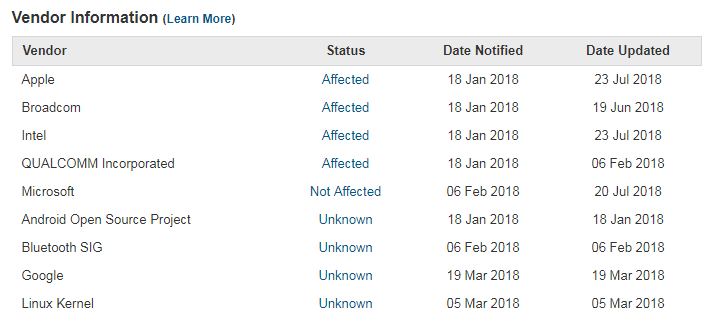
Some big vendors affected
Apple, Broadcom, Intel, and Qualcomm have confirmed that Bluetooth implementations and OS drivers are affected.
Apple and
Broadcom have deployed fixes for the bug, while the status of Intel and Qualcomm is unknown.
Microsoft said its devices are not affected. CERT/CC experts were not able to determine if Android, Google devices, or the Linux kernel are affected.
The Bluetooth Special Interest Group (SIG), the organization that oversees the development of Bluetooth standards, has issued a
statement in regards to the vulnerability.
For an attack to be successful, an attacking device would need to be within wireless range of two vulnerable Bluetooth devices that were going through a pairing procedure. The attacking device would need to intercept the public key exchange by blocking each transmission, sending an acknowledgment to the sending device, and then injecting the malicious packet to the receiving device within a narrow time window. If only one device had the vulnerability, the attack would not be successful.
The organization says it has now updated the official Bluetooth specification to require that all pairing devices validate all parameters used for key-based encrypted Bluetooth connections.
Researchers and Bluetooth SIG said they weren't aware of any in-the-wild attacks where this vulnerability might have been used.
The updates for CVE-2018-5383 should be expected as OS updates or driver updates (for desktops, laptops, and smartphones), or firmware updates (in the case of IoT/smart devices).