- May 11, 2014
- 1,639
A new ransomware called Locker has been discovered that once installed lay dormant until midnight local time on May 25th when it would activate and encrypt your data files. Once your files were encrypted it would demand .1 bitcoins in order to decrypt your files. If payment was not made within 72 hours, the ransom price would then increase to 1 bitcoin. This ransomware is currently widespread with global targeting.
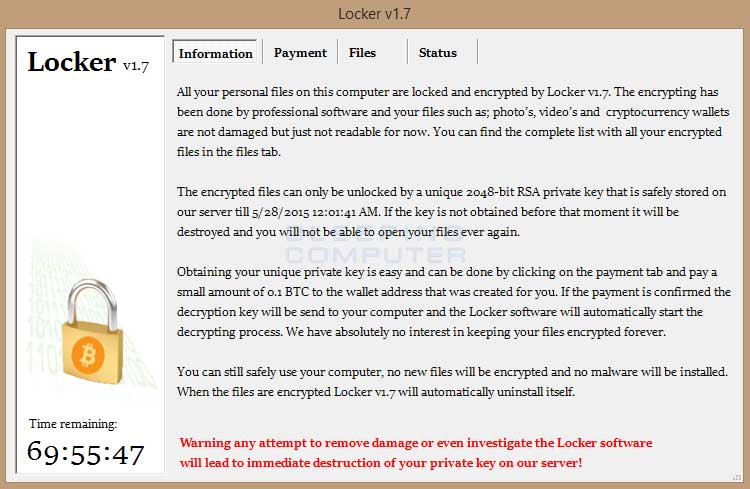
Main Locker screen
Locker appears to be installed via a dropper that creates a daisy-chain installation of various Windows services that ultimately launches the Locker screen. The main dropper will be installed in C:\Windows\Syswow64 as a random name such as twitslabiasends.exe. This file will then create the Steg service that uses the C:\ProgramData\Steg\steg.exe executable. This executable will then install Tor into C:\ProgramData\Tor and create another called service called LDR. The LDR service is associated with the C:\ProgramData\rkcl\ldr.exe and will ultimately launch the rkcl.exe program which displays the Locker interface. Finally the installation will also delete all Shadow Volume Copies so that you are unable to use them to restore your files. The command used to delete the shadow volume copies is:
vssadmin.exe delete shadows /for=C:/all /quiet
The main screen for the Locker ransomware will include a version number. This version number appears to be random with titles such as Locker v1.7, Locker v3.5.3, Locker V2.16, and Locker V5.52. The Locker screen is broken up into 4 different sections labeled Information, Payment, Files, and Status. The Information screen will display the ransom note and information on what has happened to the victim's data. The Payment screen will display the victims unique bitcoin address and information on how to make payment. The Files screen will load the list of files that have been encrypted and the Status screen will display payment status information. Screenshots of the Payment and Status screen can be seen below.
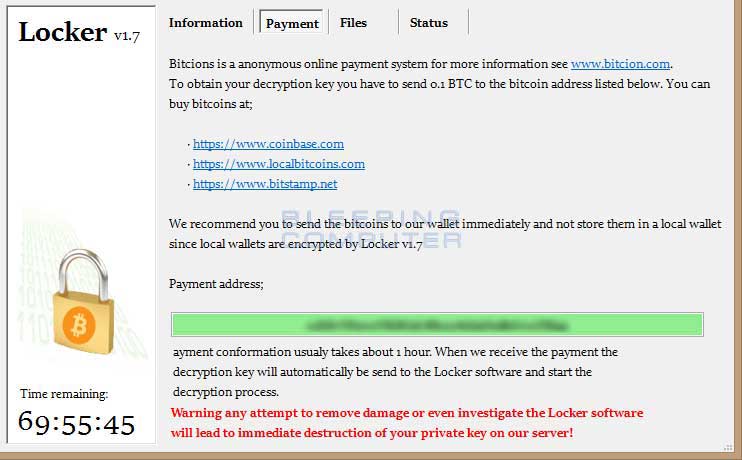
Locker Payment Page
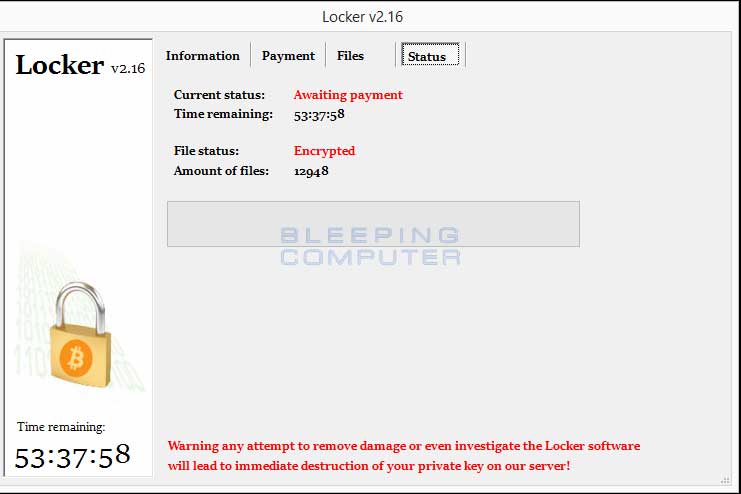
Locker Status Page
In the C:\ProgramData\rkcl folder there will be various files created. These files are:
Locker Ransomware Support Topic

