack, a circumstance that is advantaged by the presence of the attacker on the same network segment of the victim.
LinkedIn has replied to the accusation with an official statement, reassuring its users saying that the security issue doesn’t impact all of its accounts, but only some of them.
“LinkedIn is committed to protecting the security of our members. In December 2013 we started transitioning the LinkedIn site to default HTTPS and just last week announced that we are serving all traffic to all users in USand EU by default over HTTPS. This issue does not impact the vast majority of LinkedIn members given our ongoing global release of HTTPS by default.”
The reply of Zimperium is that:
[there] “are still seeing many instances of this new setting not being enabled on existing or new LinkedIn accounts in the US and Europe.” “Our initial test suggests for existing accounts that deleting authentication cookies still resident in a user’s browser might fix this issue, however this has not been consistently the case.”
Full Article
A new research is scaring users of LinkedIn revealing that they could be potentially vulnerable to Man-in-the-Middle (MITM) attacks leveraging an SSL stripping. Despite the US security firm Zimperium reported the problem to LinkedIn more than a year ago, the security issue is still unresolved.
During the MITM attack, the attacker will strip all https:// requests to http:// in order to access the victim’s traffic in plain text and to operate without restriction on it.
Zimperium contacted LinkedIn six times over the last year, but the firm replied that it has already planned the deployment of SSL that will fix the problem. In the MITM attack scenario, hackers could extract LinkedIn credentials and other LinkedIn information (Email address, Read and Sent Messages, Connections “Who viewed my profile”), hijack sessions, and of course impersonate the user (Send invitations to connect, Edit the user’s profile, Edit job postings, Manage company pages).
The attacker would have the full control for the compromised profile, including admin rights to groups and company pages, the bad news is that the attack isn’t overly complex to a skilled attacker.
“Every single user we tested was vulnerable to this attack. In addition, this vulnerability doesn’t just exist when an attacker is on the same network as the target – if an attacker has already compromised a device, once that device enters a different network, the attacker can use the victim’s device to attack other users on the same network,” reported Zimperium in a blog post.
As explained by Zimperium every account is vulnerable even if it isn’t on the same network of the attacker, “the attacker can use the victim’s device to attack other users on the same network.“
Zimperium provided a proof of concept to demonstrate the feasibility of the attack, its experts used their own tools and accounts, anyway on the market numerous software implements feature to conduct a MITM attack, a circumstance that is advantaged by the presence of the attacker on the same network segment of the victim.

LinkedIn has replied to the accusation with an official statement, reassuring its users saying that the security issue doesn’t impact all of its accounts, but only some of them.
“LinkedIn is committed to protecting the security of our members. In December 2013 we started transitioning the LinkedIn site to default HTTPS and just last week announced that we are serving all traffic to all users in USand EU by default over HTTPS. This issue does not impact the vast majority of LinkedIn members given our ongoing global release of HTTPS by default.”
The reply of Zimperium is that:
[there] “are still seeing many instances of this new setting not being enabled on existing or new LinkedIn accounts in the US and Europe.” “Our initial test suggests for existing accounts that deleting authentication cookies still resident in a user’s browser might fix this issue, however this has not been consistently the case.”
Full Article
