- Nov 10, 2017
- 3,250
Turns out Secure Boot is not secure
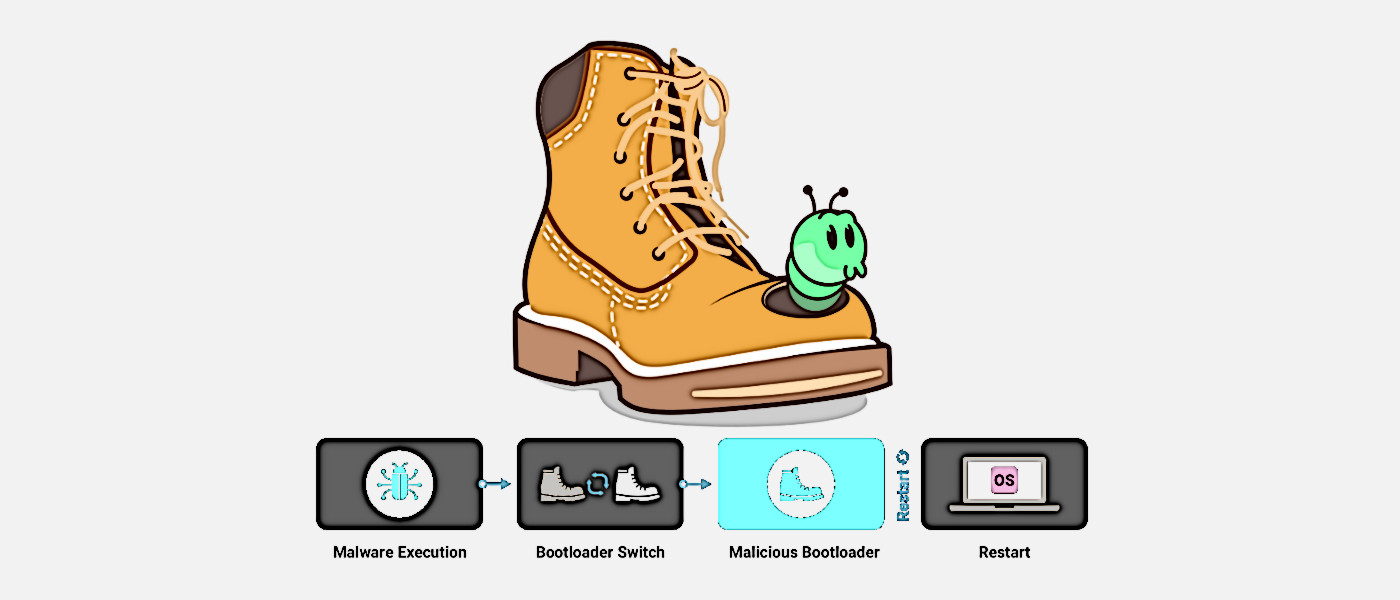
Eclypsium, a company that specializes in enterprise security solutions, revealed a new vulnerability that allows attackers to gain near-total control of WIndows or Linux systems. The company says that billions of devices are vulnerable, like systems ranging from laptops, desktop PCs, servers and workstations to other types of devices, like special-purpose equipment used in industrial, healthcare, financial, and other industries.
The attack exposes a vulnerability in the UEFI Secure Boot framework that normally prevents unauthorized access to the system during boot time. By compromising Secure Boot, attackers can then use malicious UEFI bootloaders to gain unfettered access and control of the system. Luckily, this attack requires elevated privileges to exploit, which means it would be hard for outside entities to attack a system without some level of insider knowledge or having already gained access to credentials through other means.