Main Locker screen
Locker appears to be installed via a dropper that creates a daisy-chain installation of various Windows services that ultimately launches the Locker screen. The main dropper will be installed in C:\Windows\Syswow64 as a random name such as twitslabiasends.exe. This file will then create the Steg service that uses the C:\ProgramData\Steg\steg.exe executable. This executable will then install Tor into C:\ProgramData\Tor and create another called service called LDR. The LDR service is associated with the C:\ProgramData\rkcl\ldr.exe and will ultimately launch the rkcl.exe program which displays the Locker interface. Finally the installation will also delete all Shadow Volume Copies so that you are unable to use them to restore your files. The command used to delete the shadow volume copies is:
vssadmin.exe delete shadows /for=C:/all /quiet
The main screen for the Locker ransomware will include a version number. This version number appears to be random with titles such as Locker v1.7, Locker v3.5.3, Locker V2.16, and Locker V5.52. The Locker screen is broken up into 4 different sections labeled Information, Payment, Files, and Status. The Information screen will display the ransom note and information on what has happened to the victim's data. The Payment screen will display the victims unique bitcoin address and information on how to make payment. The Files screen will load the list of files that have been encrypted and the Status screen will display payment status information. Screenshots of the Payment and Status screen can be seen below.

Locker Payment Page

Locker Status Page
In the C:\ProgramData\rkcl folder there will be various files created. These files are:
- data.aa0 - This file contains a list of the encrypted files.
- data.aa1 - Unknown purpose
- data.aa6 - The victim's unique bitcoin address
- data.aa7 - An RSA key similar to:
Quote
<RSAKeyValue><Modulus>rvSUBZItCXDmeBBu01Imy811u41pOSTRDn9+6FpsEvXXfoBrcLgBd5ommgeT5jFRmY1/4vvsd+uXTUOG9FPBtbx1ySB9cv6/+5dU8v4SZTFIkCBIb5nXvYNzmm/lBB5OXOr6B8dkjyEr94LvUUg4B4XyFRjjjoXSUXX6ND0vbt1knN6/mBSIfkvv7XTlS5IBmbxB149t79mFcr9nu1tS9edI6s+sIUB14jFumf5xob1YG5UXOSntBDgkuIso+JXrXvB1ze4Bc7Ec1711Bmy7rfXScxpxXFb7rByZukBN5IomrY+9rTpyC4Df+pvJz/osBS0kSBS+BvIdETT/nKmIYm==<MSodulus><Exponent>ImIB</Exponent></RSAKeyValue>
- data.aa9 - Unknown purpose
- data.aa9 - The date the ransomware became active.
- data.aa11 - Unknown purpose
Locker Ransomware Support Topic

